Query event log data with Operations Management Suite Search
Summary: This blog posts provides step-by-step instructions for querying Windows event logs from dozens of servers by using the Microsoft Operations Management Suite Search tool.
Good morning everyone. Ed Wilson here. I have spent much of the morning working on my calendar and arranging for a series of personal appearances that are coming up in the next several months. The Scripting Wife and I will be making a number of trips to speak at various user groups and conferences. Stay tuned for updates as the details are hammered out.
Today I want to continue my series about searching data with MS OMS.
Note This post is part of a seven part series about using MS OMS Search. The series includes:
- Easy Microsoft Operations Management Suite Search queries
- Accessing different data types in Microsoft OMS Search
- Filter data returned by Microsoft Operations Management Search
- Filter more data with Microsoft Operations Management Suite Search
- Query event log data with Operations Management Suite Search
- Use Microsoft Operations Management Suite search to track shutdown events
- Using Microsoft Operations Management Suite Search Strings
Query specific event logs with OMS
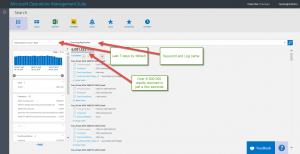
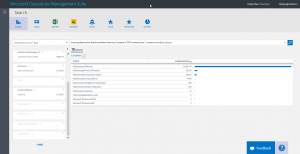
In my demo environment, I have access to more than sixty computers. Luckily, they have the #MSOMS agent installed, and so I can query from a specific event log from all of these computers rather quickly. To do this, all I need to do is to specify the EventLog keyword, and specify the log name. Here is an example query that returns data (from the last 7 days by default) from all the application event logs on all of the computers:
EventLog=Application
I can also use a colon for the same query:
EventLog:Application
The following screenshot shows the query and its output:
By default, the query uses AND. If I add a filter for EventLevelName (the property from the event log records that tells me the level, such as Information, Warning, or Error), I will get a filter that returns the records from the Application event log AND also has a Warning event level:
EventLog:Application EventLevelName=Warning
Note I could have also used a colon between EventLevelName and Warning: EventLog:Application EventLevelName:Warning. Personally, I do not like to use the colon because on my keyboard I have to hold down the Shift key to get a colon, but I do not need to hold the Shift key to get the equals sign, so it reduces the number of keystrokes by ½. In addition, in my mind, the equals sign is more readable than a colon.
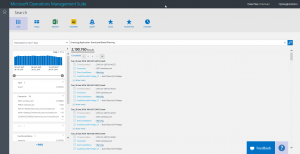
The command and the associated output are shown here:
Organize two million returned records
Now that I have found that I can easily find Warning records from all of the application logs from my servers, I need to be able to organize them into something that is easier to digest than two million random Warning records.
To do this, I want to pipe my results to the Measure keyword. (For more information about using the Measure keyword, refer to Filter more data with Microsoft Operations Management Suite Search.)
To me, it makes sense to display the number of warning messages (in the past 7 days) on a per computer basis. This can help me to narrow in on a particular computer that may be displaying an unusual number of Warning messages.
I pipe my results to the Measure command and I tell Measure to count() . I need to tell it what I want counted, and in this case, it is by Computer.
Note The word Computer is case sensitive here, and you will receive an error message if you use a lower-case C.
Here is the query and the output:
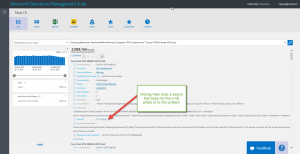
EventLog:Application EventLevelName:Warning | Measure count() by Computer
You can see from the output that I have 29 computers listed, but the Ex01.Contoso.Com computer has 2,188,413 Warning records. The next closest computer only has 1,344 Warning messages. So, I need to dive into the Warning records from Ex01 and see what is going on with that computer. All I need to do is add another AND clause to the query (remember that ANDs are automatic). I need to say that the Computer is equal to Ex01.Contoso.com:
EventLog:Application EventLevelName:Warning Computer="EX01.contoso.com"
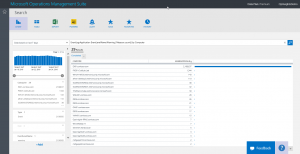
I expand one of the records so I can see how I want to further group the data:
The record that I examine is an Event ID 2112 from MSExchange ADAccess. It says something about not having permission to do something.
I decide that I want to see how often that event occurs. So I decide to measure and count by Source:
EventLog:Application EventLevelName:Warning Computer="EX01.contoso.com" | measure count() by Source
The returned results tell me that this event from the source of MSExchange ADAccess is indeed the major culprit:
In the following line, I filter only from these MSExchange ADAccess sourced events:
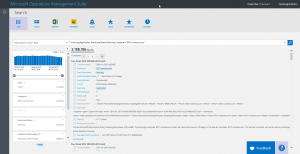
EventLog:Application EventLevelName:Warning Computer="EX01.contoso.com" Source="MSExchange ADAccess"
Here are the returned results:
I look at the results, and click View next to the event. It opens Search, and I find a KB article that tells me how to fix this problem. Sweet.
That is all I have for you today. Join me tomorrow when I’ll talk about more cool #MSOMS stuff.
I invite you to follow me on Twitter and the Microsoft OMS Facebook site. If you want to learn more about Windows PowerShell, visit the Hey, Scripting Guy! Blog. If you have any questions, send email to me at scripter@microsoft.com. I wish you a wonderful day, and I’ll see you tomorrow.
Ed Wilson
Microsoft Operations Management Team