Filter more data with Microsoft Operations Management Suite Search
Summary: Learn how to use the Microsoft Operations Management Suite Search filter tools to customize your returned data.
Good morning everyone. Ed Wilson here, and today I want to continue talking about using the Log Search feature of Microsoft Operations Management Suite.
Note This post is part of a seven part series about using MS OMS Search. The series includes:
- Easy Microsoft Operations Management Suite Search queries
- Accessing different data types in Microsoft OMS Search
- Filter data returned by Microsoft Operations Management Search
- Filter more data with Microsoft Operations Management Suite Search
- Query event log data with Operations Management Suite Search
- Use Microsoft Operations Management Suite search to track shutdown events
- Using Microsoft Operations Management Suite Search Strings
Search for more than one condition
A compound query is stand fare for SQL. Indeed, it is also rather routine when doing Windows PowerShell queries from various data sources. Often I want to know if one thing or if a different thing has occurred. When I am talking about one thing or a different thing, of course, I am talking about doing an OR type of query. To do an OR query using the Search tool in MS OMS, all I need to do is specify OR in my query. I do this before the pipe character.
For example, if I am interested in accounts that have been added to a security-enabled group, I might need to query for EventID 4728, EventID 4732, or event EventID 4756. All I need is one of these events to qualify for my query.
The first thing I need to do is to filter by the SecurityEvent data type. I talked about this in my second Search basics post, Searching for different types of data with MS OMS. The next thing I need to do is filter based on an EventID number. I talked about this in Filter data returned by Microsoft Operations Management Search.
So far, I have a search query that looks like this:
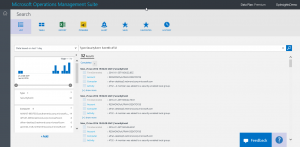
Type=SecurityEvent EventID=4732
As shown here, when I test it, it returns 32 security events:
Now, I want to add additional possible security events by using the OR operator. This is really easy to do using the MS OMS log search tool. All I do is use OR and the EventID= whatever. I come up with the following query:
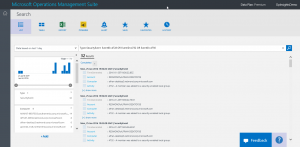
Type=SecurityEvent EventID=4728 OR EventID=4732 OR EventID=4756
Note I have written a lot of Hey, Scripting Guy! Blog posts about querying Security Event logs for various activities. These are a good source of specific event log IDs that would easily translate to #MSOMS SecurityEvent queries.
Group and count
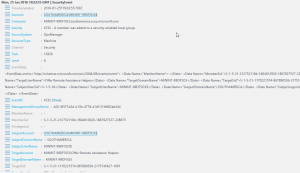
If I am going to group the events by a specific property, I need to know what properties are available. I can get this information by examining a single returned record, for example:
Based on the information I see in the record, I may want to know who is being added. So I want to use the Measure keyword to count by the SubjectAccount property. The Measure keyword goes after I have collected my security events and after the pipe character. I specify Count as my type of measuring, and I want to count the SubjectAccount property:
Type=SecurityEvent EventID=4728 OR EventID=4732 OR EventID=4756 | Measure Count() by SubjectAccount
The output is shown in the following image:
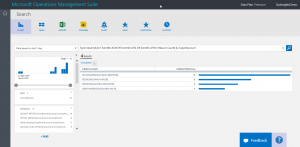
But I may want to know if a specific group is being targeted by all these additions. So I can change the query to TargetAccount. In fact, that is the only change I need to make. Here is the revised query:
Type=SecurityEvent EventID=4728 OR EventID=4732 OR EventID=4756 | Measure Count() by TargetAccount
Here is the query and the output:
That is all I have for you today. Join me tomorrow when I’ll talk about more cool MS OMS stuff.
I invite you to follow me on Twitter and the Microsoft OMS Facebook site. If you want to learn more about Windows PowerShell, visit the Hey, Scripting Guy! Blog. If you have any questions, send email to me at scripter@microsoft.com. I wish you a wonderful day, and I’ll see you tomorrow.
Ed Wilson
Microsoft Operations Management Team