UR4 for SCOM 2016 – Step by Step

KB Article for OpsMgr: https://support.microsoft.com/en-us/help/4024941/update-rollup-4-for-system-center-2016-operations-manager
Download catalog site: https://www.catalog.update.microsoft.com/Search.aspx?q=4024941
Updated UNIX/Linux Management Packs: https://www.microsoft.com/en-us/download/details.aspx?id=29696
Recommended hotfix page: https://blogs.technet.microsoft.com/kevinholman/2009/01/27/which-hotfixes-should-i-apply/
NOTE: I get this question every time we release an update rollup: ALL SCOM Update Rollups are CUMULATIVE. This means you do not need to apply them in order, you can always just apply the latest update. If you have deployed SCOM 2016 and never applied an update rollup – you can go straight to the latest one available.
There is some conflicting documentation with the above statement in the UR4 KB article, so I will try and explain. The KB article states that you must apply UR2 before UR4. This is misleading. UR2 fixed a bug in the update process to allow any subsequent UR (post UR2) to have the ability to be uninstalled. This bug was first fixed in UR2. So if you want the ABILITY to uninstall UR4, you should apply UR2 or UR3 first. However, once you apply UR4, you have the fix, and any subsequent UR’s will be able to be uninstalled. In my opinion, there is very little to no value of applying UR2 first. Simply apply UR4 to whatever version you are at (since it IS cumulative), and any subsequent Update Rollups will have the ability to be uninstalled.
Ok, now that’s clear as mud, lets get rolling:
Key fixes:
Adds support for TLS 1.2.
- For more information about how to set up, configure, and run your environment with TLS 1.2, see the following article in the Microsoft Knowledge Base: 4051111 TLS 1.2 Protocol Support Deployment Guide for System Center 2016
APM Crash fix: This update resolves an issue that causes a crash of IIS application pools that are running under CLR 2.0 when the APM feature is installed on the server as part of SCOM Agent. The code now uses appropriate memory instructions, based on the CLR version.
Fix: Addresses an issue in which the APM AppDiagnostics console fails to create a Problem Management rule due to a FormatException. The appropriate string is now used for formatting, and the Problem Management wizard is able to run without issues.
Fix: When a log file is being monitored by SCOM, Monagent locks the file and won't allow it to be renamed.
Fix: Failure of GetOpsMgrDBWatcherDiscovery.ps1 script causes the Monitoring Host to crash.
Fix: WMI Health monitor doesn't work if WINRM is configured to use https only. (servers configured with HTTP SPN’s)
WMI Health monitor doesn't work if SPN https://servername is set to a user account. (servers configured with HTTP SPN’s)
Fix: SCOMpercentageCPUTimeCounter.ps1 script generates WMI errors that are caused by Service Principle Name (SPN) configuration issues. (servers configured with HTTP SPN’s)
Product knowledge of "Windows Cluster Service Discovery" includes an incorrect reference to "Windows NT."
After a network outage, the management server does not reconnect to the gateway server if the gateway server was installed with the /ManagementServerInitiatesConnection=True option.
A configuration change to the network device triggers a rediscover of the device, and this process changes the SNMP agent address.
The UseMIAPI registry subkey prevents collection of custom performance rules data for all Linux servers.
Lets get started.
From reading the KB article – the order of operations is:
- Install the update rollup package on the following server infrastructure:
- Management server or servers
- Audit Collection Server (ACS)
- Web Console server role computers
- Gateway
- Operations Console role computers
- Apply SQL scripts.
- Manually import the management packs.
- Apply Agent Updates
- Update Nano Agents
- Update Unix/Linux MP’s and Agents
1. Management Servers

It doesn’t matter which management server I start with. I simply make sure I only patch one management server at a time to allow for agent failover without overloading any single management server.
I can apply this update manually via the MSP files, or I can use Windows Update. I have 2 management servers, so I will demonstrate both. I will do the first management server manually. This management server holds 3 roles, and each must be patched: Management Server, Web Console, and Console.
The first thing I do when I download the updates from the catalog, is copy the cab files for my language to a single location, and then extract the contents
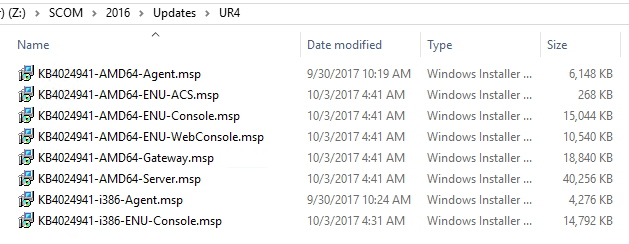
Once I have the MSP files, I am ready to start applying the update to each server by role.
***Note: You MUST log on to each server role as a Local Administrator, SCOM Admin, AND your account must also have System Administrator role to the SQL database instances that host your OpsMgr databases.
My first server is a Management Server, and the Web Console, and has the OpsMgr console installed, so I copy those update files locally, and execute them per the KB, from an elevated command prompt:
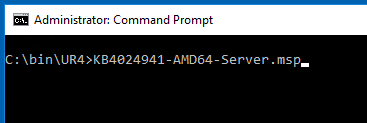
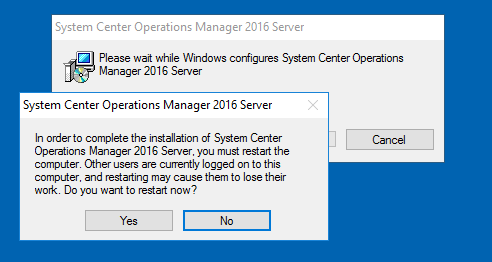
This launches a quick UI which applies the update. It will bounce the SCOM services as well. The update usually does not provide any feedback that it had success or failure…. but I did get a reboot prompt. You can choose “No” and then reboot after applying all the SCOM role updates.
You can check the application log for the MsiInstaller events to show completion:
Log Name: Application
Source: MsiInstaller
Event ID: 1036
Description:
Windows Installer installed an update. Product Name: System Center Operations Manager 2016 Server. Product Version: 7.2.11719.0. Product Language: 1033. Manufacturer: Microsoft Corporation. Update Name: System Center 2016 Operations Manager Update Rollup 4 Patch. Installation success or error status: 0.
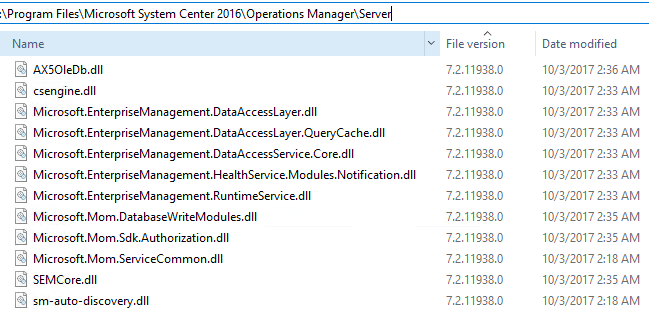
You can also spot check a couple DLL files for the file version attribute.
Next up – run the Web Console update:
This runs much faster. A quick file spot check:
Lastly – install the Console Update (make sure your console is closed):
A quick file spot check:
Or help/about in the console:
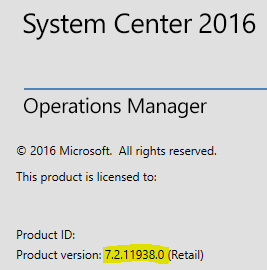
Additional Management Servers:

Apply the UR updates for Server, Web Console, and Console roles as needed for all additional management servers. You may also use Windows Update.
Updating ACS (Audit Collection Services)

One of my management servers is also my ACS Audit Collection Server role. I will apply the update for that.
From an elevated command prompt:
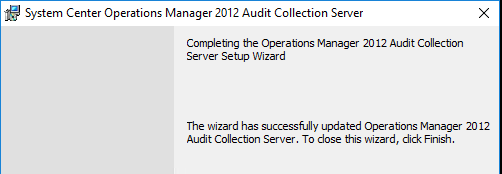
Note the above image states “Operations Manager 2012”. This is a known issue documented in the KB article.
Updated files:
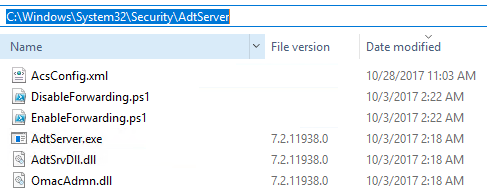
Updating Gateways:

Generally I can use Windows Update or manual installation. I will proceed with manual:
The update launches a UI and quickly finishes.
Then I will spot check the DLL’s:
I can also spot-check the \AgentManagement folder, and make sure my agent update files are dropped here correctly:
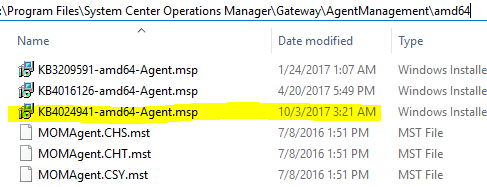
***NOTE: You can delete any older UR update files from the \AgentManagement directories. The UR’s do not clean these up and they provide no purpose for being present any longer.
I could also apply the GW update via Windows Update.
2. Apply the SQL Scripts

***Note – this update SQL script did NOT change from UR3 to UR4. If you had previously applied this file in UR3, you may skip this step. However, if you are unsure, you may always re-apply it. Reapplication will never hurt.
In the path on your management servers, where you installed/extracted the update, there is ONE SQL script file:
%SystemDrive%\Program Files\Microsoft System Center 2016\Operations Manager\Server\SQL Script for Update Rollups
(note – your path may vary slightly depending on if you have an upgraded environment or clean install)
Next – let’s run the script to update the OperationsManager (Operations) database. Open a SQL management studio query window, connect it to your Operations Manager database, and then open the script file (update_rollup_mom_db.sql). Make sure it is pointing to your OperationsManager database, then execute the script.
You should run this script with each UR, even if you ran this on a previous UR. The script body can change so as a best practice always re-run this.
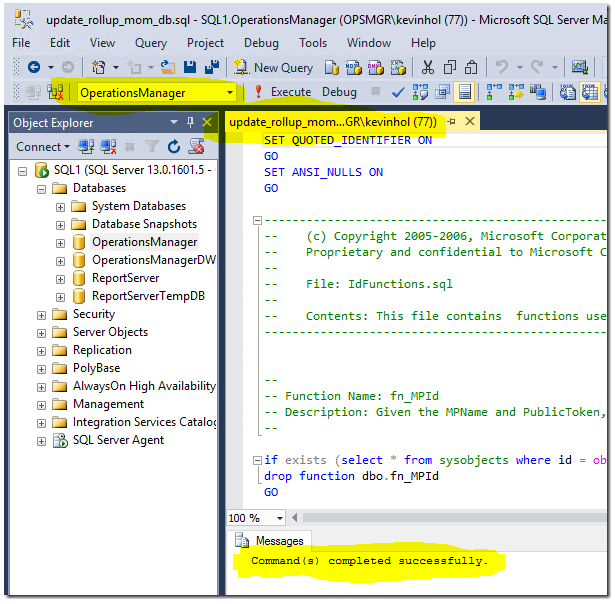
Click the “Execute” button in SQL mgmt. studio. The execution could take a considerable amount of time and you might see a spike in processor utilization on your SQL database server during this operation.
I have had customers state this takes from a few minutes to as long as an hour. In MOST cases – you will need to shut down the SDK, Config, and Monitoring Agent (healthservice) on ALL your management servers in order for this to be able to run with success.
You will see the following (or similar) output:
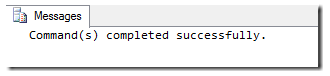
IF YOU GET AN ERROR – STOP! Do not continue. Try re-running the script several times until it completes without errors. In a production environment with lots of activity, you will almost certainly have to shut down the services (sdk, config, and healthservice) on your management servers, to break their connection to the databases, to get a successful run.
3. Manually import the management packs

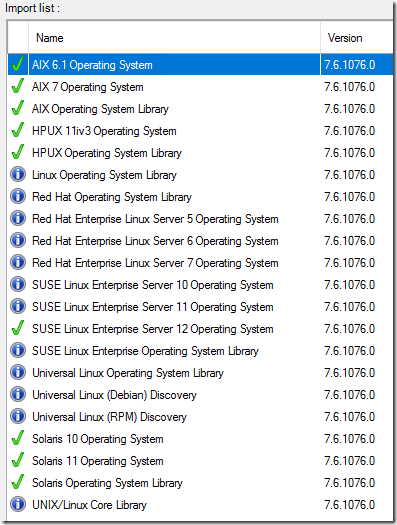
There are 36 management packs in this update! Most of these we don’t need – so read carefully.
The path for these is on your management server, after you have installed the “Server” update:
\Program Files\Microsoft System Center 2016\Operations Manager\Server\Management Packs for Update Rollups
However, the majority of them are Advisor/OMS, and language specific. Only import the ones you need, and that are correct for your language.
This is the initial import list:
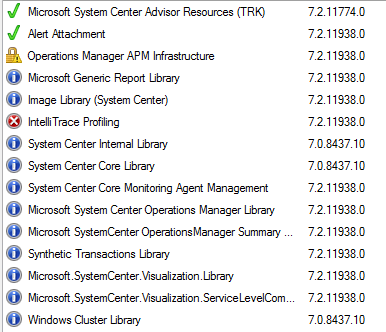
What NOT to import:
The Advisor MP’s are only needed if you are using Microsoft Operations Management Suite cloud service, (Previously known as Advisor, and Operations Insights) and have your on premise SCOM environment connected to the cloud service.
DON’T import ALL the languages – ONLY ENU, or any other languages you might require.
The Alert Attachment MP update is only needed if you are already using that MP for very specific other MP’s that depend on it (rare)
The IntelliTrace Profiling MP requires IIS MP’s and is only used if you want this feature in conjunction with APM.
So I remove what I don’t want or need – and I have this:
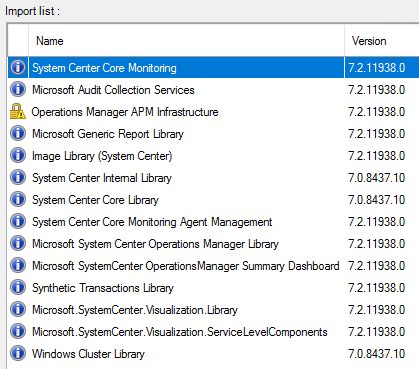
#Note: If the “Install” button is greyed out – this means you might already have one or move of these MP’s with the same version installed. In my case, I had already applied an out of band MP hotfix for “System Center Internal Library” version 7.0.8437.10, so I had to remove that to continue. Only do this if it is blocking you from continuing.
4. Update Agents

Agents should be placed into pending actions by this update for any agent that was not manually installed (remotely manageable = yes):
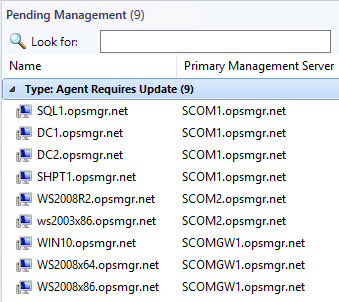
If your agents are not placed into pending management – this is generally caused by not running the update from an elevated command prompt, or having manually installed agents which will not be placed into pending by design, OR if you use Windows Update to apply the update rollup for the Server role patch.
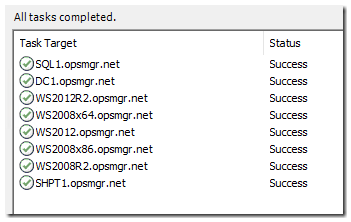
You can approve these – which will result in a success message once complete:
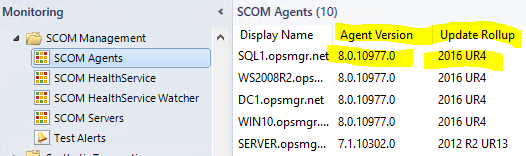
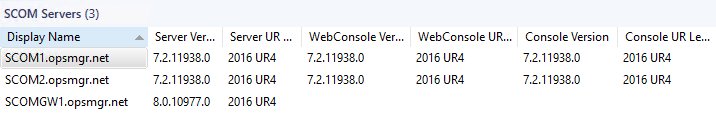
You normally could verify the PatchLevel by going into the console and opening the view at: Monitoring > Operations Manager > Agent Details > Agents by Version
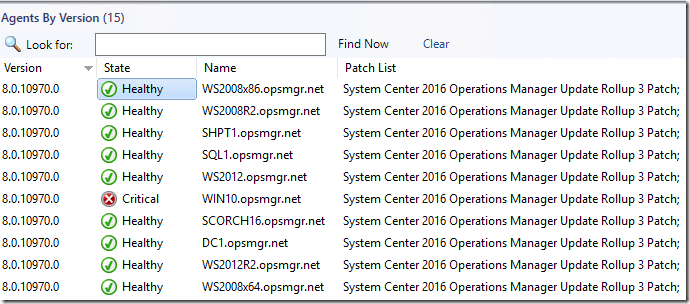
HOWEVER – due to a bug in UR4 agent patch – it is still reporting as UR3. ![]()
I *strongly* recommend you take a look at this community MP, which helps see the “REAL” agent number in the “Agent Managed” view console:
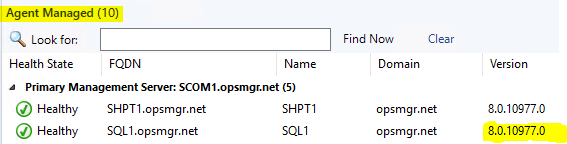
And my SCOM Management Group Management mp (updated for UR4), which will help show you REAL UR levels based on a better discovery. This has long been a pain point in SCOM:
5. Update UNIX/Linux MPs and Agents

The UNIX/Linux MP’s and agents at the time of this article publishing have not changed since SCOM 2016UR3 was released.
You can get the current Unix/Linux MP updates here: https://www.microsoft.com/en-us/download/details.aspx?id=29696
The current version of these MP’s for SCOM 2016 UR4 is 7.6.1076.0 – and includes agents with version 1.6.2-339
Make sure you download the correct version for your SCOM deployment:
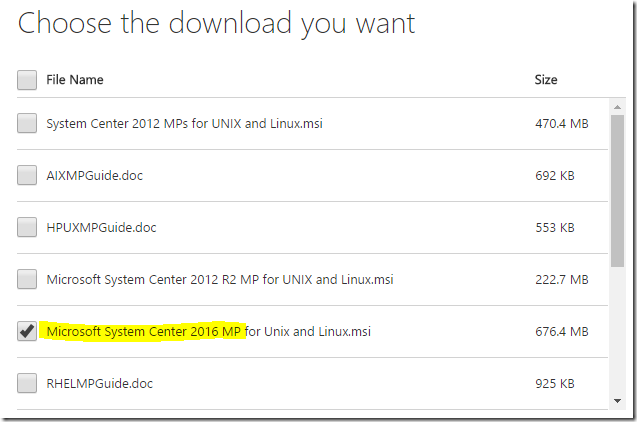
Download, extract, and import ONLY the updated Linux/UNIX MP’s that are relevant to the OS versions that you want to monitor:
This will take a considerable amount of time to import, and consume a lot of CPU on the management servers and SQL server until complete.
Once it has completed, you will need to restart the Healthservice (Microsoft Monitoring Agent) on each management server, in order to get them to update their agent files at \Program Files\Microsoft System Center 2016\Operations Manager\Server\AgentManagement\UnixAgents
You should see the new files dropped with new timestamps:
Now you can deploy the agent updates:
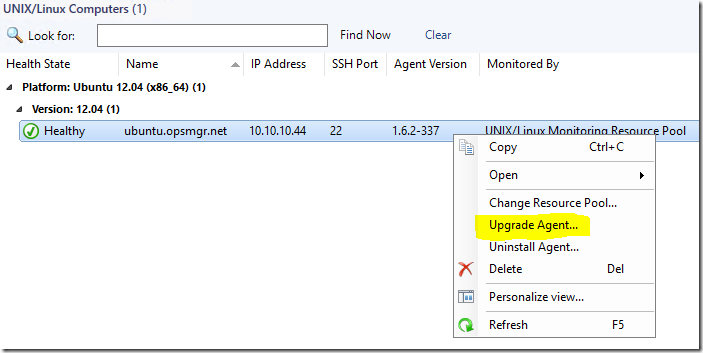
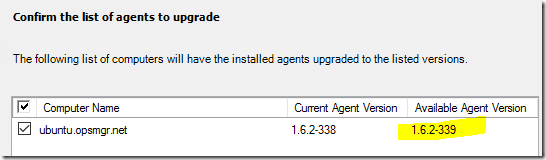
Next – you decide if you want to input credentials for the SSH connection and upgrade, or if you have existing RunAs accounts that are set up to do the job (Agent Maintenance/SSH Account)
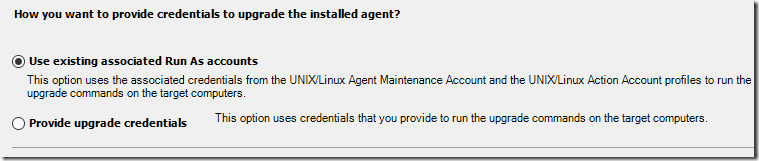
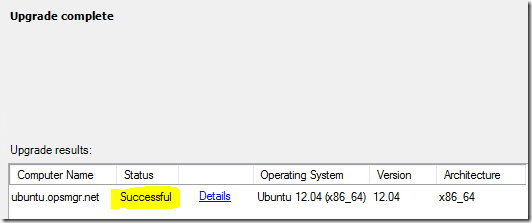
If you have any issues, make sure your SUDOERS file has the correct information pertaining to agent upgrade:
https://blogs.technet.microsoft.com/kevinholman/2016/11/11/monitoring-unixlinux-with-opsmgr-2016/
6. Update the remaining deployed consoles

This is an important step. I have consoles deployed around my infrastructure – on my Orchestrator server, SCVMM server, on my personal workstation, on all the other SCOM admins on my team, on a Terminal Server we use as a tools machine, etc. These should all get the matching update version.
Review:

Now at this point, we would check the OpsMgr event logs on our management servers, check for any new or strange alerts coming in, and ensure that there are no issues after the update.
Known Issues:
1. The ACS update shows “Operations Manager 2012” in the UI but is actually for SCOM 2016.
2. The Patchlist for agents mistakenly shows UR3, and was not updated for UR4. This can be worked around by importing my “Agent Version” and “SCOM Management” mp’s.
3. The Web Console is broken for any Silverlight dashboards. When you view a Silverlight Dashboard, you are prompted to “Configure” but even when you configure it, you are prompted over and over again. This is because the certificate being published in the utility is not correct for the version hosted on the Web Console server. You can follow the steps in the UR4 KB article to resolve the issue.