Using Search in Security Center to find Indicators of Compromise
Indicators of Compromise (IoC) are individually-known malicious events that indicate that a network, or a computer has already been breached. You can find a lot of IoC at OpenIOC (www.openioc.org), such as the Zeus IoC. In some circumstances, the IoCs will indicate the existence of a particular file in the system, or the execution of a particular command. For example, one of the WannaCry IoC is the presence of the following files in the system:
- %SystemRoot%\mssecsvc.exe
- %SystemRoot%\tasksche.exe
- %SystemRoot%\qeriuwjhrf
- wnry
- wnry
- wnry
- wnry
- wnry
- wnry
- wnry
- exe
- exe
- eky
- res
- pky
- @WanaDecryptor@.exe
- @Please_Read_Me@.txt
- vbs
- @WanaDecryptor@.exe.lnk
- @WanaDecryptor@.bmp
- bat
- exe
- exe
- Files with ".wnry" extension
- Files with ".WNCRY" extension
Source: WannaCrypt ransomware worm targets out-of-date systems
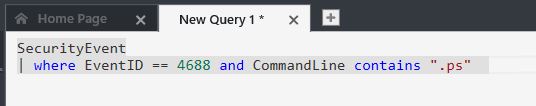
If you are using Azure Security Center, chances are that Security Center will catch a compromised system before you do. Such as when Petya outbreak happened, and Security Center was able to identify a compromised system just in a few hours (see more info about that here). But, if you still need to perform an investigation to look for compromised systems, you can use the Search capability in Security Center. You can start by searching for Event ID 4688, which is created when a new process is created in Windows (7 and beyond). In addition to that, you can also specify the file created by the malware that you are hunting (based on the info that you gather regarding's the malware IoC). For the purpose of this example, I’m going to search for a command line that contains a PowerShell Script, as shown below:
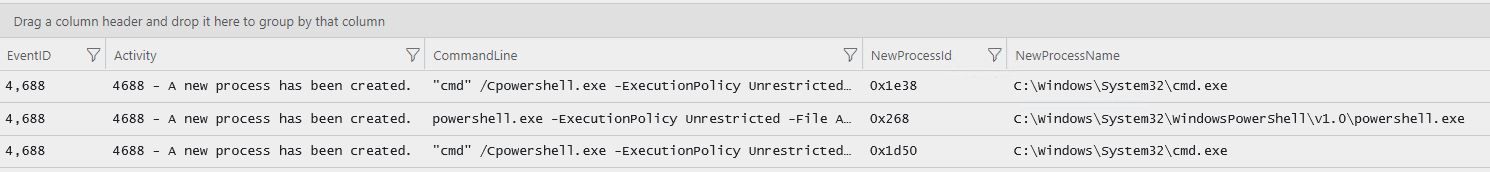
Here it is the result of this query:
Notice that we have the EventID, the description of the event, the command line, the ProcessID, and the process’s path. Just here you have a good amount of information to continue your research on the target system, and if you were searching precisely for the file created by the malware, you could see it here (assuming the file was executed at some point).