Testing Azure Security Center Detections Capabilities
When you first onboard your VMs/Computers in Azure Security Center, and the Microsoft Monitoring Agent is fully installed in the target systems, you may see some security recommendations for your workloads. This initial security assessment is very important, and usually it doesn’t take long for Security Center to provide a good picture of how secure your resources are.
The same doesn’t happen with Security Alerts, in other words, you may see some alerts, or you may not see anything. One way that you can validate the alerts is by using the procedures documented in the Alerts Validation in Azure Security Center article. These procedures will create a test alert, and you can see how an alert looks like. 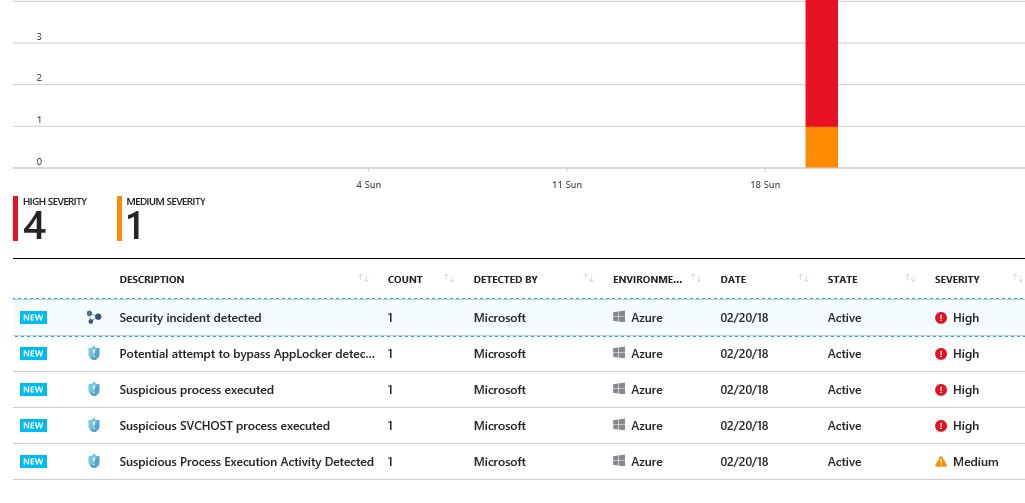
In some situations, you may want to go one step further, and try to pentest your own VMs/computers by simulating an attack. Today we released the Azure Security Center Playbook: Security Alerts, which will help you with that. The goal of this document is to provide validation steps to simulate attacks in VMs/Computers monitored by Azure Security Center (“Security Center”). You should use the steps described in this document in a lab environment, with the purpose to better understand the detection capabilities available in Security Center.