TMG Beta 3 Brings SSTP Capability
Now that TMG Beta 3 is released you can enjoy the best of both words for VPN access. In the past I was questioned about SSTP on ISA Server 2006 since Windows Server 2008 was capable to do it. The sad answer was that ISA Server 2006 didn’t have this feature built in. But now you can use TMG and select SSTP the same way as another protocol as shown in Figure 1:
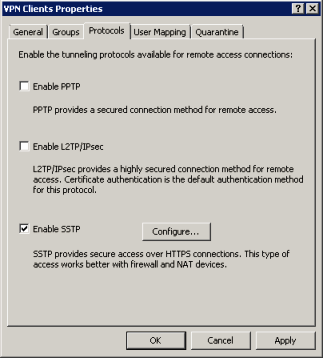
Figure 1 – SSTP available in TMG Console.
When configuring SSTP on TMG you will need to carefully plan:
· Web Listener that will be used by SSTP.
· Certificate that is going to be bound to the Web Listener.
Besides that you will need Windows Vista with SP1 on the client workstation to test this new feature.
Troubleshooting Client Access
Since I’m working remotely some these days I was able to reproduce some of the nice errors that I didn’t have when I was in my home lab. Today for example I got the following error when I was trying to connect from my laptop:
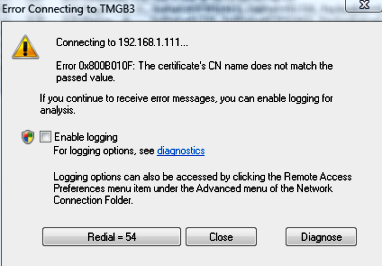
Figure 2 – First error due the cert name.
That was pretty self explanatory, but just to confirm the name that I used to issue the certificate I got a netmon trace and got the subject name:
SSL: Server Hello. Certificate. Server Hello Done.
Seq=1878717387 - 1878718743, Ack=2650000305, Win=256 (scale factor 0x8) = 65536
- Ssl: Server Hello. Certificate. Server Hello Done.
- TlsRecordLayer:
ContentType: HandShake
+ Version: TLS 1.0
Length: 1351 (0x547)
- SSLHandshake: SSL HandShake TLS 1.0 Server Hello Done(0x0E)
HandShakeType: ServerHello(0x02)
Length: 70 (0x46)
+ ServerHello: 0x1
HandShakeType: Certificate(0x0B)
Length: 1269 (0x4F5)
- Cert: 0x1
CertOffset: 1266 (0x4F2)
- Certificates:
CertificateLength: 1263 (0x4EF)
- X509Cert: Issuer: contoso-DC01-CA,contoso,com, Subject: vpn.contoso.com,IT,Contoso,Dallas,Texas
+ SequenceHeader:
- TbsCertificate: Issuer: contoso-DC01-CA,contoso,com, Subject: vpn.contoso.com,IT,Contoso,Dallas,Texas
+ SequenceHeader:
+ Tag0:
+ Version: v3 (2)
+ SerialNumber: 0x6168a464000000000002
+ Signature: Sha1WithRSAEncryption (1.2.840.113549.1.1.5)
+ Issuer: contoso-DC01-CA,contoso,com
+ Validity: From: 06/15/09 21:03:46 UTC To: 06/15/10 21:13:46 UTC
+ Subject: vpn.contoso.com,IT,Contoso,Dallas,Texas
+ SubjectPublicKeyInfo: RsaEncryption (1.2.840.113549.1.1.1)
+ Tag3:
+ Extensions:
+ SignatureAlgorithm: Sha1WithRSAEncryption (1.2.840.113549.1.1.5)
+ Signature:
HandShakeType: Server Hello Done(0x0E)
Length: 0 (0x0)
To quick fix this I edited my host file and created a manual entry there. But then right after that I got:
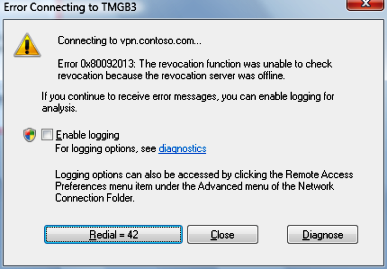
Figure 3 – Now is the CRL.
Looking to the properties of the certificate it was possible to see that the CRL was poiting to my internal CA:
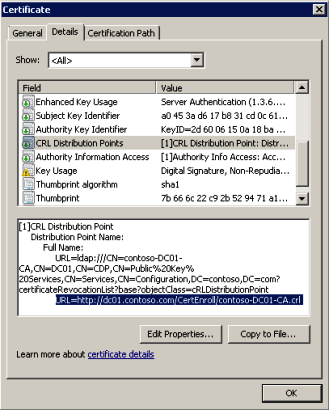
Figure 4 – The CRL for my internal CA.
To resolve this I created a web publishing rule to publish my CRL and after that all worked fine.
Additional Resources
While testing those settings I got some great links from the RRAS team (which is the component that TMG uses for VPN capability). Check it out the links below:
https://blogs.technet.com/rrasblog/archive/2007/01/17/sstp-faq-part-2-client-specific.aspx
https://blogs.technet.com/rrasblog/archive/2007/01/25/sstp-faq-part-3-server-specific.aspx
You might be wondering: how did you get access to those things if you were unable to establish the VPN connection? The answer is: through my backup PPTP connection :)