Is Firewall Service silent quitting or gracefully shutting down?
Introduction
First let’s understand what silent quits means:
When a silent exit occurs, the JIT debugger is never invoked because the process itself asked to be terminated. For example, two Win32 Application Programming Interface (API) functions that perform this action are TerminateProcess and ExitProcess .
From: https://support.microsoft.com/kb/329629
Note: Although this article is for Exchange these functions are Windows (Win32) related.
What about graceful shutdown, what is that? That’s simple: a service received an expected command to gracefully stop.
The Scenario
The scenario of this article was based on a real case where customer had to manually start Firewall Service every day, it was “apparently” quitting every night. The problem with a silent quitting is that debugger will not catch; therefore there will be no dump file to analyze. Even knowing that we tried to get a dump and of course the result was a 1st chance exception dump, no second chance. Therefore we got useless data.
Moving Forward
After researching more and more we found out that Telephony Service was set to disable and ISA Server Control depends on Remote Access Connection Manager that depends on Telephony Service:
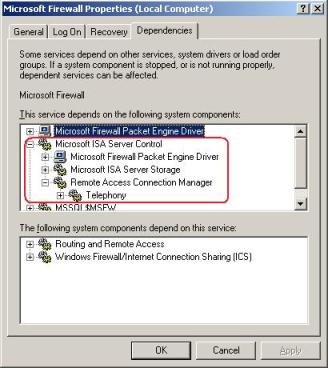
Figure 1 – ISA Server Control Dependencies.
Looking the System Log, there following sequence of events were showing up:
Event Type: Information
Event Source: Service Control Manager
Event Category: None
Event ID: 7040
Date: 2/19/2009
Time: 10:09:05 PM
User: NT AUTHORITY\SYSTEM
Computer: ISASRVSTD
Description:
The start type of the Telephony service was changed from demand start to disabled.
Event Type: Information
Event Source: Service Control Manager
Event Category: None
Event ID: 7035
Date: 2/19/2009
Time: 10:09:06 PM
User: NT AUTHORITY\SYSTEM
Computer: ISASRVSTD
Description:
The Microsoft Firewall service was successfully sent a stop control.
Event Type: Information
Event Source: Service Control Manager
Event Category: None
Event ID: 7036
Date: 2/19/2009
Time: 10:09:16 PM
User: N/A
Computer: ISASRVSTD
Description:
The Microsoft Firewall service entered the stopped state.
Event Type: Information
Event Source: Service Control Manager
Event Category: None
Event ID: 7035
Date: 2/19/2009
Time: 10:09:17 PM
User: NT AUTHORITY\SYSTEM
Computer: ISASRVSTD
Description:
The Microsoft ISA Server Control service was successfully sent a stop control.
Event Type: Information
Event Source: Service Control Manager
Event Category: None
Event ID: 7036
Date: 2/19/2009
Time: 10:09:17 PM
User: N/A
Computer: ISASRVSTD
Description:
The Microsoft ISA Server Control service entered the stopped state.
Event Type: Information
Event Source: Service Control Manager
Event Category: None
Event ID: 7035
Date: 2/19/2009
Time: 10:09:18 PM
User: NT AUTHORITY\SYSTEM
Computer: ISASRVSTD
Description:
The Remote Access Connection Manager service was successfully sent a stop control.
In the application log we got the prove that this was not a silent exit, it was actually a graceful shutdown:
Event Type: Information
Event Source: Microsoft ISA Server Control
Event Category: None
Event ID: 14181
Date: 2/19/2009
Time: 10:09:16 PM
User: N/A
Computer: ISASRVSTD
Description:
The ISA Server Control service was stopped gracefully.
Event Type: Information
Event Source: Microsoft Firewall
Event Category: None
Event ID: 14182
Date: 2/19/2009
Time: 10:09:05 PM
User: N/A
Computer: ISASRVSTD
Description:
The Firewall service was stopped gracefully.
Now What?
If those services are stopping every night and the administrator needs to manually start those, this leads to a conclusion that something (a process) is stopping it. For a domain joined ISA the first thing you shoul check is Group Policy. A simple thing that can be done without impact the production just to check if ISA Server is receiving any policy is run the command RSOP.MSC. The result for this case was shown in Figure 2:
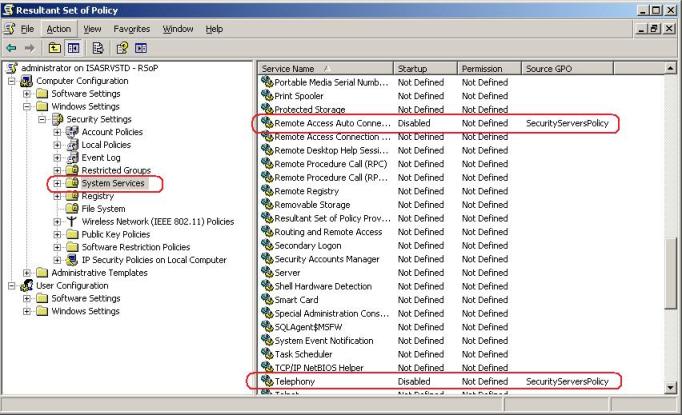
Figure 2 – RSOP.MSC result.
Bingo !!! Now everything makes sense. What was happen here was that ISA Server was inside of an OU that has a policy which was disabling those services. To fix that we created a new OU, moved ISA Server to this new OU and block inheritance in this OU.
Conclusion
Sometimes IT administrators using their best of intention disable some services that are considered not necessary from a Windows perspective (attempting to hardening). However, for ISA Server this needs to be carefully done since it can stop Firewall Service which will cause downtime in your Internet access. Before do this, review the article below that has a list of services that ISA Server depends on: