Auditing a DNS Zone
1. Introduction
One of the main aspects of security is the maintenance and to do that correctly the administrator needs to be able to track changes that are done in the environment. There are a lot of challenges on this area and one of the biggest challenge is to log what needs to be logged without overwhelm the server.
When I was working in the platforms team I remember that I received a call from a customer saying that he wants to know who deleted a record on his DNS Zone. First question was: do you have an audit policy for DNS enable? He was like: what is that? After review his environment I saw that the auditing was enabled, but not for the Active Directory Objects (his DNS Zone was integrated to AD).
This post will walk through the Auditing configuration of a DNS Zone (AD Integrated) on Windows Server 2003.
2. Preparing the Environment
There are three steps to prepare the environment:
· Verify if the Audit Policy called Audit Directory Service Access is enabled and what is the setting.
· Enabled the Auditing on the DNZ Zone that you want to audit.
· Use the Event Viewer to find out which object of modified (in this case the example will be an object deletion).
3. Configuring the Audit Policy
Open the Default Domain Controllers Policy, and check if the policy highlighted below is selected just like that:
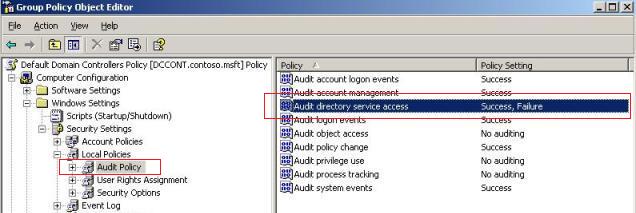
Figure 1 – Configuring Upload and Download Policy.
In my case I changed to audit Success and Failure, but the final configuration will be according to your needs.
4. Configuring the DNS Zone
Now that we have enabled the Audit Policy to all Domain Controller in the domain, we need to change the DNS Zone. To do that follow the steps below:
1) Open ADSIEdit (Start / Run / ADSIEDIT.msc)
2) Right click in the ADSI Edit and click in Connect To…
3) In the Connection Settings window, configure just like show below:
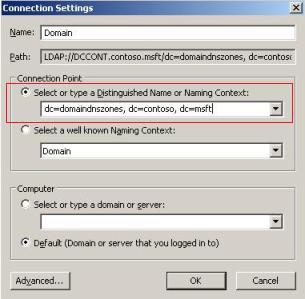
Figure 2 – Connection Setting.
Note: Change the dc= to reflect your domain name.
4) After that click OK.
5) Now expand the container until you get to the same node as show below:
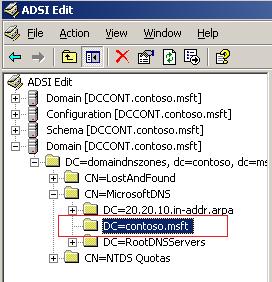
Figure 3 – Configuring the Zone.
5) Right click in the name of the zone located under CN=MicrosoftDNS and click in Properties.
6) Click in Security and then Advanced.
7) Click in Auditing and click in Add.
8) Type Everyone and click OK. Add the following type of access:
· Write All Properties
· Delete
· Delete Subtree
9) Click OK on all three windows.
Now we are ready to log !!
5. Testing
For testing purpose I delete the record called work01 and here what you should see on the security event log:
Event Type: Success Audit
Event Source: Security
Event Category: Directory Service Access
Event ID: 566
Date: 3/5/2008
Time: 7:33:51 PM
User: CONTOSO\Administrator
Computer: DCCONT
Description:
Object Operation:
Object Server: DS
Operation Type: Object Access
Object Type: dnsNode
Object Name: DC=work01,DC=contoso.msft,CN=MicrosoftDNS,DC=DomainDnsZones,DC=contoso,DC=msft
Handle ID: -
Primary User Name: DCCONT$
Primary Domain: CONTOSO
Primary Logon ID: (0x0,0x3E7)
Client User Name: Administrator
Client Domain: CONTOSO
Client Logon ID: (0x0,0x19062D)
Accesses: Write Property
Properties:
Write Property
Default property set
dnsRecord
dNSTombstoned
dnsNode
Additional Info:
Additional Info2:
Access Mask: 0x20
Note the following points in red (from top to down):
· The event type: the user was able to successfully perform this operation.
· Category: the object was categorized as a DS Object.
· User: the name of the user that performed this operation.
· Object Name: the complete path from where the object was located.
· dNSTombstoned: this is probably the only one that is not friendly. This attribute is logged whenever an object is deleted. For more information review the DNS-Tombstoned Attribute at MSDN.
5. Conclusion
This simple action can help you to track changes on your DNS Zone and prevent security compliance issues when auditors approach to review your environment.
Disclaimer: This article was originally posted in Portuguese on 09/08/2006 at Microsoft Latam Team Blog.