Upgrading Your PKI from Windows Server 2003 to Windows Server 2008 R2 Part IV: Migrating Enterprise CAs
In this post I will cover migrating Enterprise Certification Authorities to Windows Server 2008 R2. These steps will work for Enterprise CAs regardless of whether they are a Root CA or a Subordinate CA. The assumptions I make in this blog is that Key Archival and Role Separation is not enabled. This posts also assumes that the machine you are migrating to will have the same hostname. If you have a more complex scenario, such as one that includes Key Archival please see the Active Directory Certificate Services Upgrade and Migration Guidance.
The steps from Migrating the CA are the following:
1.Backup the CA Key and Database
2. Backup the CA Configuration
3. Backup CAPolicy.inf file
4. Note what certificate templates are available on the CA
5. Uninstall the CA Role from the existing CA
6. Remove the machine from the domain
7. Build a Windows Server 2008 R2 machine
8. Join the Machine with the same machine name as the machine that previously hosted the CA Role
8. Install Certificate Services with the Key Pair from the CA Backup
10. Restore the CA database from the CA Backup
11. Restore the CA Configuration
12. Verify that the correct certificate templates are configured on the CA
13. Verify AD permissions.
First perform the following steps:
1. Create a folder locally called CAMigrate
2. In the CAMigrate folder create a folder called CABackup and CAConfig
Backup the CA Key and Database
1. Use the following command to backup the CA Database, log files, and keys: certutil –backup <Path to CABackup folder>
2. You will be prompted to enter and confirm a password that is used to protect the private key of the CA in the resulting PFX file
Backup the CA Configuration
1. Open regedit
2. Navigate to HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\CertSvc\Configuration\<CA Name>
3. Right click on <CA Name> and select export from the context menu
4. Name the file config.reg and save the file in the CAConfig folder you created earlier
5. Copy the CABackup folder to the Windows Server 2008 machine that you previously built. Be sure to be careful where you copy the backup to as the backup contains a PFX file that contains the private key of the CA.
Backup CAPolicy.inf file
If a CAPolicy.inf file exists copy it from C:\Windows\ to the CAConfig folder that you created
Note what certificate templates are available on the CA
1. Open a command prompt, and navigate the CAConfig directory
2. Run the following command “certutil –catemplateas > CATemplates.txt
Uninstall the CA Role from the existing CA
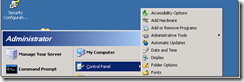
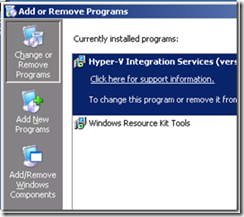
Click Start, then Control Panel, then Add or Remove Programs
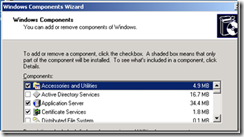
Select Add/Remove Windows Components
Uncheck Certificate Services, click Next, and then Finish
Remove the machine from the domain
Unjoin the machine that previously held the CA Role from the domain
Build a Windows Server 2008 R2 machine
Install Windows Server 2008 R2 on the machine that will host the CA Role
Install any service packs or updates
Join the Machine with the same machine name as the machine that previously hosted the CA Role
Install Certificate Services with the Key Pair from the CA Backup
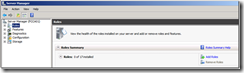
1. In server manager click on the Roles node, and then click on Add Roles
2. When the Add Roles Wizard opens, click Next
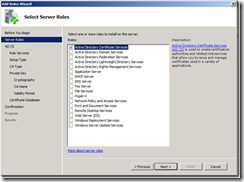
3. Select Active Directory Services and click Next
4. On the Introduction to Active Directory Certificate Services page of the wizard, click Next
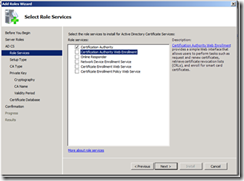
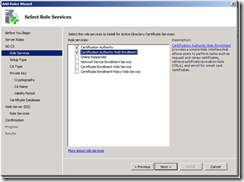
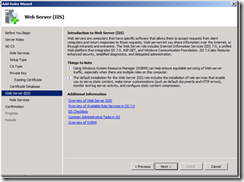
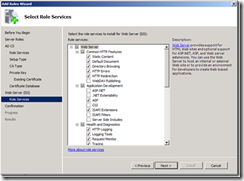
5. This article assumes that Web Enrollment is installed on the CA. Select Certification Authority and Certification Authority Web Enrollment.
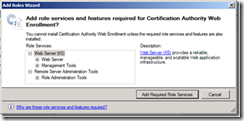
6. You will then be prompted to install the IIS Components that are required for Web Enrollment. Click Add Required Role Services.
7. On the Select Role Services page of the wizard, click Next.
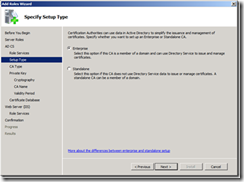
8. On the Specify Setup type page, select Enterprise, and click Next.
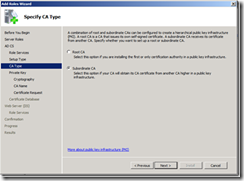
9. On the Specify CA Type page of the wizard, select either Root CA or Subordinate CA, whichever is pertinent to your installation
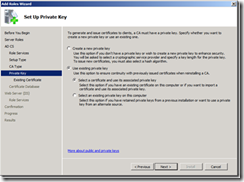
10. On the Set Up Private Key page, select Use Existing Private Key, and Select a certificate and use its associated private key
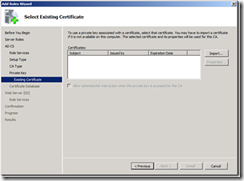
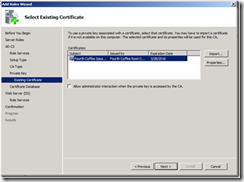
11. On the Select Existing Certificates page, click the Import… button.
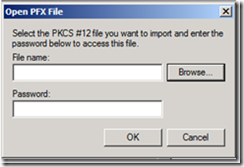
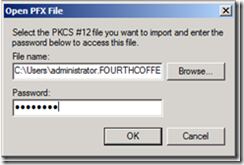
12. On the Open PFX file dialog box, click Browse…
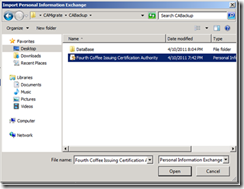
13. Select the PFX file from the backup of the CA, and click Open.
14. Enter the password for the PFX file, and click OK
15. On the Select Existing Certificate page, select the certificate, and click Next.
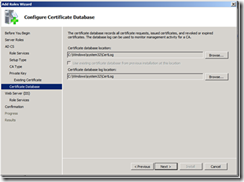
16. On the Configure Certificate Database page, select the path where you want to store the database, and log file. Click Next.
17. On the Web Server (IIS) page click Next.
18. On the Select Role Services page of the wizard, click Next.
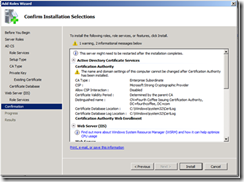
19. On the Confirm Installation Selections page, click Install.
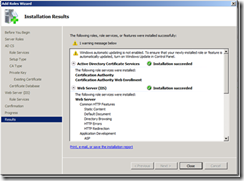
20. When the installation completes, click Close.
Restore the CA database from the CA Backup
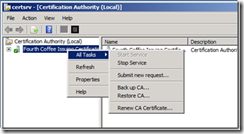
1. Open the Certification Authority MMC.
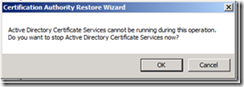
2. You will be prompted to stop Certificate Services services, click Yes.
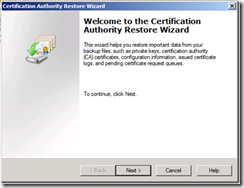
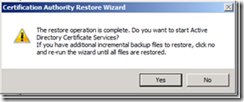
3. When the Certification Authority Restore Wizard opens, click Next.
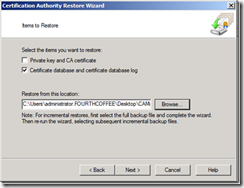
4. Select Certificate database and certificate database log, browse to the CA Backup, and click Next.
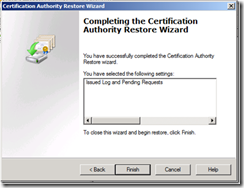
5. On the final page of the wizard, click Finish.
6. You will then be prompted to start the Certificate Services service, click Yes.
Restore the CA Configuration
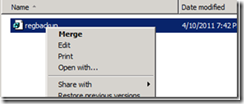
Locate the CA configuration you had previously backed up. Click on the reg file and select Merge from the context menu.
Verify that the correct certificate templates are configured on the CA
Review the CATemplates.txt file you created earlier. Ensure that those templates and just those templates are made available on the CA.
Verify AD permissions
Certificate Services is now installed on a machine with the same host name as the previous CA. However, the SID of the machine is going to be different then the previous CA. As such we need to make sure the CA has access to the PKI objects in Active Directory.
1. Open ADSIEDIT.MSC
2. Navigate to CN=Public Key Services, CN=Services, CN=Configuration, <Forest DN>
3. Locate the AIA container.
4. Within this container will be an object with CA services name.
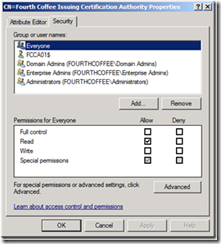
5. Right click on the object, and select Properties from the context menu.
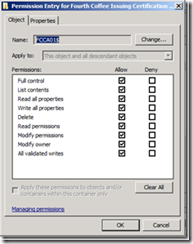
6. Select the Security tab on the resulting properties screen, and click the Advanced button.
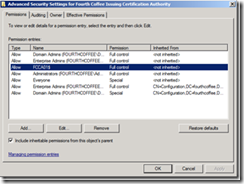
7. Locate the computer name of the machine hosting the CA Role, and select it. Then click the Edit button.
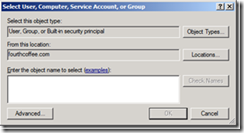
8. Click the Change button.
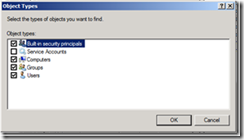
9. Click the Object Types… button
10. Select Computers and click OK.
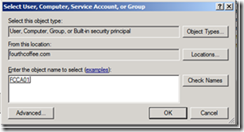
11. Type the computer name of the machine hosting the CA Role and click OK.
12. Then click OK twice.
You will need to perform the same tasks for the CDP object, Enrollment Services object, and KRA Object.
The CDP object is under the CDP container, and within a container that has the same name as the CA’s machine name.
The Enrollment Services object is in the Enrollment Services container.
The KRA object is in the KRA container.
Conclusion
This blog entry completes the series on migrating a Windows 2003 Server based Certification Authority to Windows Server 2008 R2.
-Chris