Upgrading Your PKI from Windows Server 2003 to Windows Server 2008 R2 Part III: Upgrading Standalone Certification Authorities (Offline Root CAs / Offline Policy CAs)
In this segment I am going to cover upgrading Standalone Certification Authorities. Standalone Certification Authorities are Certification Authorities (CAs) that do not use certificate templates for forming and validating certificate requests. Standalone CAs can be joined to an Active Directory Domain or can be joined to a workgroup. In this segment I am going to focus on upgrading standalone CAs that are not joined to a domain, which would be the case for offline Root and Policy CAs. Also, in this discussion I am not going to cover the process of upgrading CAs that use Hardware Security Modules (HSMs), although the process would be somewhat similar.
One of the really nice things about upgrading a standalone CA that is a member of a workgroup and that does not use an HSM is that you can get the CA you are migrating to, up and running while the previous CA is still setup. This is nice, because if you run into an issue you can simply start the migration over, while still using the old CA for any necessary functions (issuing CRLs, renewing subordinate CA certificates).
Again, throughout these series of articles the process I am using for upgrading the CA OS version is a migration, not an in-place upgrade.
The process for the upgrade is as follows:
1. Build a Windows Server 2008 R2 machine with the same hostname as the original CA
2. Backup the original CA
3. Restore the CA on the Windows Server 2008 R2 machine
4. Decommission the original CA
In this article I will be covering steps 2-3.
To decommission the original CA you can simply format and overwrite the disk or in the case of a virtual machine whatever steps you normally do to securely delete a virtual machine
Backup the original CA
My assumption in this article is that the original CA is built on Windows Server 2003.
Backing up the original CA consists of the following steps:
· Backup CAPolicy.inf file
· Backup CA keys and database
· Backup CA configuration
1. Create a folder locally called CAMigrate
2. In the CAMigrate folder create a folder called CABackup and CAConfig
Backup CAPolicy.inf file
1. If a CAPolicy.inf file exists copy it from C:\Windows\ to the CAConfig folder that you created
Backup CA keys and database
1. Use the following command to backup the CA Database, log files, and keys: certutil –backup <Path to CABackup folder>
2. You will be prompted to enter and confirm a password that is used to protect the private key of the CA in the resulting PFX file.
Backup CA configuration
1. Open regedit
2. Navigate to HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\CertSvc\Configuration\<CA Name>
3. Right click on <CA Name> and select export from the context menu
4. Name the file config.reg and save the file in the CAConfig folder you created earlier
Copy the CABackup folder to the Windows Server 2008 machine that you previously built. Be sure to be careful where you copy the backup to as the backup contains a PFX file that contains the private key of the CA.
Restore the CA on the Windows Server 2008 R2 machine
Restoring the CA consists of the following steps:
1. Restore CAPolicy.inf file
2. Install CA Role with the CA keys from the backup
3. Restore Database and Log Files from backup
4. Restore CA Configuration
Restore CAPolicy.inf file
1. Copy the CAPolicy.inf file from the CAConfig folder to the c:\Windows directory
Install CA Role with the CA keys from the backup
1. Launch Server Manager, and select the Roles node
2. Then click on Add Roles, as seen in Figure 1
Figure 1
3. The Add Roles Wizard will start, click Next
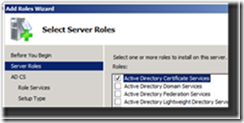
4. On the Select Server Roles page of the wizard, select Active Directory Certificate Services and click Next
Figure 2
5. On the Introduction to Active Directory Certificate Services page, click Next
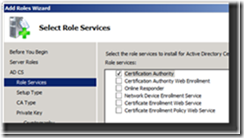
6. Select Certification Authority on the Select Role Services page of the wizard and click Next
Figure 3
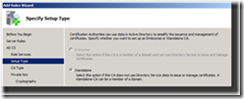
7. On the Specify Setup Type page select Standalone, and click Next
Figure 4
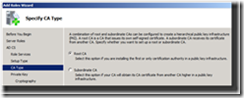
8. Select Root CA on the Specify CA Type page of the wizard as shown in Figure 5
Figure 5
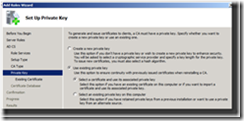
9. On the Set Up Private Key page of the wizard, select Use existing Private Key and Select a certificate and use its associated private key, then click Next
Figure 6
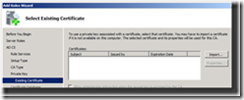
10. Click Import on the Select Existing Certificate page
Figure 7
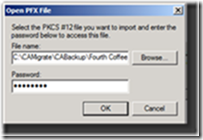
11. In the Open PFX dialog box, click Browse…
12. Browse to the CABackup folder, select the PFX (P12) file and click Open
13. Then click OK
Figure 8
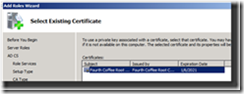
14. Select the certificate, and click Next
Figure 9
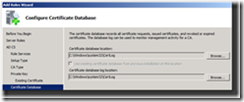
15. Configure the database and database log file locations on the Configure Certificate Database page of the wizard, and then click Next
Figure 10
16. On the Confirm Installation Selections page, click Install
17. Finally, on the Installation Results page of the wizard, click Close
Restore Database and Log Files from backup
To restore the database and log files run the following commands in an elevated command prompt:
1. net stop certsvc
2. Certutil –restoreDB –f <Path to CABackup folder>
3. net start certsvc
Restore CA Configuration
The final step is to restore the CA Configuration. The CA configuration is stored in the registry, we previously backed up this location on the original CA. First we will want to backup the current state of the registry in case we run into any issues. Then we will want to import the registry containing the CA configuration that we backed up from the original CA.
Backup CA Configuration on the new CA
1. Open regedit
2. Navigate to HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\CertSvc\Configuration\<CA Name>
3. Right click on <CA Name> and select export from the context menu
4. Name the file newconfig.reg and save the file in the CAConfig folder or an alternate location
Restore CA configuration
1. Locate the config.reg in the CAConfig folder
2. Double-click on the file, and click Yes to acknowledge the warning
3. Run the following command, from an elevated command prompt: net stop certsvc && net start certsvc
Conclusion
That covers the process for upgrading a standalone CA. A new CRL will be published locally during this process. If you desire, you can now copy this new CRL to the CDP repositories. In the next article, I will cover the process for upgrading (migrating) Enterprise CAs to Windows Server 2008 R2.