Upgrading Your PKI from Windows Server 2003 to Windows Server 2008 R2 Part I: Why Upgrade?
A lot of my customer site visits are for upgrading a customer’s PKI from Windows Server 2003 to Windows Server 2008 R2. I am going to cover the steps for upgrading a PKI in future postings in this series. However, before getting into the upgrade process, it is important to know why you may in fact want to upgrade.
A very general argument I make for upgrades of any sort are the following:
- By upgrading the operating system you are now on a platform that will be supported by Microsoft for a longer period of time.
- When we get requests for changes in functionality or the product team decides to make changes to the product to enhance certain functionality those changes are more likely to be added to the current or future operating systems and not previously released operated systems. So, in using the latest OS you have the latest, most stable platform.
- With each release of the operating system we increase the functionality and features sets of the operating system as well as operating system roles.
More specifically you will be interested in what new features and functionality are provided in Windows Server 2008 Certificate Services. So, let’s spend some time discovering the changes in features and functionality of Certificate Services.
Features Specific to Certification Authorities in Windows Server 2008 R2
Changes to Standard Edition
Prior to Windows Server 2008 R2, you need an enterprise SKU of the server OS to support Version 2 certificate templates. Version 2 certificate templates are required for features such as AutoEnrollment. Also, Version 2 templates are required for Key Archival. Additionally, Version 2 certificate templates allow you to make a number of changes to the configuration of the certificate template, versus Version 1 templates which only allow you to modify the security of the certificate template.
Cross-Forest Enrollment
Prior to Windows Server 2008 R2 a Certification Authority could only be used by clients (users, machines) in the same forest. This means if you had several forest and wanted to use functionality like autoenrollment in each forest, you needed to have an Issuing Certification Authority in each forest. This new feature allows you to have a certification authority that can provide certificates for clients in all of your forests. This not only has the possibility to decrease administrative costs, but hardware costs as well.
Changes to Certificate Templates
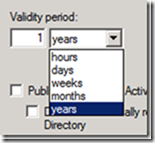
The UI for managing certificate templates now gives the administrator the ability to specify the validity period of a certificate in hours, as seen below:
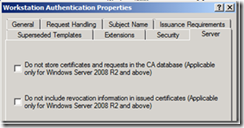
Also, for high volume CAs such as those used to support NAP or 802.1x, a certificate template can be configured so that the resulting certificate is not stored in the CA database. Also, for those same certificates templates they can be configured not to include revocation information in the certificate. See screenshot below:
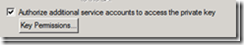
Some applications require specific permissions to be configured on the private key of a certificate stored in, say for example, the computer store. The UI now allows you to configure the private key permissions on the private key in the certificate template. The resulting certificate stored on the machine will have the permissions configured on the template.
New Features for Certificate Services in Windows Server 2008 R2
The key new feature in Windows Server 2008 R2 is Web Services. There are now two additional roles added to Certificate Services: Certificate Enrollment Web Service and Certificate Enrollment Proxy Web Service.
Rob has an excellent post on the ASKDS blog that covers Certificate Enrollment Web Services.
What about Windows Server 2008?
So there were a number of features added to Windows Server 2008, Release 1, if you will. At a high level this included the following:
- Cryptography Next Generation (CNG) and support for Suite B cryptographic protocols
- OCSP Server and Client support. See my ASKDS blog posting for more information
- Network Device Enrollment Services: A server that allows clients to enroll for certificates using the SCEP protocol
- Clustering: A key enhancement to Windows Server 2008 R2 Certificate Services is the ability configure CAs in an Active/Passive cluster
As well as a number of other features that can be found here.
Conclusion
I briefly covered many of the new features in Certificate Services for Windows Server 2008 R2. I also covered reasons for potentially upgrading your PKI to Windows Server 2008 R2. In future postings in this series I will cover the steps for upgrading a Windows Server 2003 PKI to Windows Server 2008 R2.
-Chris