ARP Spoofing Prevention in Windows Server 2012 Hyper-V
Hi there! This is Thomas Roettinger with a new blog post on how to implement ARP Spoofing protection in Windows Server 2012 Hyper-V. I published a blog in August 2011 about how to implement ARP spoofing in Windows Server 2008 R2: (https://blogs.technet.com/b/virtualpfe/archive/2011/08/02/arp-spoofing-prevention-in-hyper-v-2008-r2-sp1.aspx)
First you should know that the script that we made available in the blog post is not supported neither tested on Windows Server 2012 Hyper-V. I am sure you already browsed the new Hyper-V Manager UI and found a couple of new settings like DHCP Guard, Router Guard but nothing specific for ARP Spoofing. Well, the feature you are looking for is called Port Access Control Lists and is implemented in the new Hyper-V switch and must be configured via PowerShell.
So what are Port ACLs?
A port ACL is a rule that you can apply to a Hyper-V switch port. The rule specifies whether a packet is allowed or denied on the way into or out of the VM. ACLs have three elements with the following structure: Local or Remote Address | Direction | Action.
You can specify either a local address or a remote address in Local or Remote Address, but you cannot specify both. The value that you supply for Local or Remote Address can be an IPv4 address, an IPv6 address, or a media access control (MAC) address. Optionally you can use an IP address range if you provide the range prefix.
You can configure multiple port ACLs for a Hyper-V switch port. During operations, the port ACL whose rules match the incoming or outgoing packet is used to determine whether the packet is allowed or denied.
A good start to get familiar with the new Hyper-V switch functions is this TechNet link https://technet.microsoft.com/en-us/library/jj679878.aspx
This is the technical explanation of ARP spoofing
ARP spoofing is a man-in-the-middle attack technique that is used to attack an Ethernet local area network (LAN). The attacker associates a MAC (media access control) address with the IP address of another node by sending fake ARP messages to an Ethernet LAN. Therefore, the attacker can capture data frames that are sent to another node (here Virtual Machine attached to the same virtual switch).
This technique is also often used by hosters to ensure, Customer A does not create an IP conflict with Customer B by using a duplicated IP Address.
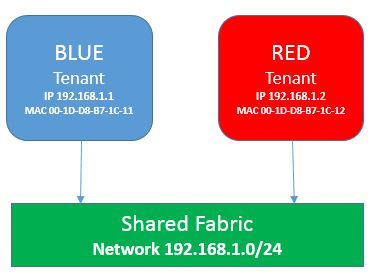
In the following scenario I am referencing to virtual machine Blue owned by Customer A and virtual machine Red owned by Customer B. Both customers get a unique IP included in their hosting package. The hosting company provisions both virtual machines with the respective IP address configuration.
The PowerShell command to create a Port ACL is called “Add-VMNetworkAdapterAcl”. You can view the full syntax for this command by typing the following command at a PowerShell command prompt:
Get-Help Add-VMNetworkAdapterAcl
In the scenario above we want to enable ARP-Spoofing for virtual machine Blue and Red.
First we create a Port ACL for virtual machine Blue to allow communication with IP Address 192.168.1.1 in both directions inbound and outbound. We then create a second rule that denies inbound and outbound for any other IP Address than the one we allowed for virtual machine Blue.
Add-VMNetworkAdapterAcl –VMName BLUE –LocalIPAddress 192.168.1.1 –Direction Both –Action Allow
Add-VMNetworkAdapterAcl –VMName BLUE–LocalIPAddress ANY –Direction Both –Action DENY
Optional (see note below)
Add-VMNetworkAdapterAcl –VMName BLUE–LocalMACAddress 00-1D-D8-B7-1C-11 -Direction Both –Action Allow
Add-VMNetworkAdapterAcl –VMName BLUE–LocalMACAddress ANY –Direction Both –Action DENY
Now configure the same two Port ACLs for virtual machine Red with the modified IP Address
Add-VMNetworkAdapterAcl –VMName RED–LocalIPAddress 192.168.1.2 –Direction Both –Action Allow
Add-VMNetworkAdapterAcl –VMName RED–LocalIPAddress ANY –Direction Both –Action DENY
Optional (see note below)
Add-VMNetworkAdapterAcl –VMName BLUE–LocalMACAddress 00-1D-D8-B7-1C-12 -Direction Both –Action Allow
Add-VMNetworkAdapterAcl –VMName BLUE–LocalMACAddress ANY –Direction Both –Action DENY
Note: You can include the MAC Address in the Port ACL but this would only be required to secure your virtual machines when you allowed MAC Spoofing in the first place while creating the virtual machine. Allow MAC spoofing is disabled by default and should only be enabled in certain scenarios for example when configuring NLB (Network Load Balancing)
For testing you log on to virtual machine Blue and ping virtual machine Red this should be successful. Now it is time to change the IP Address of VM Blue to 192.168.10.3 and ping virtual machine RED again. This should fail because the Port ACL prevents VM Blue from communication with any other IP or MAC Address then the one we specified in the ACL rule.
ARP Spoofing Prevention is just one example what you can achieve with Port Access Control Lists.
I hope you find this blog post useful , check back soon and keep watching this space for more posts on other Windows Server 2012 topics:
Thomas Roettinger
Program Manager (PACE)
Server and Cloud Division