Office 365 Core Identity Scenarios
Tim Tetrick
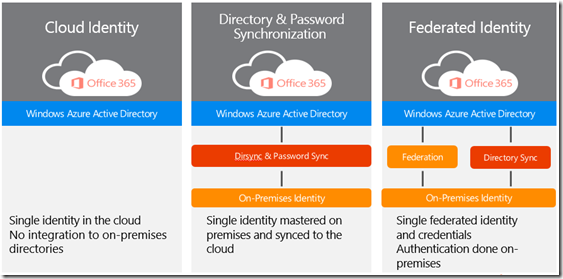
I often get questions about the identity management options with Office 365. Identity management is the process of identifying individuals in a system and controlling access to the resources in that system. With Office 365, there are three main identity options you have available – Cloud Identity, Directory Synchronization (with Password Sync), and Federated Identity.
Cloud Identity
Cloud Identity is the simplest method for providing user authentication in Office 365. Users are completely managed and stored in the cloud. Specifically, users are stored in the cloud in Windows Azure Active Directory and managed via the Office 365 Admin Portal or via PowerShell. In this model users are only stored in the cloud and are not associated with any on-premises identity provider like an on-premises Active Directory.
Directory Synchronization (with Password Sync)
Directory Synchronization is used when you have an existing on-premise Active Directory and you want those same users to have access to Office 365. By installing the DirSync tool, it will periodically sync the user profiles up to Office 365. It eliminates the need to manually create and manage users in the cloud. And with the recent release of Password Sync, it also eliminates the need to manage user passwords in two different locations. User identities and passwords are created and managed on-premises and synchronized to the cloud.
Federated Identity
With Federated Identity, also known as Single Sign-On, you authenticate to Office 365 using your on-premises identities. This is commonly done with on-premises Active Directory using Active Directory Federation Services (ADFS). ADFS requires deploying additional servers both internally and Internet-facing. See here for more details. In this scenario, if for any reason users are unable to authenticate via their local AD, then users will not be able to authenticate to Office 365 and will not be able to access any of the Office 365 services. Therefore, it is highly recommended to deploy this scenario with high-availability / redundancy in mind. With the recent release of Azure IaaS, customers are also starting to look at hosting ADFS infrastructure within Azure to solve the high-availability issue. There is a good White Paper that talks through the story of hosting ADFS infrastructure within Azure - you can find it at Office 365 Adapter: Deploying Office 365 Single Sign-On using Windows Azure. In addition, there are some third-party providers offering hosted ADFS services within Azure.
Because of the additional cost and complexity of deploying additional servers and high-availability with Federated Identity, many customers (especially in the SMB space) are choosing to implement Directory Synchronization (with Password Sync) instead. However, there are some reasons why customers will still prefer ADFS and directory federation over DirSync with Password Sync. Some of these reasons include:
- ADFS can be configured such that users who are already logged on to a domain joined and connected machine do not require any password re-entry to sign in at Office 365. This gives you true single sign-on since re-entry of the password is not required. With DirSync and password sync a user must still re-enter their password, although it will be the same password as they use on-premises.
- ADFS allows for client access filtering, which restricts access to Exchange Online to users based on their IP address.
- ADFS will honor Active Directory configured login time restrictions for users.
- ADFS can include web pages for users to change their passwords while they are outside the corporate network.
- ADFS permits use of on-premises deployed multi-factor authentication products. Note that Azure AD supports multi-factor authentication but many third party multi-factor authentication products require on-premises integration.
Thanks for reading and I hope this information was helpful!