Update: Microsoft Security Intelligence Report (SIR v12)
By Ron Grattopp  …..Well, it’s been over 2 years since I’ve blogged about the SIR (last one I did was for V8, Apr 2010), so I thought it might be time for a reprise. You might remember that the SIR is published twice a year for the previous 6-month period, so this one (V12) is for the time period July-Dec 2011.
…..Well, it’s been over 2 years since I’ve blogged about the SIR (last one I did was for V8, Apr 2010), so I thought it might be time for a reprise. You might remember that the SIR is published twice a year for the previous 6-month period, so this one (V12) is for the time period July-Dec 2011.
Microsoft Security Intelligence Report
At the site link above you can download the full report as well as an abbreviated report of just Key Findings. There are also links to the Malware Protection Center, the Security Response Center, and the Security Development Lifecycle, as well as a link for ITPro Security Tools (i.e. Microsoft Security Compliance Manager 2.5, the Microsoft Baseline Security Analyzer, and Security Update Management tools). AND there is a link to view a 3-minute v12 Report Overview video. (all shown in the screenshot below)
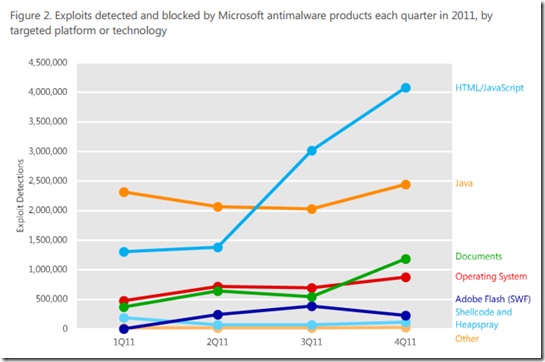
Some of the key findings were: detection of exploits delivered via HTML/JavaScript increased steeply in the second half of CY2011 (as you can see from the report excerpt below). Also exploits in document readers and editors increased in that time frame as well making them now the third most commonly detected exploit, ahead of operating system exploit detections. In malware trends, the Conficker worm continues to be the TOP threat in business environments – this SIR features and in-depth analysis of Conficker as well as specific guidance on how to defend and recover from it. Another chart shows that the infection rate of Windows 7 SP1 is less than half that of Windows XP.- which goes to the ROI discussion around Windows 7 I just had in a recent post. On home systems, auto-run worms, adware, and the “BlackHole” exploit kit are among the most prevalent threats in that space. Interestingly, the amount of SPAM blocked by FOPE declined significantly (>50% reduction) in the last CY presumably due, at least in part, to the take-down, by Microsoft, of some large botnets which you may have heard about in the news.
Of course, you still hear the occasional person pontificating about the lack of security in Microsoft products, but as you know (from previous discussions I’ve done here on the TS2 blog), since we employed the Secure Development Lifecycle (SDL) over a decade ago, we have reduced the vulnerabilities in our software to the point where Microsoft products account for only 6.4% of all vulnerabilities disclosed in H2-CY11. I’ve mounted my soapbox several times over the years to help you make the point with your customers that Microsoft is now leading the industry the area of security and thus is a good bet for you to use as the software platform for your business.
Rogue security software has become one of the most common methods that attackers use to swindle money from victims.
See www.microsoft.com/security/resources/videos.aspx for an informative series of videos designed to educate a general audience about rogue security software.
Of course the report goes on in great detail about additional security risk areas such as email threats and malicious websites, but you should download and read the report if you are interested in those. Hopefully this overview of the SIR V12 reminded you that we have a great deal of information and resources available to help you deal with the ever-evolving security threats in your computing world. But using our current products and platform are one of the key ways you can protect yourself and your business customers.
Cheers,
Ron