Microsoft releases new Security Incident Report, version 8, for H2CY09
Microsoft has released a new Security Incident Report (which you should be able to download as a PDF from this link) that covers H2CY09 (Jul-Dec 2009). I would also encourage you to visit the homepage (shown above) for this report (Microsoft's quarterly overview) where you can download it as well as a Key Findings Summary and watch a video, the page also has links to previous editions of the report and links to other Trustworthy Computing Centers.
This is Volume 8 of this quarterly report which is a comprehensive and wide-ranging study of the evolving threat landscape, as well as software vulnerability disclosures and exploits, including malicious software (malware). I’ve highlighted these SIR reports in previous posts on my old TS2 blog. As the others, this report shows once again that security can be greatly improved by upgrading to the latest software, and through user education. Hopefully someday the word will get out to the masses that Windows XP is less secure than Win 7, or even Vista, and they should consider upgrading. Actually, I think most everyone is likely aware that XP isn’t up to the security muster of the Vista/Windows 7 platform, but I think too many continue to believe that XP is “good enough” since they may not have been suffered a major infection or exploit, but as you’ll realize if you read reports such as this, it’s an ever increasing threat out there so banking on decade old technology to protect you can wind up costing you more than than the cost of prevention.
Below I’ll summarize what I consider some of the more salient points in the report. And, of course, I encourage you to review the Key Findings Summary as well.
• The 64-bit versions of Windows 7 and Windows Vista SP2 had lower infection rates than any other operating system configuration in Jul-Dec 2009. It’s important to note as well that the 32-bit versions of Vista SP2 and Windows 7 also had infection rates that were far lower (less than half) than Windows XP even with its latest service pack, SP3.
• Note that domain-joined computers were much more likely to encounter worms than non-domain computers, since worms typically spread most effectively via unsecured file shares and removable storage volumes, both of which are generally more prevalent in enterprise environments and than in homes.
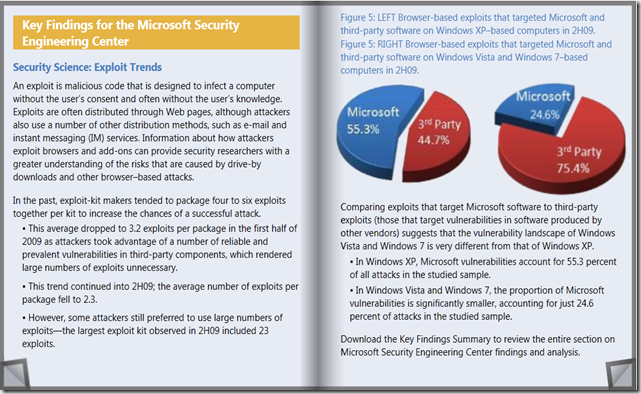
• In Windows XP, Microsoft vulnerabilities account for 55.3 percent of all attacks in the studied sample (based on comparing targets of browser-based exploits), however, in Windows Vista and Windows 7, the proportion of Microsoft vulnerabilities is significantly smaller, accounting for just 24.6 percent of attacks in the studied sample (again comparing targets of browser-based exploits). Again, reinforcing the effectiveness of Microsoft’s Trustworthy Computing Initiative.
Here’s some key thoughts from Vinny Gullotto, general manager of the Microsoft Malware Protection Center, from a post on The Official Microsoft Blog
• "as cybercrime evolves it can be difficult to know how to stay protected…the newest Microsoft Security Intelligence Report version eight (SIRv8) released today reveals that cybercrime continues to mature and adopt more traditional business techniques.”
• "SIRv8 is the most comprehensive intelligence document our team has published to date…The SIR provides information that helps customers and partners better understand the problem of malicious software, so they can take appropriate action.”
• "Home users remain the most susceptible to infected malware and socially engineered threats, such as advertisements and personal assistance sites. Worms such as Win32 Conficker are still the top threat to business, using propagation methods that work well within internal networks. Spam messages associated with advance-fee fraud ( “419 scams”) and gambling increased significantly in 2H09, and we found that 90 percent of all botnet (those hacked networks) spam originates from just five botnets.”
I”m sure it’s no surprise to you at this point to know that today’s cyber criminals are very sophisticated, perhaps some even more so than legitimate businesses—some even have their own R&D, marketing, testing, and other tools and resources to ensure the effectiveness of the malicious code they develop. it’s as much a business now as any legitimate enterprise and I point this out to encourage you to keep your guard (and your customers’ guard) continuously up.
I would also point out that this latest SIR also includes a new section with guidance from Microsoft on how to mitigate or protect against the threats described. The report says you need to consider transforming "your security message from "no" to "how”, which means demonstrating to your organization, or customers, how to be secure rather than telling them what they can or can’t do." Essentially, Microsoft stresses the importance of basic user education--keeping users informed not to click on unknown or suspicious links, how to create and use strong passwords, not to share username or password information, and other common sense measures that need to be drilled on a regular basis.
Btw, there’s also a cool thing (shown below) where you can click thru/browse the Key Findings Summary if you don’t want to download it.