Deliver amazing EMS demos, Part 3: Enterprise Mobility + Security E5 features

In the EMS Partner Community blog series and community calls, we have spent time looking at the new EMS E5 features. So far, we have taken an in-depth look at Microsoft Cloud App Security and Azure Information Protection. In the November blog posts and call, we will look at another EMS E5 feature, Azure Active Directory Premium P2.
- View the November community call
- Microsoft Cloud App Security introduction, getting started
- Microsoft Azure Information Protection introduction
In addition to writing about these offerings, I wanted to also sharpen my demo skills and explore the demo tools that are available to partners. I have spent time over the past few days setting up a new EMS demo environment, and want to share what I've learned with you.
Getting set up
Parts 1 and 2 in this blog series about EMS demos cover using the Microsoft Demos site to set up an Office 365 and EMS tenant and then configure the demo environment.
EMS demo post #1 - Build your demo environment EMS demo post #2 - Configure your demo environment
Microsoft Cloud App Security
The Cloud App Security tenant comes pre-populated with data. For an individual user, this eliminates the needs to find a firewall log to pull data from. You can log into your Cloud App Security dashboard with your tenant admin credentials.
The instructions for how to best use this demo environment are in the demo guide available on the Microsoft Demos site. Take the time to walk through the steps on your own to become familiar with how to use Cloud App Security.
Sign in to the Microsoft Demos website 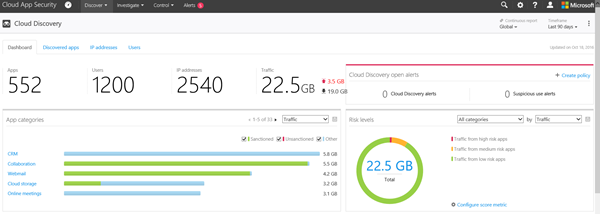
Azure Information Protection
This is one of my favorite features to show. The power of the automatic classification, and how simple it is to use, is just plain fun. Before you use it, there are some setup steps you will need to follow. On the administrative side, the setup steps are in the demo guide. The steps are all in the appendix of the Information Protection Demo Guide.
For the Azure Information Protection demo, you will need a client. The demo guide suggests setting up a local VM running Windows 10. Another option is the one that I use - hosting the VM in Azure.
The best way to do this is with a MSDN account. Log into Azure and create a VM. Search the VM Gallery for the Windows 10 Enterprise N image. This image is only available under MSDN subscriptions for non-production testing. If your company has a silver or gold competency, you may be able to use the Azure credits in your company's Visual Studio Enterprise with MSDN subscription.
- Learn more about Visual Studio subscriptions for Microsoft partners (select "Activate your Visual Studio subscription")
- Learn more about internal use software and licenses for partners
 Once you have a Windows 10 client running, you will need to install Microsoft Office. If you used the Microsoft Demos site to provision your tenant, this part will be easy.
Once you have a Windows 10 client running, you will need to install Microsoft Office. If you used the Microsoft Demos site to provision your tenant, this part will be easy.
- On the client machine, log into Office 365 with a sample user like Isaiah Langer
- On the Office 365 home page, click Install Office 2016 in the upper right corner of the browser
- Complete the Office 365 install
With Windows and Office now running, you will need the client installs for Azure Information Protection and Azure Rights Management. Download and install these on the client, and be sure to download the sample documents as outlined in the appendix of the setup guide.
When it comes to demonstrating Azure Information Protection, test things ahead of time and know the built-in conditions for each label. For example, to trigger the Confidential setting for a document with Social Security Numbers in it, you will want to include the text SSN and a properly formatted number: XXX-XX-XXXX. Credit card numbers can be tested with the number 4242 repeated four times.
Azure Active Directory Premium P2
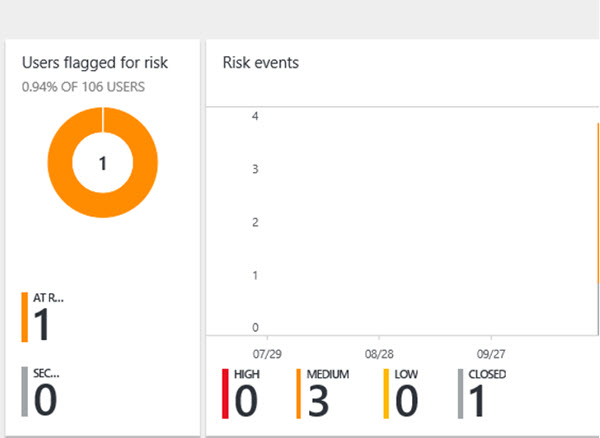 I found that showing a real risk in action really made this demo come alive for me. To make the risk dashboard come alive in Azure, I simulated logging in from an anonymous IP address. For one of the users I forced a password reset on the account to have it show as closed.
I found that showing a real risk in action really made this demo come alive for me. To make the risk dashboard come alive in Azure, I simulated logging in from an anonymous IP address. For one of the users I forced a password reset on the account to have it show as closed.
To enable an anonymous IP address, I installed a TOR browser on the Windows 10 VM I created as a client machine. To simulate logins from unfamiliar locations, VPN proxies can be used. Browsers like Google Chrome and Opera have free plugins for simulating being in another location.
Azure Active Directory Identity Protection has an initial learning period of 14 days during which it does not flag any new locations as unfamiliar locations. It also ignores sign-ins from familiar devices and locations that are geographically close to an existing familiar location. This means the best accounts to test will have a 14-day history for you to then deviate from.
For more ways to simulate different kinds of risk events, visit the Azure Active Directory Identity Protection playbook