2012 to 2014: Rise of the Bootkits
 By Lesley Kipling, Forensic Security expert, Microsoft Global Business Support.
By Lesley Kipling, Forensic Security expert, Microsoft Global Business Support.
What is a bootkit I hear you ask? Simply a bootkit is a rootkit that infects the boot process of a computer to load malicious drivers before any security software can load, and which therefore will bypass any of the operating system security controls. The term rootkit originally referred to a set of tools used to administer a UNIX machine (root was the name of the UNIX user with administrative access), today this term refers to malicious software designed to hide “stuff” (processes, files, data etc) from the operating system.
To facilitate troubleshooting the boot process inside Microsoft support, we divided the boot process into the following four phases: Initial, Boot Loader, Kernel and Logon. For the purposes of this discussion, we are really only interested in the first phase and specifically what happens after a successful power-on self test (POST). This phase involves the loading of the most important data structure on the disk, namely the Master Boot Record (MBR) which is created when the disk is partitioned, and always located at Cylinder 0, Head 0, Sector 1 of each physical disk.
The master boot code in the MBR loads the volume boot record (VBR) of the active partition which in turn loads NTLDR and the defined operating system. More information on this can be found here. Essentially then, bootkit malware replaces the normal boot sector code (either MBR or VBR) with code of its own choosing. How do you fix it? Well, if such a malware is indicated you may want to consider the use of bootrec.exe /fixmbr or /fixboot here. Bear in mind, fixing the issue without closing the vector by which the attacker was able to compromise the boot sequence may just result in re-infection.
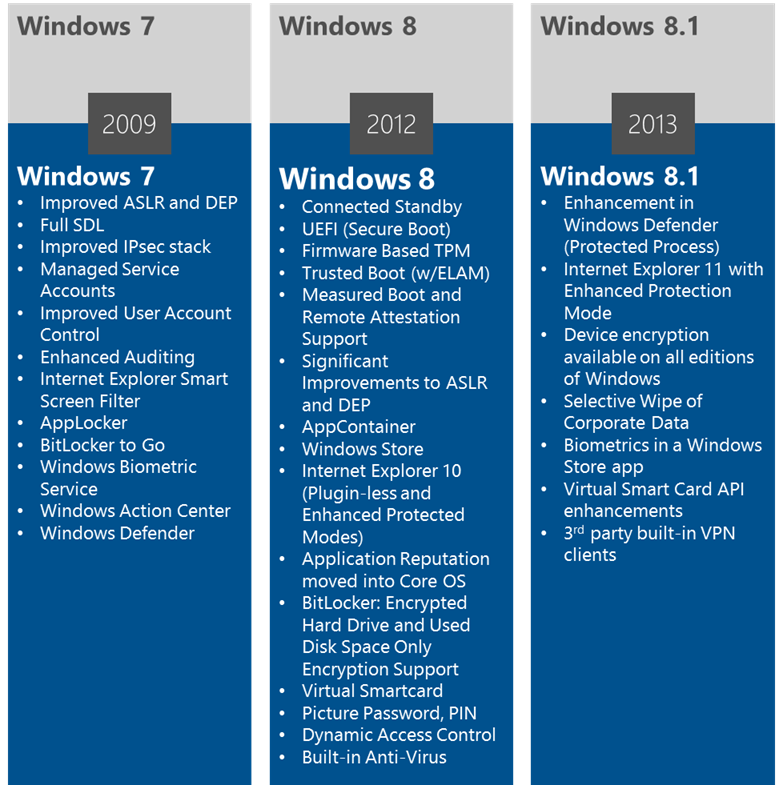
So to what do we attribute the increase in bootkits? I’d point to the fact that the Windows operating system security is getting tighter and tighter. Take a look at the graphic below to see all the enhancements made in Windows 7, resulting from security work done in Windows Vista timeframe. The reaction of the attackers? “Let’s load our malcode first then we’ll be able to bypass all of these great security features!” Bad news for us determined defenders of the Windows security ecosystem. Fortunately writing a 64-bit driver takes some skill; if not done properly the machine will bugcheck (bluescreen), we get involved, and the game is up.
But look – see those nifty new features in Windows 8? Secure Boot, Trusted boot, ELAM (early load anti-malware), Measured boot and Remote Attestation are all designed to combat that trend in bootkit development by protecting the boot sequence of the operating system. The only problem is, you need to be using Windows 8 (8.1 now) to benefit from the built-in protection mechanisms and most of our customers simply aren’t. Obviously there are complexities involved and it may not be easy for an organisation to upgrade, but where the business is considering such a project, my recommendation would be to go straight to the latest and greatest to ensure you are one step ahead of the attackers.
Historically there was the maxim of “wait for the next release” but building a trustworthy cyberspace has led the software development industry to adopt other approaches, such as agile and rapid application development; similarly contemporary defence strategies should look to include a more agile approach, aligned to increasing the detection capability of the organisation. For the Microsoft future view on what cyberspace will look like and the role cybersecurity will play, read\watch the report here.
Finally and whilst we’re on the topic of detecting the attacker quickly, I’d like to remind you of the Microsoft Security Intelligence Repost (SIR) here. To quote: “The Microsoft Security Intelligence Report (SIR) analyzes the threat landscape of exploits, vulnerabilities, and malware using data from Internet services and over 600 million computers worldwide. Threat awareness can help you protect your organization, software, and people.”
Good luck, keep up the good work and stay safe out there!