Lab Ops – PowerShell 4 and PKI
In a Remote Desktop Services lab setup involving a gateway to allow connections to our virtual desktops over the internet we are going to need to use an SSL certificate to secure traffic between the remote devices and the gateway. Typically in the past we would have gone into a server running IIS and made a self signed certificate in IIS Manager and while this still works in IIS8.5 (the one that ships with Windows Server 2012R2) there is better way and that is PowerShell 4 that is also included in Server 2012R2. Why is it better? More control specifically we can add alternate names to correspond to all the DNS entries we might need in something like RDS. We also get all the other benefits of using PowerShell like repeatability and like all ne PowerShell commands it’s easy to understand what it’s doing..
To make a certificate:
New-SelfSignedCertificate `
-CertStoreLocation cert:\LocalMachine\My `
-DnsName rds-Broker.contoso.com,rds.contoso.com,rds-gateway.com
where the new certificate is going to be stored on the local machine in the “my” folder and it has two alternate names. By the way not everyone knows this but the ` character is the line continuation character and means I can format code that’s easier for you to read.
The new certificate is not much use where it is so we can also export it and if we want the private key we’ll need to password protect it. First we need to find it and to do that we can simply browse the certificates just as we might for any other kind file on a hard drive except that for certificates we are navigating through the certs: drive not the C drive. Get-ChildItem is the proper PowerShell command for navigating folders of any kind but it also has aliases dir ls, gci etc. I mention this because in some IT departments it is considered best practice not to use aliases but the root PowerShell commands to provide clarity, perhaps in the same way as we don’t use the word ain’t in an English class!
$Cert = Get-ChildItem -Path cert:\localmachine\My | `
where subject -EQ "CN=RDS-Broker.contoso.com, CN=RDS-Web.contoso.com, CN=rds.contoso.com"
Now we can setup a password and export it
$pwd = ConvertTo-SecureString -String "Passw0rd!" -Force –AsPlainText
Export-PfxCertificate `
-cert $cert `
-FilePath '\\rds-DC\c$\RDS-Web self signed certificate.pfx' `
-Password $pwd
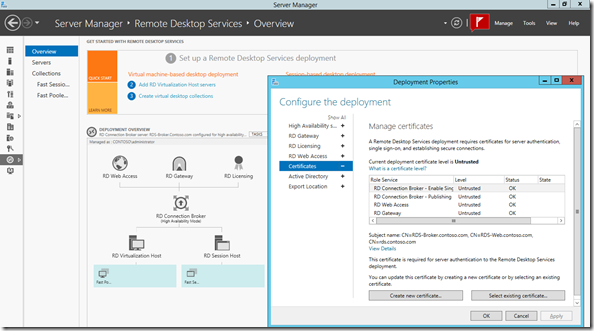
We could then import this into our VDI deployment with PowerShell as well, but there is a simple UI in the deployment properties in Server Manager.
where we can check our certificates are installed and recognised as part of the deployment. Of course there is proper PowerShell for this..
set-rdcertificate `
-Role RDGateway `
-ConnectionBroker RDS-Broker.contoso.com `
-ImportPath 'C:\RDS-Web self signed certificate.pfx'`
-Password $pwd #same as password above
which not only puts the certificate where it need to go but put makes the RD Broker aware of it.
Creating certificates is also going to be useful if we want to manage any evals , demos and labs we might want to work with in Azure but that is a story for another post , not least because I need spend more time in the cloud myself!
In the meantime do have a look at the PowerShell content in MVA, and if you aren’t running Server 2012R2 where you are you can install it on older operating systems back to Windows Server 2008 R2/ Windows 7 from here