The Right Theory for IT.
Back in the sixties Douglas McGregor at MIT came up with Theory X and Theory Y. This is so old it might infact be a new thing for you. If it is new to you the theories play out like this…
Theory X |
Theory Y |
| - We’re all lazy | - We work hard |
| - We hate work | - We enjoy work |
| - We’re under rigorous control | - We have sensible guidelines |
| - We have no autonomy | - We’re self-motivated |
| - There’s no trust | - We’re trusted |
If we apply this to IT then:
- Theory X will result in a complete lockdown of the desktop, and access to the internet because it’s assumed our users will misuse the IT systems at every opportunity and will also try to make off with our company data if not the device itself!
- Theory Y will mean we can install apps on our machine, the internet will be available to us and we can use our device for personal stuff as well as work, because we can be trusted to do the right thing.
I’ve only had limited exposure to Theory X some 10 years ago, but my wife’s work adopts that theory and so do the roles of other family members, so I’ve just about enough information to apply those six principles that Chris from AvePoint covers in his article earlier in the month.
In a Theory-X company environment, only a select few employees that need to work remotely will be allowed to. If it is allowed then (in my experience) several bad things start to happen. The first is that there is typically a collection of tools that are poorly integrated to provide the VPN, encryption, and remote desktops. This happens because IT is seen as an overhead in these organisations the lack of trust also manifests itself in the mistaken belief that by using different providers a system can be more secure. Typically the infrastructure is bolted onto what’s there and a lack of investment means that not everything works remotely, even if it’s tested!
Obviously Integration and Usability suffer, but if Remote desktops are used, the desktop you get at work is the same at home (however good or bad that is). The only problem then is the extra pain of logging into that at home (setting up the VPN etc.) especially if there’s an aggressive timeout policy as well which closes the session rather than leaving it open but dropping the connection.
Productivity for my wife actually goes up at home as she is on hot desk hell at the office and the office network seems slower to connect to her line of business systems than when she is home, oh and the coffee is better and cheaper at home!
Scalability is a huge problem here. The limiting factor is not the technology, I think it’s the helpdesk. If a fragmented solution is implemented, it’s going to be more prone to failure and so this will limit it’s use and the helpdesk may well not have had the training needed to support the user base .
Security & Privacy. The theory X approach can often create security problems as direct result of trying to be too secure. If I look at security on my wife’s machine then there’s no single sign on, indeed some of the passwords are system generated alphanumerics like a GUID. She can’t hope to remember these so she writes them down albeit in an obfuscated fashion. If the mobile users are dedicated and motivated then they will try and circumvent the security lockdown in some way. USB drives, e-mail and cloud storage are the usual methods so that corporate data can be accessed on users personal devices as they are familiar and often faster than the way device Theory X grudgingly hands out to employees.
How does all of this contrast with the world of Theory Y? I am now in Theory Y heaven at Microsoft so if I consider myself a mobile worker then what do those principles look like now:
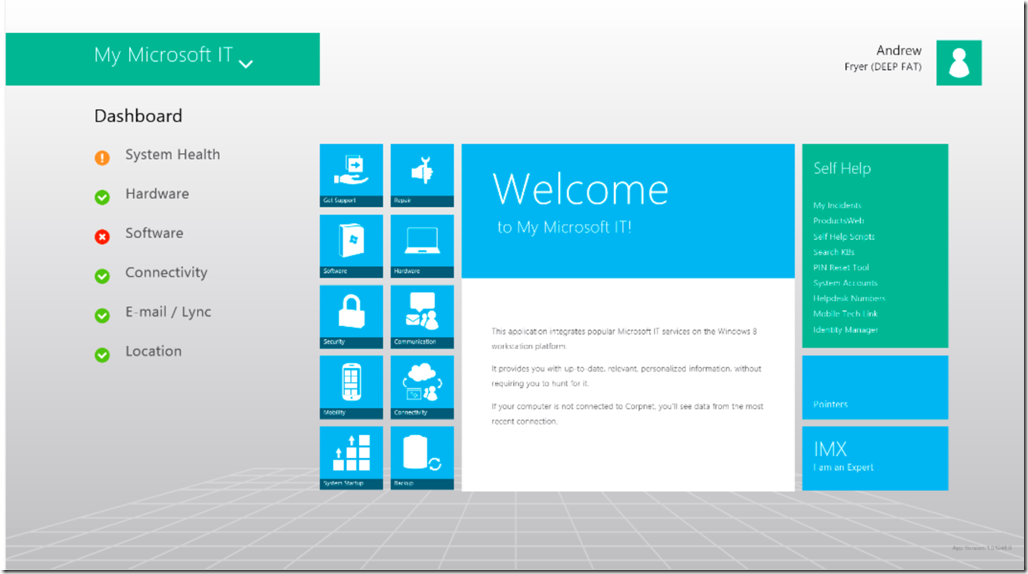
Integration. This just got installed on my Surface 2 Pro by our IT department MSIT
It gives me a rich dashboard to get everything done that I need to, it’s little things like this that make life easy. other good examples are when I book leave it shows up in my calendar and my managers. When I am in a meeting in Lync my status gets set to busy, when I am presenting I can drop my usual background and PowerPoint tells Lync I am unavailable so only my manager can interrupt my presentation with an instant message. SkyDrive (mine and Pro) just sync’s everything. I have work folders for syncing more sensitive stuff across my devices. Bitlocker & Direct Access are part of my desktop and my smartcard authentication is one of my login process to access resources via ADFS like Yammer wherever I am.
Usability for me starts with me having a choice of which devices I use. I do have a Surface 2 Pro, but I didn’t have to have that, I have a Nokia 925 just now and actually I kind of miss the older 920 but you get the idea. I can elect which devices mine or Microsoft’s. I get e-mail on up to a limit of 10, if I go over that I choose which to disable and I can report the phone as missing all from the same web portal.
Productivity. This is mostly down to Direct Access & Lync, The only issues I have is in participating in the odd badly prepared meeting, or by someone who isn’t Lync aware at the other end of the call.
Scalability. I think this is well covered at Microsoft. We have a very small helpdesk and you might think we are all techies but actually in my department of 80 odd people, we have about 20 technical chaps and most of those are developers. Although I am an MCSE I am not allowed near production infrastructure, so I do need to make a call to these guy’s if I've any issues.
Security. I have BitLocker to protect my data. If I choose to disable it then I must get manager approval. In Windows 8.1 I can store a virtual smartcard on my device, so I don’t need a reader to use my real smartcard. The password for this, plus my domain account and my registered devices are the only three things I need to be secure, although my smartcard does actually have to let me into our offices too! Also, my VPN won’t work unless my machine is current with patches and malware updates.
Privacy. You might think that this fun loving culture is not as secure say as a government department. Actually I think our culture is more secure, we have an up-to-date infrastructure design, backed by experts in threat management, but most importantly we have a culture of security. This means we believe that we should protect high business impact data like personal information very carefully. Of course it’s you that keeps us honest here as any breaches would be widely reported. In my case we simply can’t do some of the cross matching of personal data that would be useful to better understand you or our audience because of these policies. This might be seen to be inefficient, but the cost to our reputation in this area would be far higher than any short term gain.
So my assertion is that not only is Theory Y a better place to work, it’s also more secure than Theory X. The statistics bear me out, the fun loving high-tech companies rarely loose confidential data whereas this continues to be an issue for the more traditional companies and institutions who try to rely on technology to maintain security when it is really all about the user and the organisational culture.
What theory does your company adopt? Would you agree with Mr Fryer that Theory Y’s the way forward? Let us know in the comments below or via @TechNetUK.