Increase your security IQ; 5 key resources that can help you take back control
By Ken Malcolmson, Group Manager at Trustworthy Computing, Microsoft.
Five free, easy to use resources that can help mitigate the risks of legacy applications, understand the evolving threat landscape, and help you understand the risks of operating Windows XP systems after April 2014.
It can be a tough time being responsible for “computer security” these days. In a rapidly evolving threat landscape it can be difficult to stay on top of all the latest advice and guidance on how best to protect your systems and networks. Here are five key resources that Microsoft Trustworthy Computing offers that can help.
1. The Microsoft Security Intelligence Report (SIR) and SIR applications
Imagine that someone managed to collect and analyze malware and security information from more than a billion systems around the world. Imagine that analysis was brought together in a single, easy to access location to give you a clear picture of the threat landscape and help you adjust your defensive strategies.
The good news is you don’t have to imagine it – the Microsoft Security Intelligence Report contains extensive analysis of the latest trends in malicious software infection rates – breaking the information out by operating system, by geography, and by threat type – as well as examining changes in software vulnerability disclosures, the effectiveness of real-time antimalware suites, and the latest fake antivirus scams. With key findings available in ten languages, deep-dive analysis of the threat landscape in more than 100 countries and regions around the world, and practical guidance on how you can protect yourself and your organization from these threats.
The SIR is available on the web, as a Windows 7 and 8 desktop application, and you can keep up to date on our latest intelligence through the Trustworthy Computing Blogs Windows Phone application.
2. Enhanced Mitigation Experience Toolkit (EMET) v4.0
EMET is a free mitigation tool designed to help IT Professionals and developers prevent vulnerabilities in software from being successfully exploited. The tool works by protecting applications via the latest security mitigation technologies built into Windows, even in cases where the developer of the application didn’t opt to do this themselves. By doing so, it enables a wide variety of software to be made significantly more resistant to exploitation – even against zero day vulnerabilities and vulnerabilities for which an update has not yet been applied.
EMET has been a very popular tool among customers trying to manage risk associated with insecure applications they have in their environments.  Over the past year we have seen some attackers evolve their tactics in ways that we believe can be mitigated with a tool like EMET. We have also received feedback from a number of customers on how we could make EMET better fit their needs. This information has been invaluable in enhancing the latest version of the tool. The latest version, EMET 4.0, incorporates a number of new enhancements including protection against Man in the Middle attacks leveraging the Public Key Infrastructure (PKI), and hardening of Return-Oriented Programming (ROP) mitigations. This version also addresses known compatibility issues and is designed to work with our latest technologies such as Internet Explorer 10 and Windows 8.
Over the past year we have seen some attackers evolve their tactics in ways that we believe can be mitigated with a tool like EMET. We have also received feedback from a number of customers on how we could make EMET better fit their needs. This information has been invaluable in enhancing the latest version of the tool. The latest version, EMET 4.0, incorporates a number of new enhancements including protection against Man in the Middle attacks leveraging the Public Key Infrastructure (PKI), and hardening of Return-Oriented Programming (ROP) mitigations. This version also addresses known compatibility issues and is designed to work with our latest technologies such as Internet Explorer 10 and Windows 8.
3. Software Vulnerability Exploitation Trends
Microsoft recently released new research that examines the long-term impact of security mitigations that Microsoft has implemented to address software vulnerabilities. This analysis is based on a study of security vulnerabilities that have been addressed through Microsoft security updates over a seven year period (2006 – 2012) and are known to have been exploited. The study focuses on assessing trends in the types of vulnerabilities that have been exploited, the product versions that have been targeted and the exploitation techniques that have been used by attackers.
You might wonder why we conduct this type of research. Many of the customers I talk to are interested in using software vulnerability counts as a measure of whether the industry and the software vendors they procure software from are getting better or worse at developing software that has fewer and less severe vulnerabilities. We publish various vulnerability counts in the Microsoft Security Intelligence Report. But simply counting vulnerabilities seems to assume that all vulnerabilities pose equal risk. When we take a closer look at which vulnerabilities are actually exploited by attackers and how they are exploited, we can get a better picture of what’s really going on, which can inform how associated risks can be managed more efficiently.
Some of the key findings from the new research paper, called “Software Vulnerability Exploitation Trends,” include:
- The number of remote code execution (RCE) vulnerabilities that are known to be exploited per year appears to be decreasing.
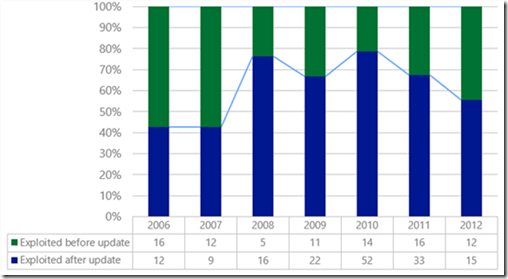
- Vulnerabilities are most often exploited only after a security update is available, although recent years have shown an upward trend in the percentage of vulnerabilities that are exploited before a security update is available.
Figure 1: Percentages of CVEs that were exploited before vs. after security updates were available
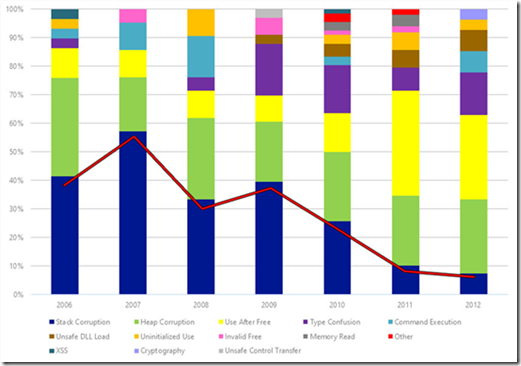
- Stack corruption vulnerabilities were historically the most commonly exploited vulnerability class, but now they are rarely exploited. The use of stack corruption vulnerabilities declined between 2006 and 2012 from 43% of exploited vulnerabilities to 7%.
Figure 2: The distribution of CVE vulnerability classes for CVEs that are known to have been exploited
- Use after free vulnerabilities are currently the most commonly exploited vulnerability class.
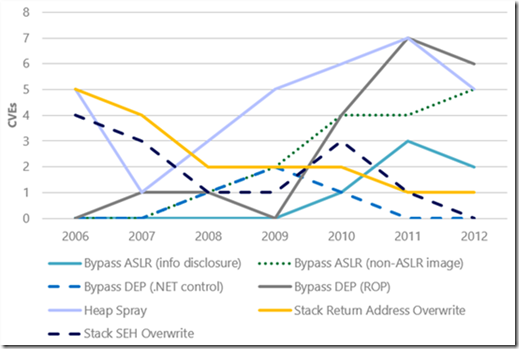
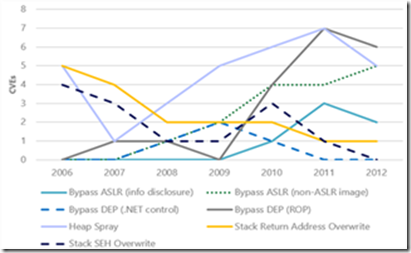
- Exploits increasingly rely on techniques that can be used to bypass the Data Execution Prevention (DEP) and Address Space Layout Randomization (ASLR).
Figure 3: The number of CVEs that were exploited using specific exploitation techniques
There are plenty of other data points included in this new research that help us understand the factors that make exploitation of vulnerabilities more difficult. Based on the research, the paper makes specific recommendations on how these factors can be influenced to help reduce the likelihood of exploitation and thereby help manage risk.
4. CISO Perspectives
We regularly discuss security topics with many security executives around the world. Many of the Chief Information Security Officers (CISOs) and security executives that we talk to tell me that they are always craving information. It always seems as though while some parts of their job responsibilities are under control, they think that other areas need more of their attention or could be more efficiently managed. Since they typically have limited time, limited information and limited resources, they look for sources of information that are tailored for their specific needs, making the information easy to consume and highly valuable. One such source of information for security executives is… other security executives.
 We’ve captured some of these discussions and developed a new series of articles that will share some of their insights on important security topics with the broader security community. The series, called CISO Perspectives, launched in early September with the first two articles about risk and cloud compliance.
We’ve captured some of these discussions and developed a new series of articles that will share some of their insights on important security topics with the broader security community. The series, called CISO Perspectives, launched in early September with the first two articles about risk and cloud compliance.
CISO Perspectives on Risk – this article provides insights on the challenges, success factors and potential solutions on the topic of risk. The article includes commentary from CISOs representing some of the world’s largest organizations. Our aim is to share and highlight some of the key things that CISOs and information and security risk specialists might want to consider in relation to risk management.
This article discusses approaches to identifying and understanding risk and suggests resources for identifying, quantifying, measuring and mitigating risk.
CISO Perspectives on Compliance in the Cloud - regulatory compliance is a hot topic among many of the customers we talk to. Of particular interest is compliance as it relates to the cloud. It is a challenging topic and there are many regulations that Chief Information Security Officers (CISOs) need to be aware of and adhere to and these can vary significantly by industry and location.
This CISO Perspectives article provides insight on the challenges, success factors and potential solutions of compliance from CISOs representing some of the world’s largest organizations. Our aim is to share and highlight some of the key things that other CISOs and information and security risk specialists might want to consider in relation to the topic of compliance.
The article discusses three areas of compliance – location, risk assessment and due diligence – and includes perspectives from some industry leaders.
We will look for opportunities to publish more CISO Perspectives articles on future topics. Keep up to date at our blog.
5. The risk of running Windows XP systems after April 2014
If you are still running systems using Windows XP, you need to know at after April 8 2014, there will be no more support for that version of the operating system – that includes updates that address security vulnerabilities in the code.
Per our long established product support lifecycle, after April 8, 2014, Windows XP SP3 users will no longer receive new security updates, non-security hotfixes, free or paid assisted support options or online technical content updates. This means that any new vulnerabilities discovered in Windows XP after its end of life will not be addressed by new security updates by Microsoft. Moving forward, this will likely make it easier for attackers to successfully compromise Windows XP-based systems using exploits for unpatched vulnerabilities. In this scenario, antimalware software and other security mitigations are severely disadvantaged and over time and will become increasingly unable to protect the Windows XP platform.
What is the risk of continuing to run Windows XP after its end of support date? One risk is that attackers will have the advantage over defenders who choose to run Windows XP because attackers will likely have more information about vulnerabilities in Windows XP than defenders. Let me explain why this will be the case.
When Microsoft releases a security update, security researchers and criminals will often times reverse engineer the security update in short order in an effort to identify the specific section of code that contains the vulnerability addressed by the update. Once they identify this vulnerability, they attempt to develop code that will allow them to exploit it on systems that do not have the security update installed on them. They also try to identify whether the vulnerability exists in other products with the same or similar functionality. For example, if a vulnerability is addressed in one version of Windows, researchers investigate whether other versions of Windows have the same vulnerability. To ensure that our customers are not at a disadvantage to attackers who employ such practices, one long standing principle that the Microsoft Security Response Center (MSRC) uses when managing security update releases is to release security updates for all affected products simultaneously. This practice ensures customers have the advantage over such attackers, as they get security updates for all affected products before attackers have a chance to reverse engineer them.
But after April 8, 2014, organizations that continue to run Windows XP won’t have this advantage over attackers any longer. The very first month that Microsoft releases security updates for supported versions of Windows, attackers will reverse engineer those updates, find the vulnerabilities and test Windows XP to see if it shares those vulnerabilities. If it does, attackers will attempt to develop exploit code that can take advantage of those vulnerabilities on Windows XP. Since a security update will never become available for Windows XP to address these vulnerabilities, Windows XP will essentially have a “zero day” vulnerability forever. How often could this scenario occur? Between July 2012 and July 2013 Windows XP was an affected product in 45 Microsoft security bulletins, of which 30 also affected Windows 7 and Windows 8.
Some of the people I have discussed this scenario with are quick to point out that there are security mitigations built into Windows XP that can make it harder for such exploits to be successful. There is also anti-virus software that can help block attacks and clean up infections if they occur. The challenge here is that you’ll never know, with any confidence, if the trusted computing base of the system can actually be trusted because attackers will be armed with public knowledge of zero day exploits in Windows XP that could enable them to compromise the system and possibly run the code of their choice. Furthermore, can the system’s APIs that anti-virus software uses be trusted under these circumstances? For some customers, this level of confidence in the integrity of their systems might be okay, but for most it won’t be acceptable.
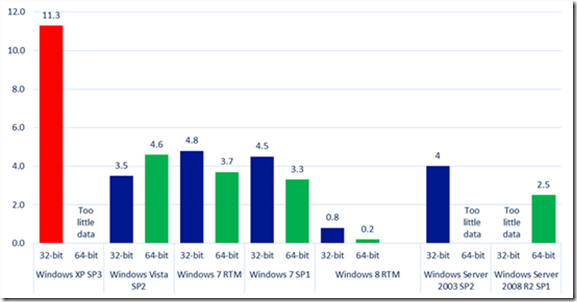
As for the security mitigations that Windows XP Service Pack 3 has, they were state of the art when they were developed many years ago. But we can see from data published in the Microsoft Security Intelligence Report that the security mitigations built into Windows XP are no longer sufficient to blunt many of the modern day attacks we currently see. The data we have on malware infection rates for Windows operating systems indicates that the infection rate for Windows XP is significantly higher than those for modern day operating systems like Windows 7 and Windows 8.
Figure 1: Infection rate (CCM) by operating system and service pack in the fourth quarter of 2012 as reported in the Microsoft Security Intelligence Report volume 14
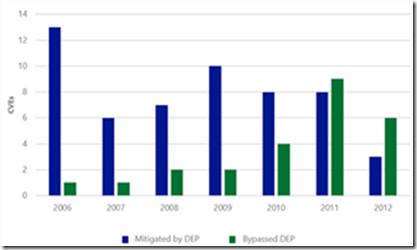
I wrote above about the findings of a new study on exploit activity that we just published: Software Vulnerability Exploitation Trends - Exploring the impact of software mitigations on patterns of vulnerability exploitation. This seven-year study indicates that attackers have evolved their attacks to overcome one of the key security mitigations that Windows XP has: Data Execution Prevention (DEP). Figure 3 shows the number of common vulnerabilities and exposures (CVEs) that had exploits that would have been mitigated if DEP were enabled compared to the number of CVEs that had exploits that bypassed DEP. With the exception of 2007 and 2008, there appears to be a clear downward trend in DEP’s ability to retroactively break exploits. This trend is not because DEP is no longer effective; rather, it is an indication that attackers have been forced to adapt to environments in which DEP is already enabled—at increased cost and complexity. The evidence is the increasing number of CVEs that had exploits that bypassed DEP.
Figure 2 (left): The number of CVEs that were exploited using specific exploitation techniques; Figure 3 (right): The number of CVEs for which exploits were written that could have been mitigated by enabling DEP as compared to the number of CVEs that had exploits that bypassed DEP
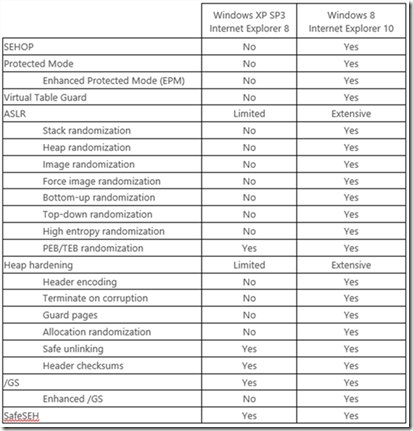
This new data shows us that the predominate threats that individuals and organizations face are now much different than they were when Windows XP Service Pack 3 was released. Turning on the Windows Firewall in Windows XP Service Pack 2 and later operating systems forced attackers to evolve their attacks. Rather than actively targeting remote services, attackers now primarily focus on exploiting vulnerabilities in client applications such as web browsers and document readers. In addition, attackers have refined their tools and techniques over the past decade to make them more effective at exploiting vulnerabilities. As a result, the security features that are built into Windows XP are no longer sufficient to defend against modern threats. Windows 8 has significantly superior security mitigations compared to Windows XP as Figure 4 illustrates. Detailed information on the new security mitigations built into Windows 8 is available in the aforementioned research paper.
Figure 4: The table below compares the mitigation features supported by Internet Explorer 8 on Windows XP Service Pack 3 with the features supported by Internet Explorer 10 on Windows 8. As this table shows, Internet Explorer 10 on Windows 8 benefits from an extensive number of platform security improvements that simply are not available to Internet Explorer 8 on Windows XP.
Organizations need a level of certainty about the integrity of their systems. Minimizing the number of systems running unsupported operating systems is helpful in achieving that. End of support for Windows XP is April 8, 2014.
So there you have it – five key resources that can help you better understand the risks facing your organization, and some thoughts on mitigating some of those risks. I hope you found this article interesting and informing.
BIO:
Ken Malcolmson is a group marketing communications manager in Microsoft’s Trustworthy Computing Group. In this role, Malcolmson and his team manage marketing and communications for a range of security domains at the company, including Microsoft’s corporate security strategy; the Microsoft Security Engineering Center, which includes the Security Development Lifecycle and Security Science; the Microsoft Security Intelligence Report, which provides in-depth analysis of the global threat landscape; and Microsoft’s collaborative work with governments, multinational organizations and both industry and non-profit groups to enhance security across the cyber-ecosystem.