How to publish a private certificate chain for Communicator Phone Edition (aka Tanjay)
Communication between the Communicator Phone Edition and Office Communications Server 2007 is by default encrypted using TLS and SRTP. Therefore the device needs to trust certificates presented by Communications Server 2007 servers. If you're using a well known Public Root CA (see table below), the certificate will automatically be trusted by the device.
| Vendor | Certificate Name | Expiry Date | Key Lenght |
| Comodo | AAA Certificate Services | 12/31/2020 | 2048 |
| Comodo | AddTrust External CA Root | 5/30/2020 | 2048 |
| Cybertrust | Baltimore CyberTrust Root | 5/12/2025 | 2048 |
| Cybertrust | GlobalSign Root CA | 1/28/2014 | 2048 |
| Cybertrust | GTE CyberTrust Global Root | 8/13/2018 | 1024 |
| Verisign | Class 2 Public Primary Certification Authority | 8/1/2028 | 1024 |
| Verisign | Thawte Premium Server CA | 12/31/2020 | 1024 |
| Verisign | Thawte Server CA | 12/31/2020 | 1024 |
| Verisign | Comodo | 1/7/2010 | 1024 |
| Verisign | Class 3 Public Primary Certification Authority | 8/1/2028 | 1024 |
| Entrust | Entrust.net Certification Authority (2048) | 12/24/2019 | 2048 |
| Entrust | Entrust.net Secure Server Certification Authority | 5/25/2019 | 1024 |
| Equifax | Equifax Secure Certificate Authority | 8/22/2018 | 1024 |
| Geotrust | GeoTrust Global CA | 5/20/2022 | 2048 |
| Godaddy | Go Daddy Class 2 Certification Authority | 6/29/2034 | 2048 |
| Godaddy | https://www.valicert.com/ | 6/25/2019 | 1024 |
| Godaddy | Starfield Class 2 Certification Authority | 6/29/2034 | 2048 |
Table 1 - Public certificates trusted by Communicator Phone Edition
If you're using your own private Root CA the device may or may not trust the certificate. Communicator Phone Edition will query AD for objects of category certificationAuthority (CN=Certification Authorities, CN=Public Key Services, CN=Services, CN=Configuration, DC=<domain>, DC=<tld> ). If the query does not return any object or if the objects have empty caCertificate attributes the device will search for AD objects of category pKIEnrollmentService.
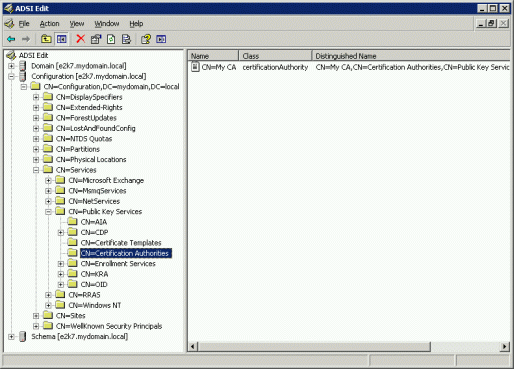
If you deployed Windows Certificate Services on a domain member server, that server will probably be already published. If not, to have the Root CA certificate placed in the caCertificate attribute, use the following command:
certutil -f -dspublish <Root CA certificate in .cer file> RootCA
Jens Trier Rasmussen has a nice blog post about this procedure.
But now imagine that you use a private certificate with a deep certificate path, how would you add the full certificate chain to AD?
I first came up with this problem recently, when I had to use a certificate from Saphety, a Portuguese public Certification Authority. Although Saphety certificates are generally trusted, since they are signed by ValiCert, this particularly long certification path (see figure below) was causing problems when used with Communicator Phone Edition. The symptoms were the same as if the certificate was not trusted.
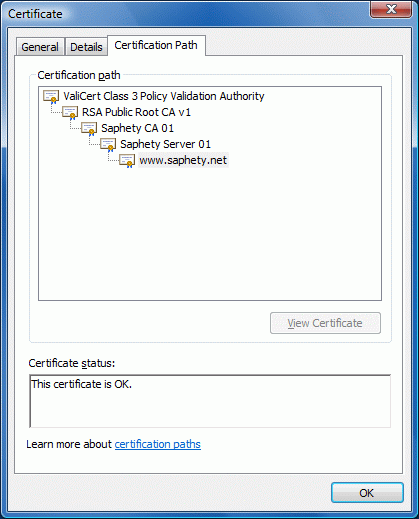
The solution is to publish the whole certificate chain (both the Root CA and all subordinated CAs) in Active Directory. Here are the detailed steps:
- Download the full certificate chain (.p7b file) and double click it
- Expand the file name, select Certificates, right click each certificate on the right pane, select All Tasks and then Export...
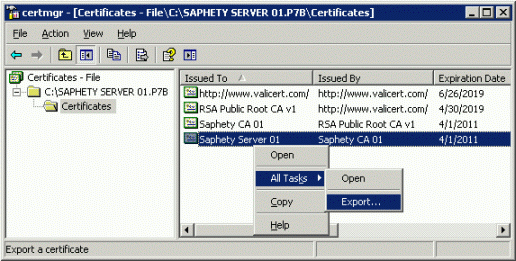
- Save each certificate as a .CER file.
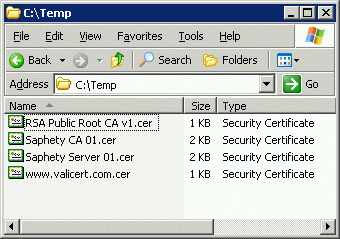
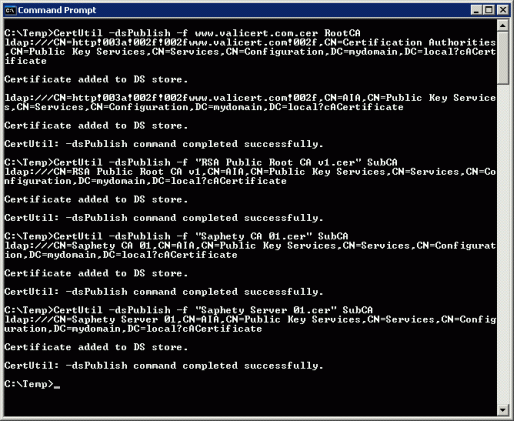
- Add the top level CA as a RootCA and all the others as SubCA, using the following commands:
CertUtil -dsPublish -f www.valicert.com.cer RootCA
CertUtil -dsPublish -f "RSA Public Root CA v1.cer" SubCA
CertUtil -dsPublish -f "Saphety CA 01.cer" SubCA
CertUtil -dsPublish -f "Saphety Server 01.cer" SubCA
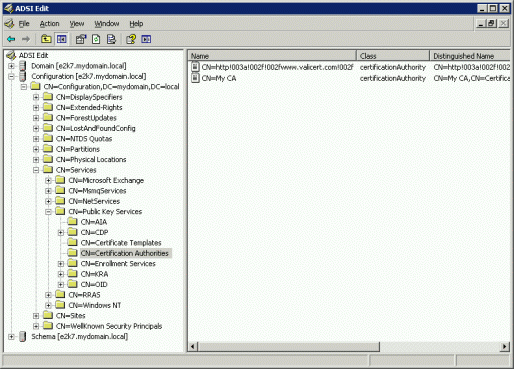
- Using ADSIEdit, verify that the objects were added under CN=Certification Authorities (CN=AIA for the Sub CAs ), CN=Public Key Services, CN=Services, CN=Configuration, DC=<domain>, DC=<tld> .
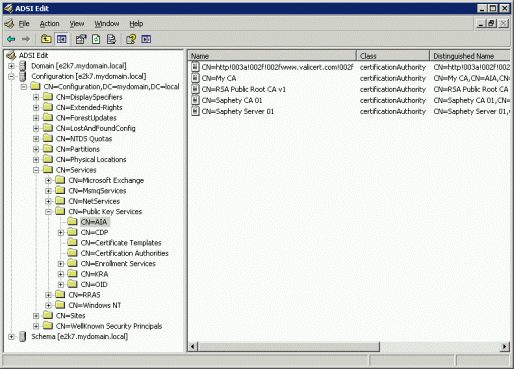
And that's it. Communicator Phone Edition should now be able to download the certificate from OCS and trust it. For more information, read Microsoft Communicator Phone Edition Deployment Guide.