Replace certificates on ADFS 3.0
In my test environment I wanted to replace self-signed certificates with publicly trusted ones.
Follow these steps if you want to achieve the same:
- RDP to your ADFS 3.0 server
- Import the new certificate to the Machine’s Personal Store
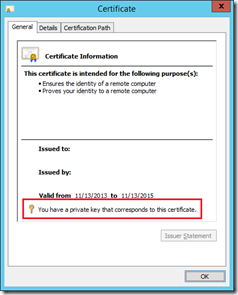
- Make sure you have a private key that corresponds to this certificate. If not, go to the PC you requested the certificate on, export it from there and make sure to include the private key,
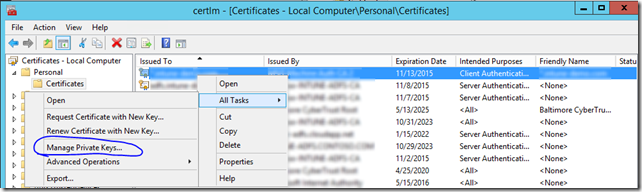
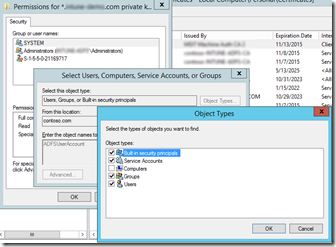
- Assign the proper permissions to the Private Key for the ADFS Managed Service Account:
- Make sure to select “Service Accounts” in when searching for the account.
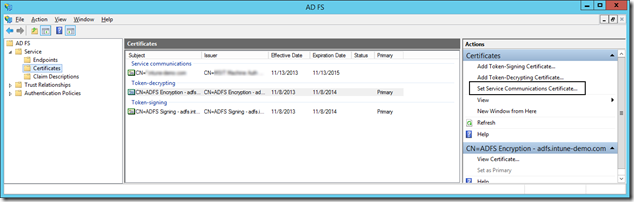
- Now switch to AD FS management, drill down to Certificates and select “Set Service Communication Certificate”
- You will be prompted for the required certificate. If you don’t see the new certificate in the list of available certificates – it means you either don’t have the private key that corresponds to this certificate OR you didn’t import the cert correctly.
(next commands have to be done too - thanks Jaguar who mentioned this in a comment)
- Run Get-AdfsSslCertificate. Make a note of the thumbprint of the new certificate.
- If it's unclear which certificate is new, open MMC snappin, locate the new certificate and scroll down in the list of properties to see the thumbprint.
- Run Set-AdfsSslCertificate -Thumbprint xxxxthumbprintofthenewsslcertxxxxx (without spaces).
- Restart the ADFS service
Optionally when using Web Application Proxy(s):
- Copy and import the new certificate to the Web Application Proxy/Proxies which are not domain joined. Make sure the certificate is imported into the Machine Personal Store.
- Switch the certificate on the Web Application Proxy, I personally did this by reinstalling the Web Application Proxy (requires a reboot) but it’s much easier to use the “Set-WebApplicationProxySslCertificate” cmdlet.
Consider leaving a reply in case this post helped you. Thanks!