Hyper-V How To: Understand Hyper-V Architecture
Understanding the Hyper-V architecture can help you understand how to better secure Hyper-V. This excerpt from the Hyper-V Security Guide helps to explain:
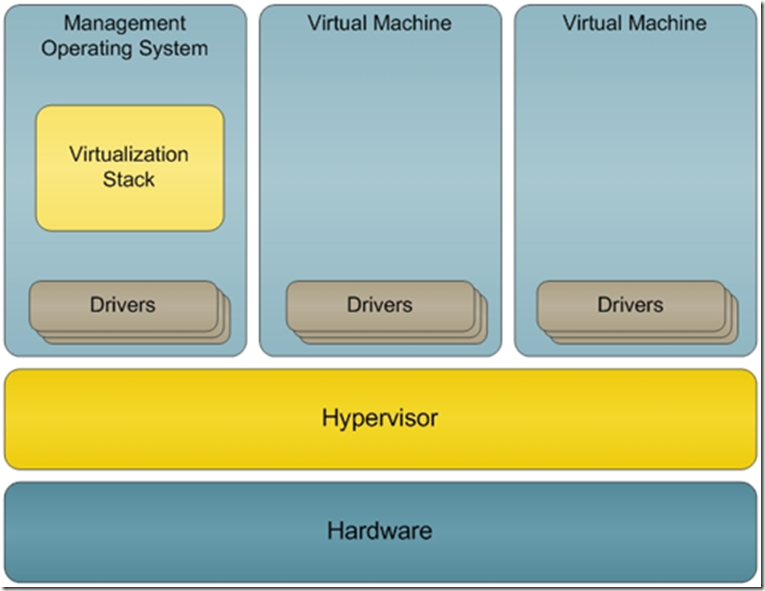
“After you install the Hyper-V role, all of the operating system instances on the physical computer run as virtual machines. Even the instance of Windows Server 2008 that you use to create and manage the virtual machines is a virtual machine; this instance is the management operating system. You use the management operating system specifically to create and manage virtual machines.
Hyper-V uses a microkernelized approach in which the hypervisor is very small and allows no third-party code to run within it. The hypervisor, which is a core component of Hyper-V, is a thin layer of software between the hardware and the operating system. The hypervisor allows multiple operating systems to run unmodified on a single physical computer at the same time. Because any unknown security vulnerabilities included in Hyper-V could compromise the security of the management operating system and the virtual machines, Microsoft has carefully reviewed and tested the Hyper-V source code to minimize this risk. In addition, the hypervisor component was designed with minimal configuration requirements to reduce its complexity and attack surface. (For more information on the Hyper-V virtualization architecture, see An Introduction to Hyper-V in Windows Server 2008 on Microsoft TechNet.)”