Hyper-V Security How to: Use BitLocker to Protect Your VMs
Windows Server 2008 Hyper-V and BitLocker Drive Encryption was recently published to the download center, but some folks are having trouble accessing it (it seems there is a lot of interest in all things Hyper-V). Here are the procedures in the doc to tide you over till your download comes through:
Deployment Overview
- Install Windows Server 2008.
- Install the Hyper-V role and the BitLocker feature.
- Configure the system volume for BitLocker.
- Turn on BitLocker and encrypt the operating system and data volumes.
- Create new virtual machines.
Deployment Steps
For more information on to partition a hard disk drive for BitLocker Drive Encryption, see https://technet2.microsoft.com/WindowsServer2008/en/library/c61f2a12-8ae6-4957-b031-97b4d762cf311033.mspx#BKMK_S1. NOTE: BitLocker requires that your TPM module is enabled and working. See Windows Trusted Platform Module Management Step-by-Step Guide.
Step 1
Install Windows Server 2008.
Step 2
Install the Hyper-V role and the BitLocker feature.
- Start Server Manager, navigate to the Device Manager tab, and verify that the prerequisite Trusted Platform Module (TPM) is present.
- In Server Manager, click Add Roles.
- Read the directions, and then click Next to continue.
- Select the Hyper-V role check box, and then click Next to continue.
- Read the directions, and then click Next to continue.
- Select the appropriate networking interface check boxes to create virtual networks, and then click Next to continue.
- To begin installation of the Hyper-V role, click Install.
- After installation of the Hyper-V role is complete, click Yes to restart your server.
- After reboot, start Server Manager and verify that the Hyper-V role has been installed successfully.
- In Server Manager, click Add Features.
- Select the BitLocker Drive Encryption check box, and then click Next to continue.
- To begin installation of the BitLocker Drive Encryption feature, click Install.
- After the BitLocker Drive Encryption initial installation phase is complete, click Yes to restart your server.
NOTE: After reboot, log on and Server Manager will be automatically started to complete the BitLocker Drive Encryption installation.
NOTE: Verify that the installation has been successful.
Now you must configure the system volume for BitLocker before turning on the installed BitLocker Drive Encryption from Control Panel.
Step 3
Download and read detailed information and instructions for the BitLocker Drive Preparation Tool at:
https://support.microsoft.com/default.aspx/kb/930063.
Download and install the installation kit from the Microsoft download center at:
https://www.microsoft.com/downloads/details.aspx?FamilyID=320b9aa9-47e8-44f9-b8d0-4d7d6a75add0&DisplayLang=en
- Click BitLocker Drive Preparation Tool.
- Click I Accept to accept the software license terms.
- Read the warnings below Caution, follow them as appropriate, and then click Continue.
- After completion, the BitLocker Drive Preparation Tool requires you to restart the system. To reboot, click Finish.
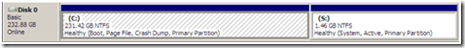
Note: After reboot, the system volume (drive S) and the operating system volume (drive C) are separate, as shown in the following screenshot.
Step 4
Turn on BitLocker and encrypt the operating system and data volumes.
- Start Control Panel for BitLocker Drive Encryption.
- Click Turn On BitLocker.
- Click Continue with BitLocker Drive Encryption.
- Follow the steps to turn on the Trusted Platform Module (TPM) security hardware. The system firmware performs a Physical Presence Interface check. This is a form of authorization validation before the TPM ownership is allowed on this system
- After the TPM is initialized successfully, you must save the recovery password before you encrypt the operating system volume and any optional data volumes.
- To start encrypting the operating system volume, click Encrypt.
- Wait for the encryption of the operating system volume to complete, then repeat this task for the data volumes.
NOTE: If you have many data volumes to encrypt, consider using the manage-bde.wsf script. The manage-bde.wsf syntax is included in the "Windows BitLocker Drive Encryption Design Guide" and the "Windows BitLocker Deployment Guide," which are available from the Microsoft Download Center at go.microsoft.com/fwlink/?LinkId=115215.
For example, to mark data volume P: so that it must be manually unlocked, use the following command:
manage-bde.wsf –autounlock –disable P:
To turn autounlock back on for P:, use:
manage-bde.wsf –autounlock –enable P:
To view more detailed Help for this script, type the following command:
cscript.exe %windir%\system32\ manage-bde.wsf -h
Step 5
Create new virtual machines.