Configuring DirectAccess to Support Citrix Connections
We’ve seen a lot of questions on how to get the Citrix client to work with DirectAccess. The following provide some information and procedures that may work to get the Citrix client to work over DirectAccess.
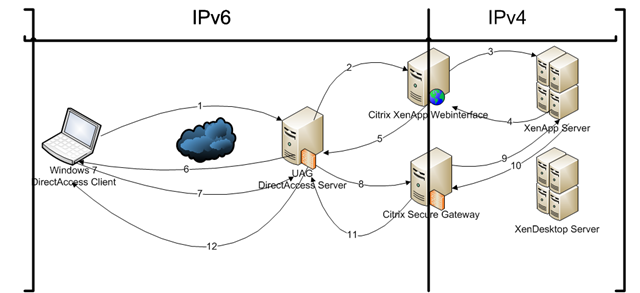
The Citrix client can use IPv6 to connect to one type of server only: the Citrix Secure Gateway (CSG). In order for the Citrix client to work over DA, you need to:
- Install the CSG on the internal network
- Configure the Citrix Web Interface to use CSG
- Create an NRPT rule that uses the internal DNS server directly instead of going through the UAG DNS64
A key issue to be aware of is that Citrix clients do not support IPv6, with the exception of connecting to the Citrix Secure Gateway (CSG). Although it can sit directly on the internet, it’s preferred that it be put it on the LAN, with an IPv6 address (either native or ISATAP). Here’s how it works:
- The client establishes a DA connection
- The user uses the browser to bring up the Citrix Web Interface and authenticates to it.
- The Web Interface compiles a list of allowed applications and presents them to the user.
- The user clicks an icon that represents an application and the Web Interface invokes the client side Citrix plug-in
- The Citrix plug-in initiates a session with the server through the CSG according to the connection information supplied by the Web Interface. In this case this includes information about the SSLProxy (CSG) and Secure ticket authority.
In configuring the CSG, note should be taken in https://support.citrix.com/proddocs/index.jsp?lang=en&topic=/xenapp5fp-w2k8/sg-features-v2.html to use the IPv6 address to listen on.
Note:
The client plug-in needs to be version 11 and above and must trust the CSG’s server certificate.
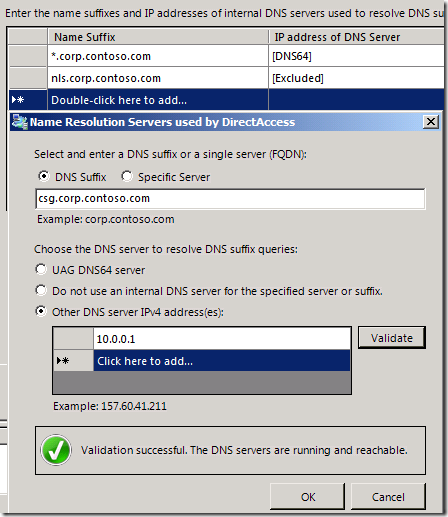
Finally, it appears that even though the Citrix client is able to connect over IPv6 to the CSG, it needs the CSG’s name to resolve to both the IPv4 address and the IPv6 address. For this to happen, we need to exempt the name of the CSG from the NRPT in the UAG DirectAccess configuration so that it uses an internal DNS server instead of the UAG DNS64. This is done by entering the IP address of the internal DNS server. Not doing this will default to the UAG DirectAccess server’s DNS64 services, which never returns IPv4 addresses (it always returns a NAT64 address), causing issues for the Citrix client.
An example of how you can configure this is included in the figure below.
HTH,
Tom
Tom Shinder
tomsh@microsoft.com
Microsoft DAIP iX/SCD iX
UAG Direct Access/Anywhere Access Group (AAG)
The “Edge Man” blog (DA all the time): https://blogs.technet.com/tomshinder/default.aspx
Follow me on Twitter: https://twitter.com/tshinder
Facebook: https://www.facebook.com/tshinder