How to Configure UAG to Publish Your Private Certificate Revocation List
In order for SSTP (Secure Socket Tunneling Protocol) and DirectAccess to work properly the SSTP and DirectAccess client must have access to the CRL (Certificate Revocation List) of the server certificate (if you are using Client Certificate or Smart Card authentication you will also need access from the client to the CRL)
If you are using internal Microsoft Certificate Authority (CA) you can publish the CRL through UAG based on the following procedures:
Important Note:
If you are using Microsoft Certificate Authority (CA) make sure the Root CA certificate (If you are using in intermediate CA, also include the intermediate CA certificate) is located in the Trusted Root Certification Authorities of the Local Computer Store
Steps to Publishing the CRL through UAG
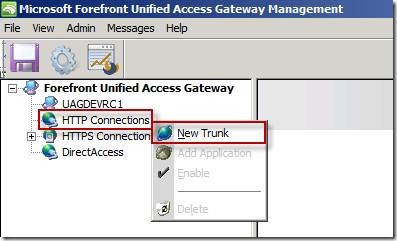
Open UAG management Console, navigate to HTTP Connections, right click, and choose New Trunk
On the Welcome to the Create Trunk Wizard page click Next.
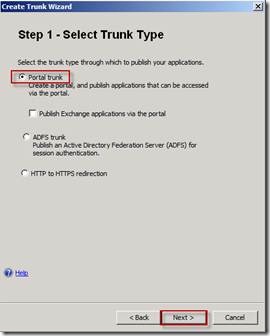
On the Step 1 – Select Trunk Type page, select the Portal trunk option and click Next.
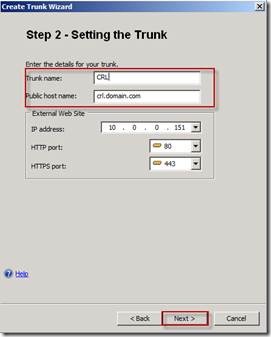
On the Step 2 – Setting the Trunk page, enter the Trunk name and enter the Public host name, this part is very important! You must enter the exact URL that you configured in the CDP (CRL Distribution Point) setting on your certificates, then click Next.
Note:
External clients must be able to resolve the public host name
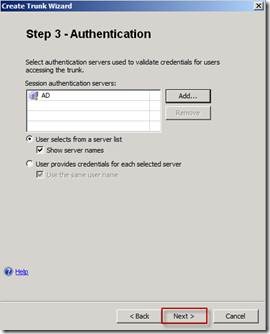
On the Step 3 - Authentication page, choose any authentication repository (this is not relevant because in next phases we will disable the authentication for this Trunk because access to CRL doesn't require authentication) then click Next.
On the Step 4 – Endpoint Security page, click Next (you will disable Endpoint Security for this Trunk later so the choice made her is immaterial).
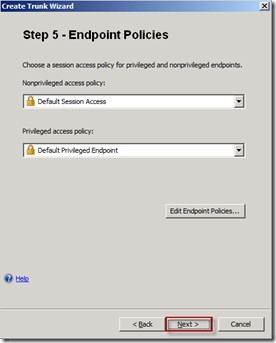
On the Step 5 Endpoint Policies page click Next.
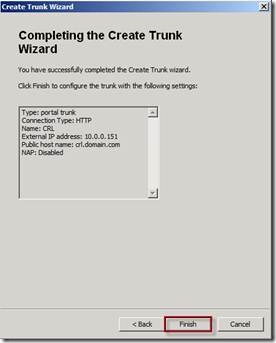
On the Completing the Create Trunk Wizard page click Finish.
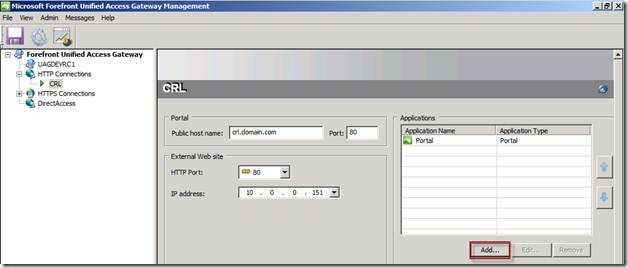
Configure the New Trunk
Now we will configure an Other Web Application (application specific hostname) application in the new trunk to publish the internal CRL.
In the UAG management console click Add.
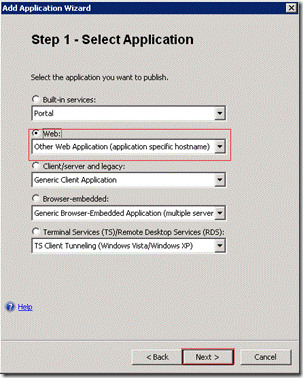
On the Step 1 – Select Application page select the Web option and then select the Other Web Application (application specific hostname) option from the drop down list. Click Next.
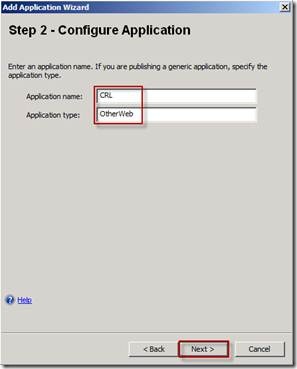
On the Step 2 – Configure Application page enter the Application name and in the Application type text box, enter OtherWeb, then click Next.
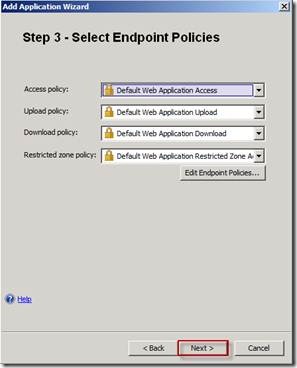
On the Step 3 – Select Endpoint Policies page click Next.
On the Step 4 – Deploying an Application page click Next.
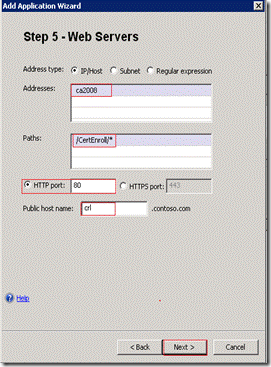
On the Step 5 – Web Servers page, in the Addresses text box, enter the name on your internal IIS server that hosts the CRL. Change Paths to the path defined for CRL Distribution Point, for example “/CertEnroll/* (your certificate distribution point will likely have a different name, enter the name that you have defined for your CDP). Define the Public host name as configured in the CDP (CRL distribution point). This name should be the same Public host name defined for the trunk. Click Next.
Note:
External clients should be able to resolve this name
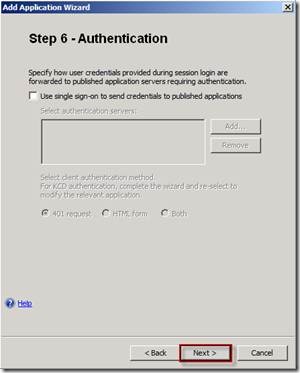
On the Step 6 - Authentication page click Next.
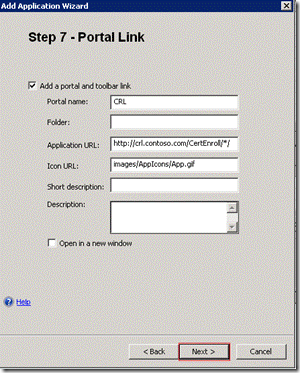
On the Step 7 – Portal Link page click Next.
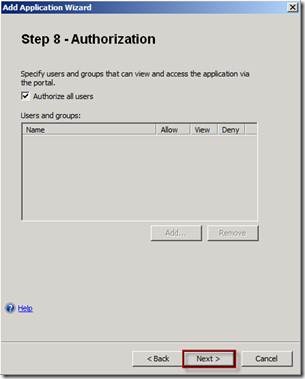
On the Step 8 - Authorization page click Next.
On the Completing the Add Application Wizard page, click Finish.
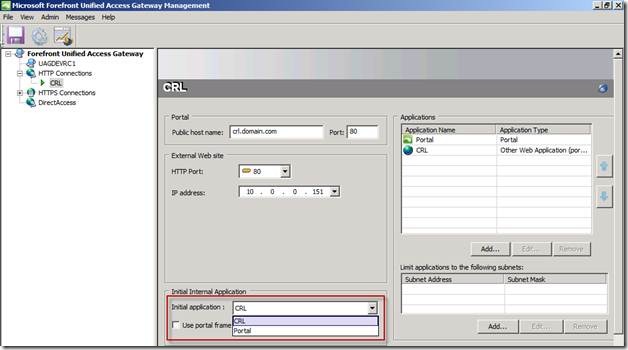
In the UAG Management Console navigate to the Initial application and choose the application you created (this will allow access directly to the CRL and not through the UAG default portal).
In the UAG Management Console navigate to Trunk Configuration and choose Configure
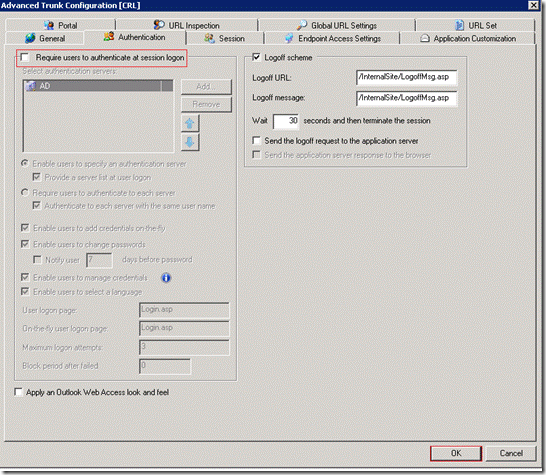
Disable Require users to authenticate at session logon onthe Authentication tab in the Advanced Trunk Configuration dialog box.
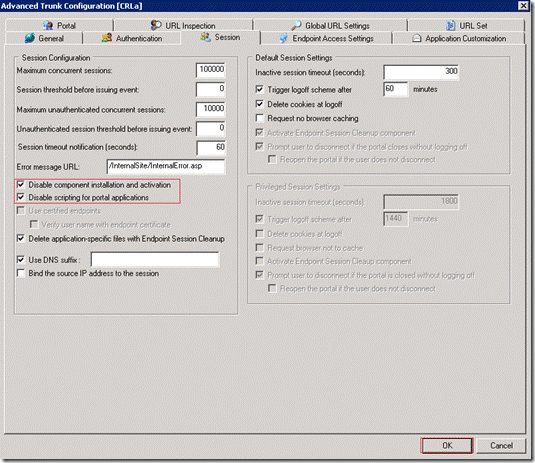
Enable the option “Disable component installation and activation” on Sessions tab of Advanced Trunk Configuration dialog box. You need to do this because UAG client components are not required for publishing CRL. Also enable the option “Disable scripting for portal applications”
This article was originally written by Tarun Sachdeva, Sr. Support Engineer.
Tom Shinder
tomsh@microsoft.com
Microsoft ISD iX/SCD iX
UAG Direct Access/Anywhere Access Group (AAG)
The “Edge Man” blog (DA all the time): https://blogs.technet.com/tomshinder/default.aspx
Follow me on Twitter: https://twitter.com/tshinder
Facebook: https://www.facebook.com/tshinder