Tip of the Day: DNS Recursion Policies
Today’s Tip…
Previous DNS Policy tips discussed two uses for Query Resolution Policy;
- Location Aware Response policies for authoritative queries, and
- Selective-Filtering for non-authoritative queries.
Those are just two from the list of potential policy scenarios and I’m itching to share information on policy processing behaviors and troubleshooting, but feel compelled to share just one more variation, the Recursion Policy.
Recursion Policies
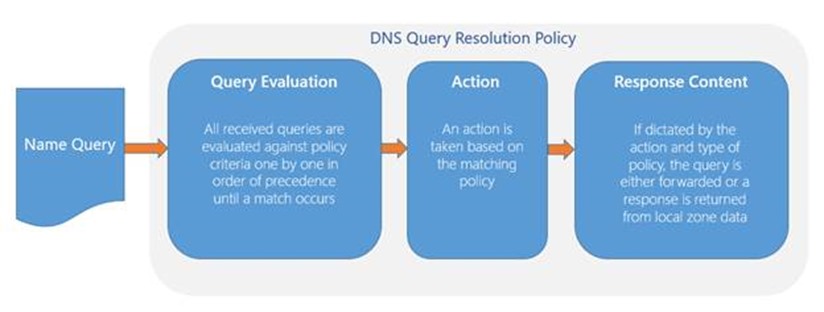
Recursion Policies provides DNS administrators granular control over recursion for non-authoritative queries using essentially the same logic as in our previous examples. Recall the particulars of policy operations:
- A query is received by the DNS server.
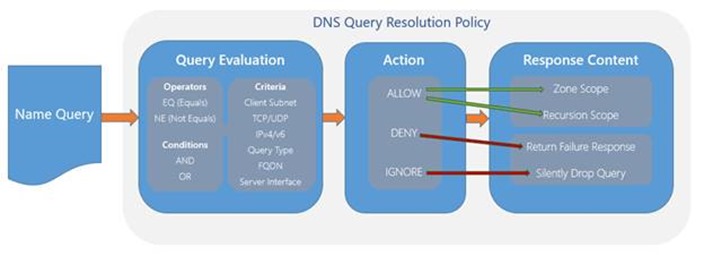
- It is evaluated against the criteria specified in the list of policies until a match is found. To refresh, valid criteria includes:
- Client Subnet
- TCP/UDP Transport Protocols
- IPv4/IPv6 Protocols
- The FQDN in the request
- Query Type
- IP of the server interface on which the query was received
- Time-of-Day
- When a policy is matched, an action of IGNORE, DENY, or ALLOW is applied
- If the action is ALLOW, response content is returned from a specified source
The Response Content is where recursion policies differ from authoritative query-response policies. Where an authoritative response policy makes use of a Zone Scope to provide the appropriate answer, recursion policies make use of a Recursion Scope, which contains settings to control how recursion is handled, including:
- Whether recursion is enabled, and if so
- To what forwarder(s) to send the query
Configuring a Recursion Scope
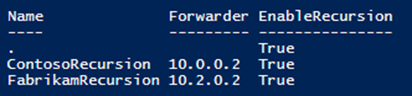
Before creating the policy, one or more recursion scopes must be created. For example:
Add-DnsServerRecursionScope -Name “InternalRecursion" –Forwarder 10.0.0.2 –EnableRecursion $True
The above command creates a scope called “InternalRecursion” in which recursion is enabled (-EnableRecursion $True), and name-requests forwarded to the DNS server with IP 10.0.0.2 (-Forwarder 10.0.0.2)
Note: Multiple forwarders can be specified simply by using comma separated values.
Configuring a Recursion Policy
In the DNS policy, we need to reference the Recursion Scope using the -ApplyOnRecursion and -RecursionScope parameters. Consider the following example:
Add-DnsServerQueryResolutionPolicy -Name “InternalClientRecursionPolicy" -Action ALLOW -ApplyOnRecursion -RecursionScope "InternalRecursion" -ServerInterfaceIP "eq,192.168.1.1“
In the above example, any query received by the DNS server on its 192.168.1.1 interface will be forwarded to the DNS Server identified in the “InternalRecursion” scope. A use-case in this scenario might be to enable recursion for internal clients, while locking down recursion for queries from other networks. Very handy to help mitigate the risk of certain DNS-centric exploits.
What about the Legacy Recursion Settings
In the context of DNS policy, forwarding settings exposed through the DNS server properties Forwarders tab (accessible using the DNS management console) are referred to as the Default Recursion Scope. For purposes of policy, it can be identified by its scope name, “.”.
Final Thoughts
Remember the spiffy graphic above? Hopefully the following fills in its blanks a bit and serves as handy reference, helping in the recall of concepts discussed in the January set of DNS Policy tips.