(RDS) Tip of the Day: Shadow IT– Learn how to get control now
Today’s Tip…
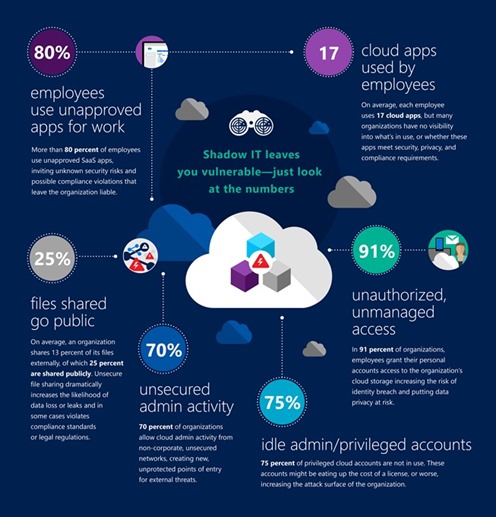
Shadow IT is here and it’s a threat to your organization. What is Shadow IT? It’s when your employees use unapproved devices, SaaS apps, or any other type of technology – without your consent- for getting their work done. As the traditional solutions do not have visibility to users’ actions, unfortunately, Shadow IT is neglected or ignored. For example, there are several organizations and IT teams that claim they are not in the cloud. But, the reality is, their employees already are. A study shows that more than 80% of employees admit to using non-approved SaaS apps for convenience, to be more productive, or because they are easier to use. Unfortunately, your employees are unknowingly putting your company at risk and could be maliciously sharing files and exfiltrating sensitive data. It is smart to get a handle on this now.
To be provocative – some argue that SaaS and Cloud App Security (CAS) is much harder than classic network-based security. Why, you may ask? Because employees can do what they want, from any device and from anywhere. This undermines the basic assumptions of the security models used today by IT teams. Network security tools assume employees are using the corporate network, while end-point security tools assume they are using a corporate device. But, if they can use any app, from anywhere in the world, none of these assumptions apply.
Cloud Security is an equally important control plane to lock down as part of your defense in-depth strategy. Additionally, it will help you get compliant with the new Global Data Protection Regulation (GDPR), being enforced by May 2018.
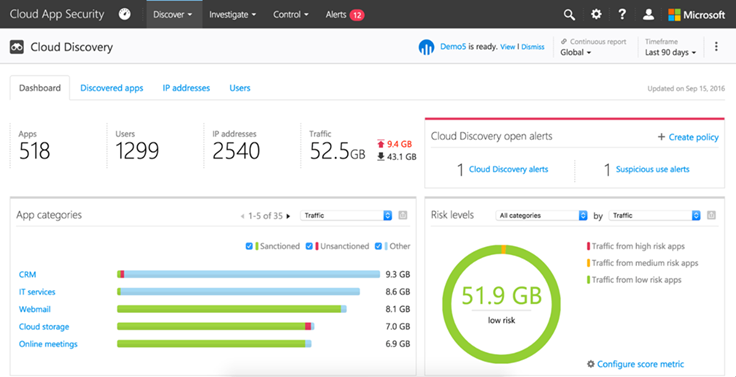
CAS, Microsoft’s CASB, is agentless, simple, and intuitive to deploy and manage. The first step is to sign up for the trial and turn on discovery. From there, we’ll provide you with a detailed report showing the apps in use, from which IPs and which users, along with a risk score based on an algorithm we’ve built for over 13,000 applications. Following the discovery process, enable threat protection and implement controls. Set policies for your organization by sanctioning applications via our API connectors. CAS has global admin privileges for the dominant SaaS apps including Salesforce, Box, DropBox, Google Apps, AWS, ServiceNow and others – and of course Office 365.
Just last week we enabled a large customer with 85,000 employees to use CAS through the API connectors for Office 365 for OneDrive, Exchange, Salesforce, and Box in a matter of minutes. They lit up with how easy it was to use. And now they can begin monitoring which users are downloading/sharing content and when. They can monitor the activities of the administrators as well. This is huge progress that significantly increases their security posture.
Microsoft’s integration of the Adallom acquisition is first party and, quite simply, better, and here’s why: We are part of the same organization. CAS engineering and Office engineering teams work together to ensure we provide a more secure experience for Office 365.
As a first-party CASB integrated into Office 365:
- We don’t require a service account to be connected to Office 365, which increases security.
- We don’t have to worry about API throttling!
- MCAS is integrated into the Office 365 Portal under the security and compliance center.
- We include access to Microsoft threat intelligence integration and will send reports to our customers.
And broaden it to other apps in your environment following Office 365 to put controls in place. The top applications we see customers using are Salesforce, ServiceNow and Box/Dropbox.
Finally, Microsoft’s CAS is the only CASB in the market that seamlessly integrates with file-level encryption technologies such as Azure Information Protection as well as Azure Active Directory controls like conditional access. CAS is not just another CASB solution. Our goal is to provide not just another point security solution, but rather a holistic and innovative security approach with Enterprise Mobility + Security (EMS). This helps you protect your users, devices, apps, and data both on-premises and in the cloud.
Discover the cloud apps in your organization and start controlling them today! To get started, please visit the Cloud App Security website.
References:
- “Shadow IT– Learn how to get control now” - https://blogs.technet.microsoft.com/enterprisemobility/2016/11/22/shadow-it-leaves-you-vulnerable-learn-how-to-get-control-now/
- “More than 80 per cent of employees use 'non-approved' SaaS apps- https://www.computing.co.uk/ctg/news/2321750/more-than-80-per-cent-of-employees-use-non-approved-saas-apps-report
- “Microsoft Cloud App Security” - https://www.microsoft.com/en-us/cloud-platform/cloud-app-security