Tip of the Day: More Message Analyzer 1.1: Viewing Network Virtualization Traffic
Today’s (Networking) Tip…
Did you know that Message Analyzer includes parsers enabling you to view Network Virtualization traffic?
Background
Virtual Networking operates by running a virtual tenant network ( the Customer Address space) on top of a private cloud or hosting provider physical network (the Provider Address space). If traffic from a tenant virtual machine on one Hyper-V server to reach a destination tenant virtual machine hosted on a second Hyper-V server, the frame must be encapsulated (tunneled) to traverse the provider network underneath.
The protocol that provides this encapsulation header is GRE.
Problem
Encapsulated payload (in this case the whole of the tenant network packet) is typically not visible in a host network trace.
NOTE: Of course, customer address space traffic WOULD be visible in a capture taken from a VM on the virtual network trace itself. But for the purposes of this example we are interested to see what happens to the encapsulated v-net frames as it traverses the physical network.
Solution
Message Analyzer!
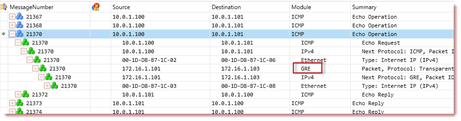
The following figure shows an ICMP operation from a virtual machine (on the 10.x.x.x network) as it traverses the provider network (the 172.16.x.x) network to reach a remote destination. Note the module indicating GRE encapsulation is in use.
Fig. 1: The Analysis Grid
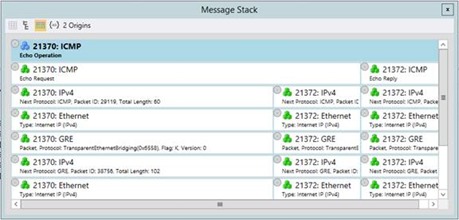
In a tip earlier in the week we explored the different views available for the Message Stack tool window. Let's see what this example looks like in the Visual Stack view.
Fig. 2: Message Stack Window