Scope-level Link layer filtering using DHCP Policies in Windows Server 2012
Introduction
Link-layer filtering was a DHCP feature introduced in Windows Server 2008 R2 where one could allow or restrict access to clients based on their MAC address. However the caveat in this feature was that this was possible only at the server level. One of the frequent asks we‘ve had since is a desire for scope level link-layer filtering.
With the new infrastructure for DHCP policies available in Windows Server 2012, this requirement can now be fulfilled. Here’s how!
Creating a scope-based allow-filter list using Policies
Consider a scenario where an administrator needs to allow only a specific set of computers or devices on a subnet. In order to control which clients can be allowed on a subnet, an administrator can constrain the DHCP server to providing IP addresses to a specific set of known clients where the clients which are allowed on a subnet are known a-priori.
To realize this, the administrator can create a policy inside the scope on the DHCP server for this subnet. The conditions of the policy will be MAC-address = a1, a2, … , an (or more specifically MAC-address = a1 OR MAC-address = a2 … OR MAC-address = an ) and the IP-range of the policy will be the entire scope IP range. Here, a1 through an are the MAC addresses of the clients which are allowed on the subnet. A step-by-step guide for creating DHCP policies is here.
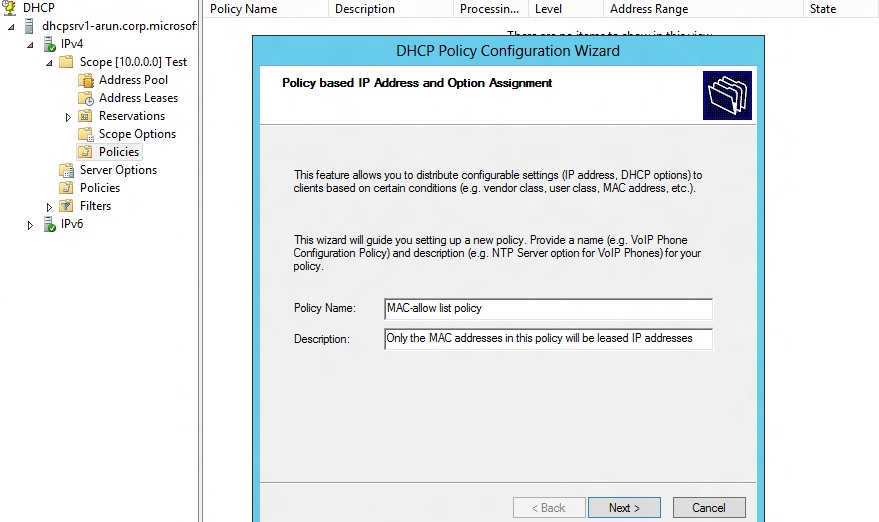
The policy can be created by going to the Policies node under the relevant scope in DHCP MMC and selecting “New Policy”.
Figure 1: Policies Wizard - First Page
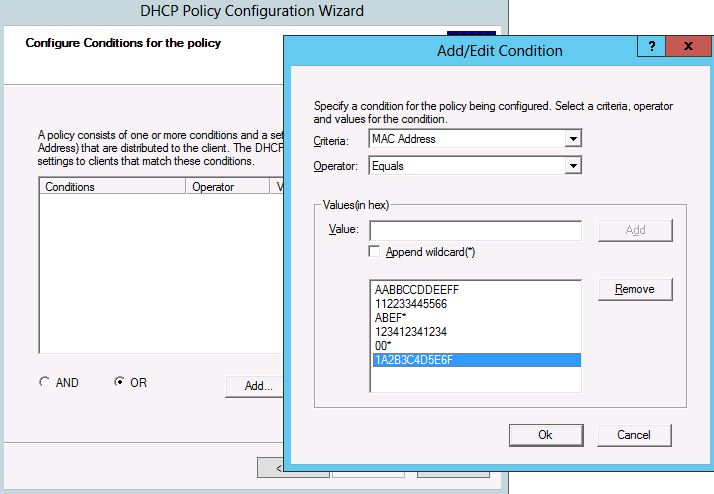
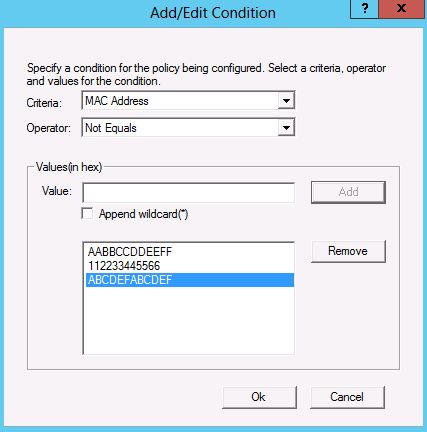
On the conditions page, click on ‘Add’ and in the dialog that pops up, choose the MAC address as the criteria and make sure that the operator chosen is “Equals”. Now add all the MAC-addresses in the list box for values. Note that this also has support for wildcards should you need it. You could select a prefixed MAC address and append a wild card along with selecting individual MAC-addresses.
Figure 2: Policy Conditions Dialog - Addition of MAC-addresses to the list box.
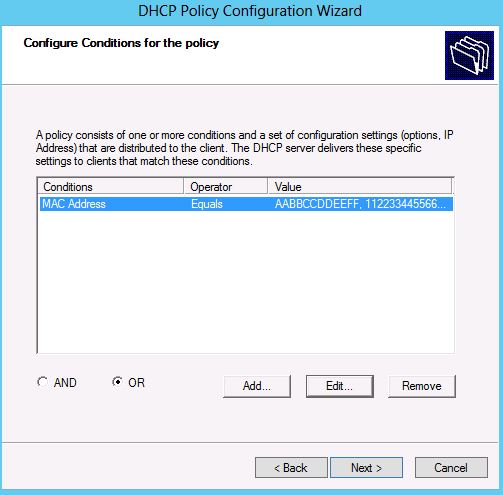
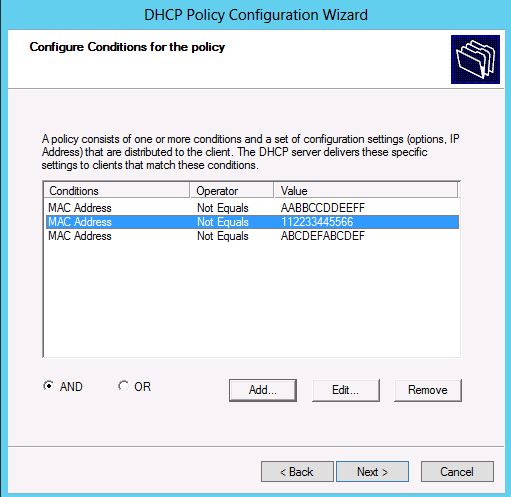
This selection is equivalent to the condition MAC-address = a1, a2, … , an. The conditions page would now look as shown in Figure 3.
Figure 3: Conditions Page in Policy configuration wizard after addition of MAC-addresses to the list box
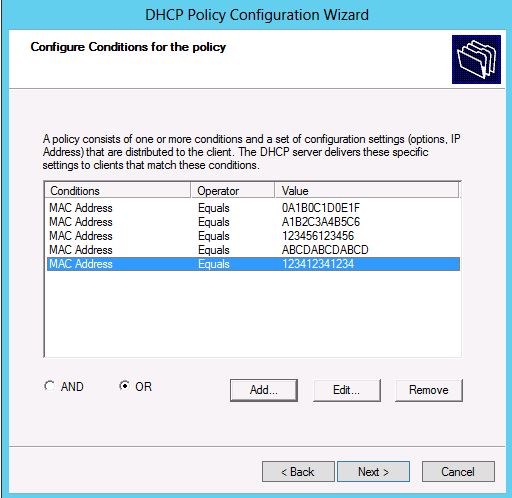
An alternate way to do the same thing is, make sure that the “OR” radio button is selected on the conditions page since we wish to create an “OR” based policy. Now click on ‘Add’ and choose the MAC address as the criteria in the dialog that pops up and add the first MAC-address as the condition.
Figure 4: Conditions Page in Policy configuration wizard after selection of MAC-addresses
Do the same for all MAC-addresses to be added to the allow list for this scope. Eventually the conditions page of the wizard would look something like the snapshot in Figure 4.
Both these above ways of selecting conditions will fulfill the requirement of creating a policy with condition MAC-address = a1 OR MAC-address = a2 … OR MAC-address = an.
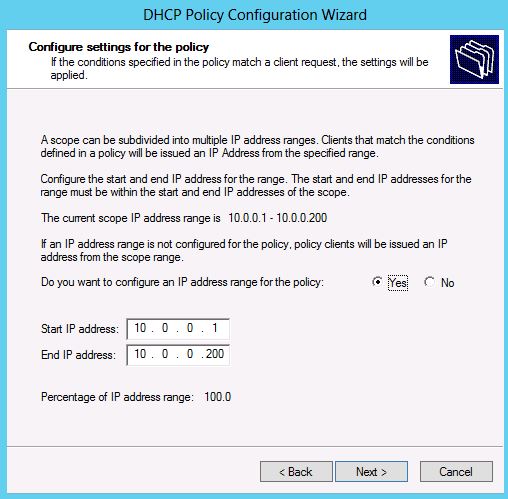
On the next IP ranges page, choose the start and end range to be the start and end IP address of the range of the scope itself such that the “percentage of IP address range” should show up as 100. By choosing the entire scope range for this policy, we are essentially ensuring that only a client matching this policy (matching one of the MAC-addresses) will be leased an IP-address from this scope. A client whose MAC address does not match any of the MAC addresses specified in the policy will not be able to get an IP address lease from the DHCP server. Had we not chosen the entire scope range for this policy, an unwanted client could get an address from the remaining part of the scope range.
Figure 5: Policy configuration page - IP Address range selection page
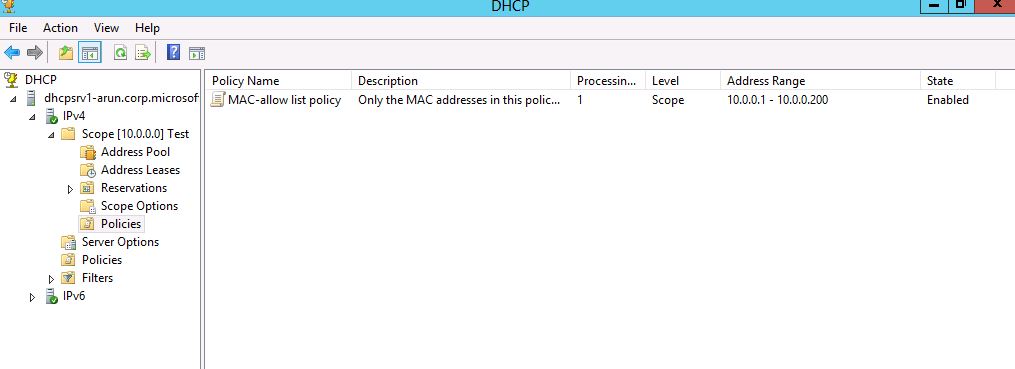
Follow the subsequent step of configuring options if needed and go to summary page and complete the creation of the policy. The results pane after the policy creation would look like this.
Figure 6: Results pane in DHCP MMC
You have now successfully created and configured a policy for this scope such that only the computers/devices having one of the specified MAC-addresses will be able to get an IP address from this scope.
Creating a scope-based deny-filter list using Policies
In case you wish to configure a deny list instead of an allow list, where the MAC-addresses specified will be blocked and not be leased an IP address from the given scope, the only modification in the above process is the conditions of the policy.
The conditions of the policy should now be MAC-address != a1, a2, … , an (or MAC-address != a1 AND MAC-address != a2 … AND MAC-address != an ) .
Again, one can do this using any of the following ways. Add all required MAC-Addresses in the list box as
shown below making sure that the operator chosen is “Not Equals”.
Figure 7: Addition of Deny list MAC-addresses to the Policy Conditions Dialog
The other approach is to MAC-Addresses individually in separate conditions and the conditions page will look as follows. The operator chosen will be AND.
Figure 8: Addition of Deny list MAC-addresses to Policy Conditions
The conditions along with the IP range configured (the whole scope range as in the previous case) for this policy will ensure that in case the incoming client has a MAC-address which is not one of the addresses in the list; it should be leased out an address from this scope. However a client which has a MAC-address same as one present in the policy, it will not get an address from this DHCP scope.
Limitation
Policy IP-ranges cannot overlap and an IP address cannot be a part of two policies. Hence using the entire scope range for this policy implies that you can’t create another IP-range based policy in this scope. However you can still create multiple policies (without configuring IP ranges on them) within this scope and use those to give out different sets of DHCP options to different client based on some criteria.
Using powershell to create scope-based policy for Link-layer filtering
Since there could be a large number of MAC-addresses that need to be added to such a list, doing this operation via UI might be a bit cumbersome. Here is a link to a script that takes as input: a file which contains the list of MAC-addresses (line separated), the scope ID, and whether this list is meant to be used as an allow list or deny list. This script will create the appropriate required policy for you.
Other Links
- About DHCP policies
- Step-by-step to configure DHCP policies
- Setting up DHCP Policies for Virtual Machines
- Set different lease durations for different device types
Team DHCP