Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Configuration Manager Archive
URL
Copy
Options
Author
invalid author
Searching
# of articles
Labels
Clear
Clear selected
adk
Alerts
Android
application compatibility
Application Management
application model
app model
asset intelligence
azure rights management services
Best Practices
brad anderson
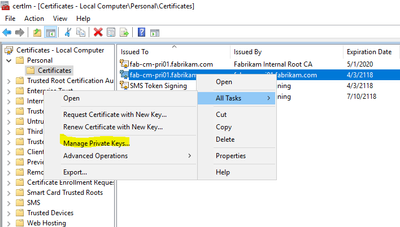
Certificates
client
client deployment
Cloud
cm 1511
CM 2007
CM 2012
cm cb
cm vnext technical preview
Conditional Access
ConfigMgr
configmgr 25
configpacks
Configuration Manager
cumulative updates
customer feedback
dcm
Deployment
Endpoint protection
Exchange
Extensions
featured
fep 2010
general information
hotfixes
Hybrid
hybrid cloud
iOS
Known Issue
linux
linuxunix
logging
mac address
mac os
MAM
MDM
mdt
mdt 2013
Messaging
Microsoft Intune
microsoft sql server 2008 r2
Migrate
mms
Mobile Device Management
Modern Apps
mui
nic
Office 365
on prem
oob
Operating System Deployment
osd
PKI
PowerShell
Public Preview
PXE
r2
regional settings
scap
SCCM
scup
SDK
Security
Servicing
settings management
signing
SMS
SMSTS.log
software updates
sp1
sp2
supported configurations
Surface Pro 3
System Center
System Center Configuration Manager
system uuid
task sequences
tools
Upgrade
usb ethernet adapter
Virtualization
win2k8
win2k8r2
Windows
Windows 10
windows 10 1507
windows 10 1511
windows 10 1607
windows 8 1
windows azure
windows intune
Windows Phone
Windows Server
WSUS
wufb
- Home
- Microsoft Intune and Configuration Manager
- Configuration Manager Archive
Options
- Mark all as New
- Mark all as Read
- Pin this item to the top
- Subscribe
- Bookmark
- Subscribe to RSS Feed
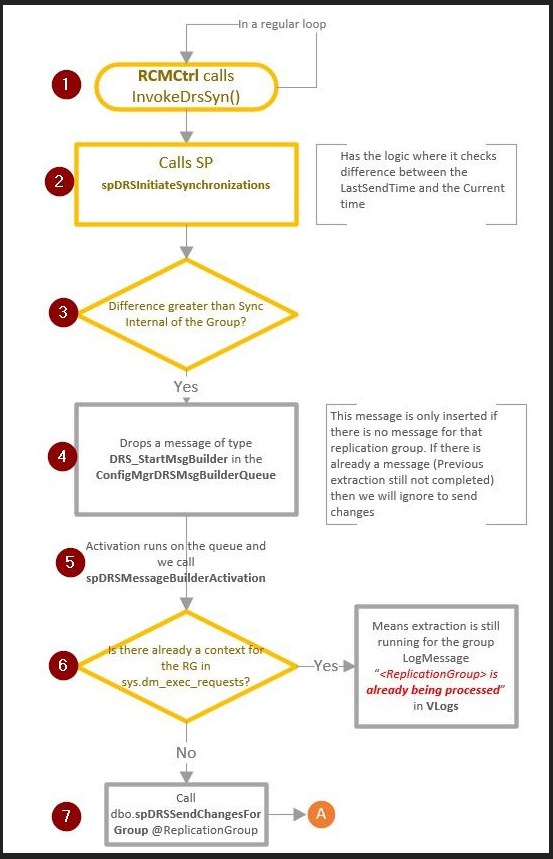





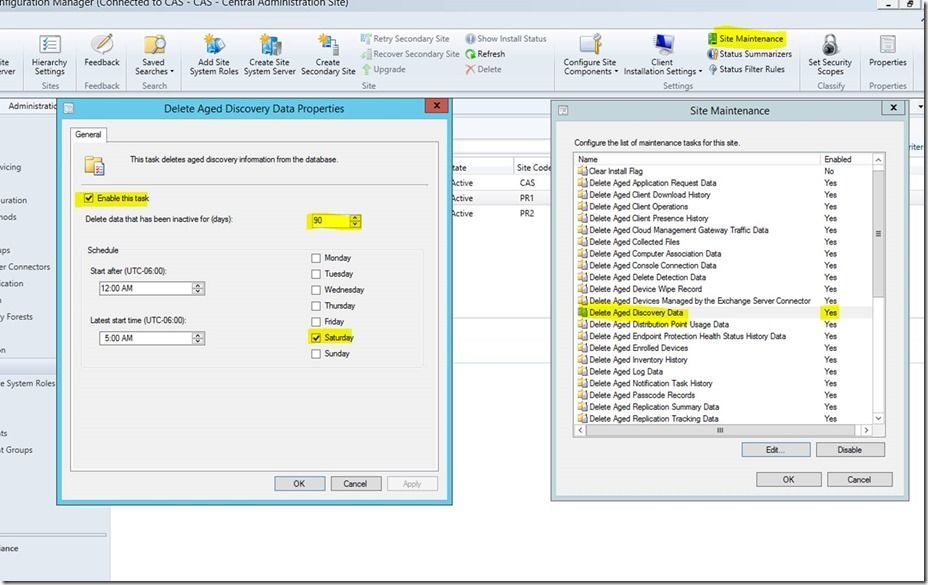

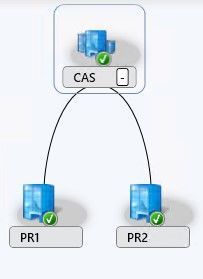










Latest Comments