Improved cryptography infrastructure and the June 2013 bulletins
It was just over one year ago, May 28, 2012, to be exact, that I transitioned from running active MSRC cases and writing bulletins to my current role managing software security incidents. A lot has changed in that year - and I’ve dealt with some interesting issues during my tenure - but our goal of providing the best customer protections possible remains a constant. For example, in June 2012, we introduced a new feature to automatically update the Certificate Trust List (CTL), allowing us to quickly move untrusted or compromised certificates to the CTL without customer interaction. Since this feature works by checking for new updates over the internet, enterprises that filter this type of network traffic are not able to take full advantage of this feature.
Today we are building on that functionality by releasing an update, in the form of Security Advisory 2854544, which gives enterprises more options for managing their private public key infrastructure (PKI) environments. This functionality, initially built into Windows 8, Windows Server 2012 and Windows RT, is now available for Windows Vista through Windows 7. Over the coming months, we’ll be rolling out additional updates to this advisory - all aimed at bolstering Windows’ cryptography and certificate-handling infrastructure. Our efforts here aren’t in response to any specific incident; it’s the continuing evolution of how we handle digital certificates to ensure the safest possible computing environment for our customers.
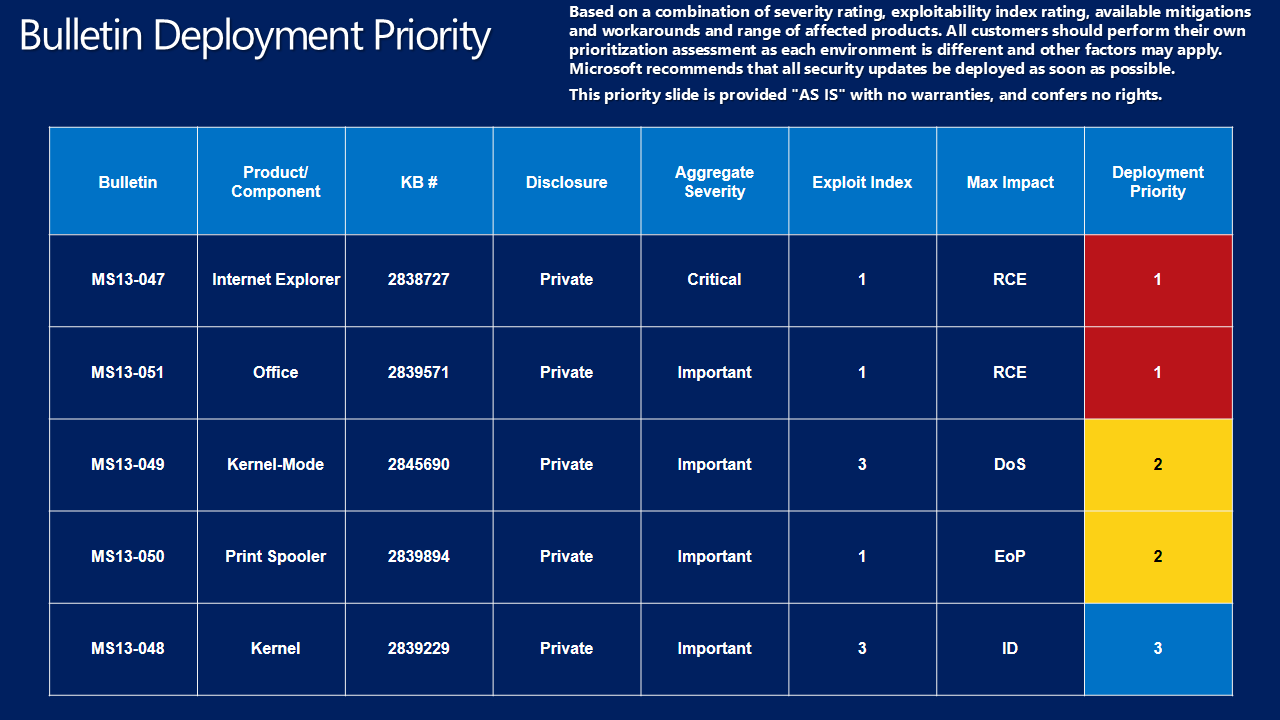
Speaking of safer computing, let’s talk about the five bulletins we released today - one Critical and four Important, addressing 23 vulnerabilities in Microsoft Windows, Office and Internet Explorer. For those who need to prioritize deployment, we recommend focusing on MS13-047 and MS13-051 first. As always, customers should deploy all security updates as soon as possible. Our Bulletin Deployment Priority guidance is below to further assist in deployment planning (click for larger view).
MS13-047 | Cumulative Security Update for Internet Explorer
This security update resolves 18 issues in Internet Explorer that could allow remote code execution if a customer views a specially crafted Web page using the browser. An attacker who successfully exploited these vulnerabilities could gain the same user rights as the current administrator. This security update is rated Critical for all versions of Internet Explorer, on all supported releases of Microsoft Windows. These issues were privately disclosed and we have not detected any attacks or customer impact.
MS13-051 | Vulnerability in Microsoft Office Could Allow Remote Code Execution
This security update resolves one privately reported vulnerability in Microsoft Office. The vulnerability could allow remote code execution if a user opens a specially crafted Office document using an affected version of Microsoft Office software, or previews or opens a specially crafted email message in Outlook while using Microsoft Word as the email reader. This issue is rated Important for Microsoft Office 2003 and Office for Mac 2011. While details about this issue were privately disclosed, we are aware of limited, targeted attacks that attempt to exploit this vulnerability.
Watch the bulletin overview video below for a brief summary of today’s releases.
Our Bulletin Deployment Priority graph provides an overview of this month’s priority releases
(click for larger view).
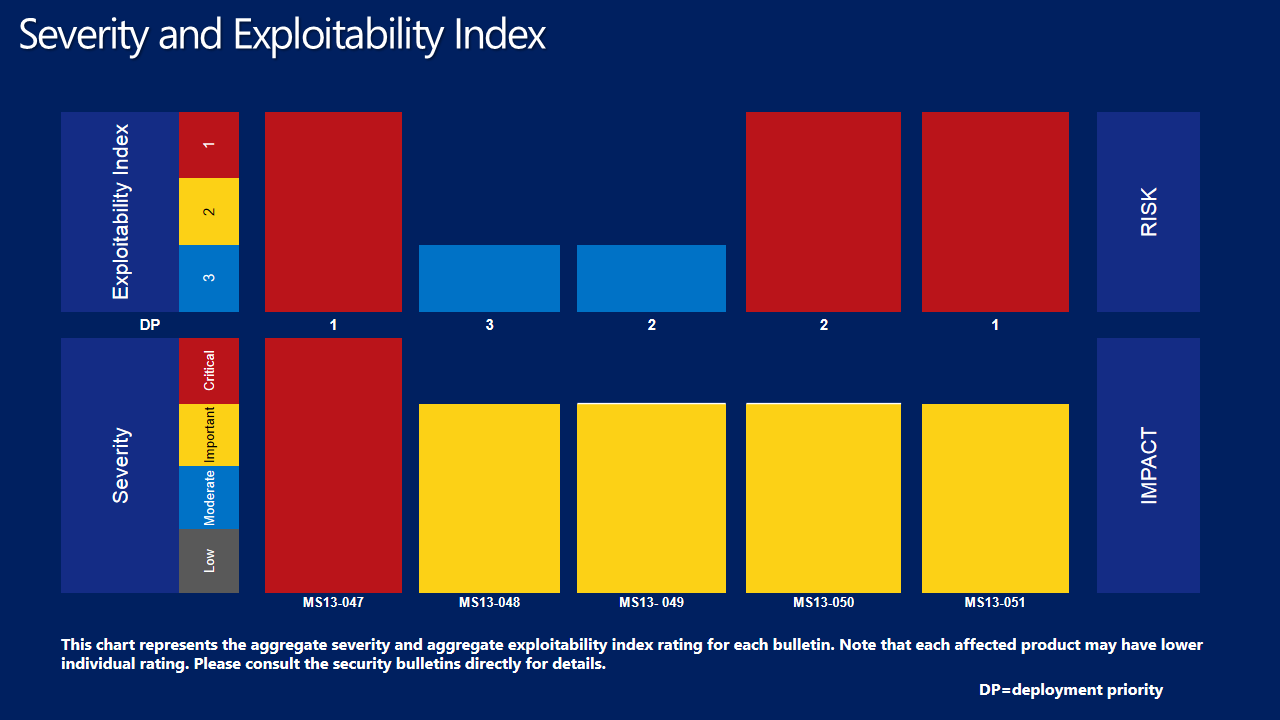
Our risk and impact graph shows an aggregate view of this month’s Severity and Exploitability Index
(click for larger view).
For more information about this month’s security updates, visit the Microsoft Bulletin Summary Web page.
Andrew Gross and I will host the monthly bulletin webcast, scheduled for Wednesday, June 12, 2013, at 11 a.m. PDT. I invite you to register here, and tune in to learn more about this month’s security bulletins and advisories.
For all the latest information, you can also follow the MSRC team on Twitter at @MSFTSecResponse.
I look forward to hearing your questions about this month’s release in our webcast tomorrow.
Thank you,
Dustin Childs
Group Manager, Response Communications
Microsoft Trustworthy Computing