Microsoft Customer Protections for May 2013
Today, we are releasing 10 bulletins, addressing 33 vulnerabilities in Microsoft products. Before we get into the details, we wanted to first let our enterprise customers know about a change in how we’re communicating technical details within our security advisories. Starting today, customers will be able to clearly identify key security updates within advisories. For further details, please visit Knowledge Base article 2849195.
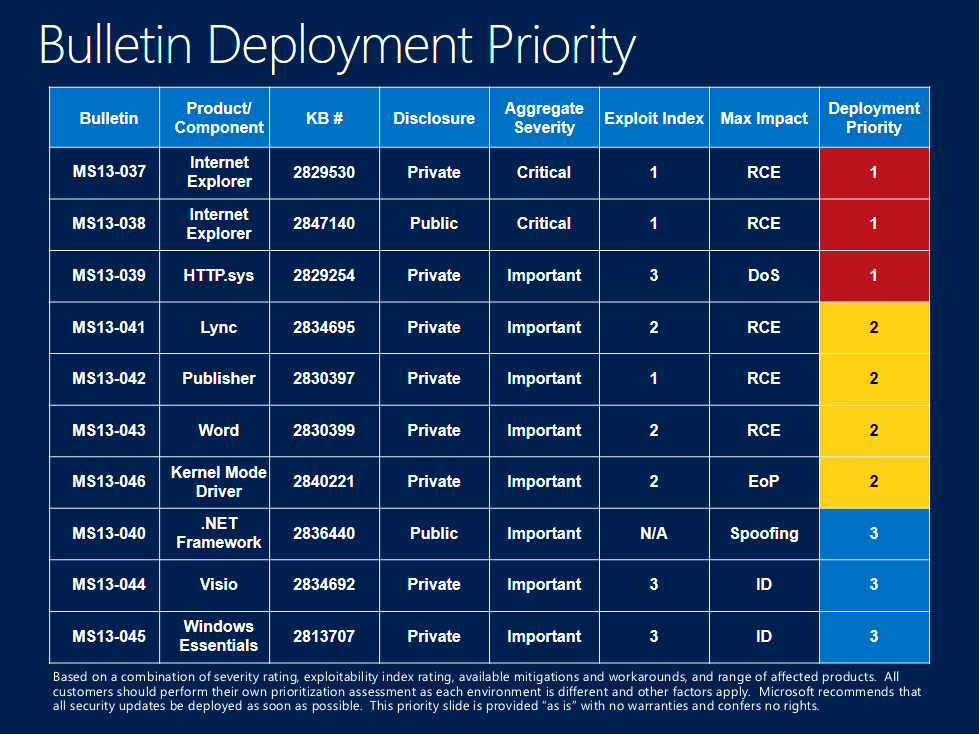
Let’s talk about the updates that we released today. Ten bulletins were released, two Critical and eight Important, addressing 33 vulnerabilities in Internet Explorer, Microsoft Windows, Microsoft Office, Server and Tools, and .NET Framework. For those who need to prioritize deployment, we recommend focusing on MS13-037, MS13-038 and MS13-039 first. As always, customers should deploy all security updates as soon as possible. Our Bulletin Deployment Priority guidance is below to further assist in deployment planning (click for larger view).
MS13-037 | Cumulative Security Update for Internet Explorer
This security update resolves 11 issues in Internet Explorer that could allow remote code execution if a customer views a specially crafted Web page using the browser. An attacker who successfully exploited these vulnerabilities could gain the same user rights as the current administrator. This security update is rated Critical for all versions of Internet Explorer, on all supported releases of Microsoft Windows. These issues were privately disclosed and we have not detected any attacks or customer impact.
MS13-038 | Security Update for Internet Explorer
This security update permanently addresses the Internet Explorer 8 issue described in Security Advisory 2847140 to help ensure customers are protected. This security update is rated Critical for Internet Explorer 8 on Windows clients and Moderate for Internet Explorer 8 on Windows servers. There is no severity rating for Internet Explorer 9. This issue was publicly disclosed and there are limited known targeted attacks.
MS13-039 | Vulnerability in HTTP.sys Could Allow Denial of Service
This security update resolves one issue in Microsoft Windows that could allow denial of service if an attacker sends a specially crafted HTTP packet to an affected Windows server or client. The security update is rated Important for supported editions of Windows 8 and Windows Server 2012. This issue was privately disclosed and we have not detected any attacks or customer impact.
Watch the bulletin overview video below for a brief summary of today’s releases.
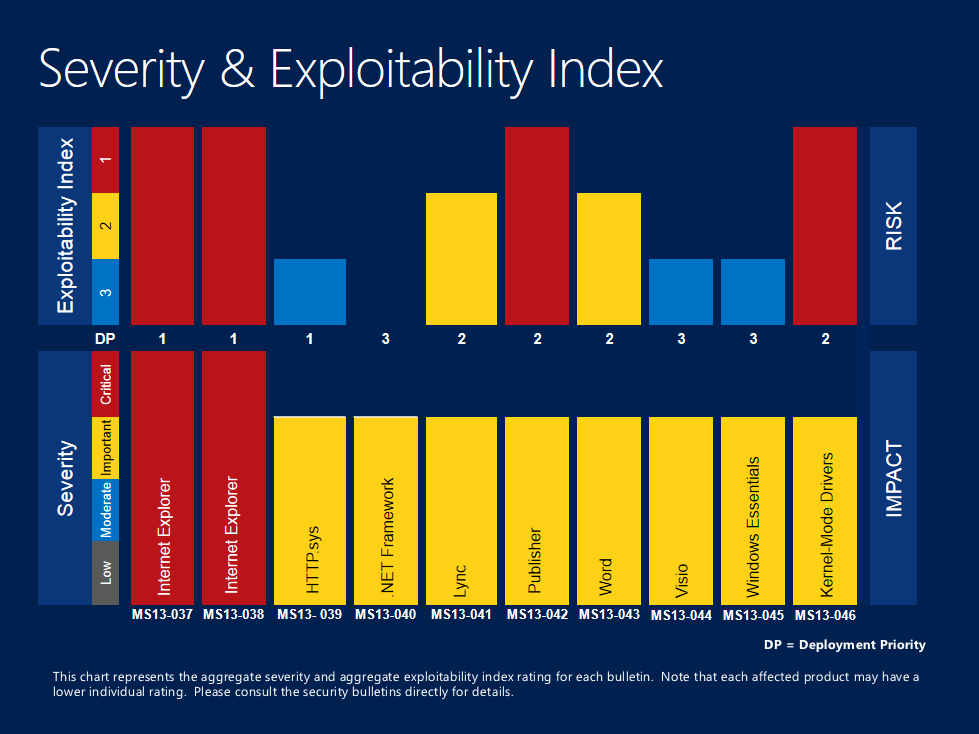
Our risk and impact graph shows an aggregate view of this month’s Severity and Exploitability Index
(click for larger view).
For more information about this month’s security updates, visit the Microsoft Bulletin Summary Web page.
Jonathan Ness and I will host the monthly technical webcast, scheduled for Wednesday, May 15, 2013, at 11 a.m. PT. I invite you to register here, and tune in to learn more about the May Security Bulletins and Advisories.
For the latest information, you can also follow the MSRC team on Twitter at @MSFTSecResponse.
I look forward to hearing your questions about today’s release in our webcast tomorrow.
Thank you,
Dustin Childs
Group Manager, Response Communications
Microsoft Trustworthy Computing