Monitoring non-domain members with OM 2012
While the rest of the System Center community is in Vegas for MMS2012 I’m helping customers with their questions about System Center Operations Manager 2012. To be honest I’m little jealous on all the people who are in Vegas right now. ![]()
So I created some more detailed documentation on how to start monitoring your non-domain members (workgroup servers in your DMZ) in OM2012.
It are still the same steps as in OM 2007 so if you already familiar with those steps it would be easy for you.
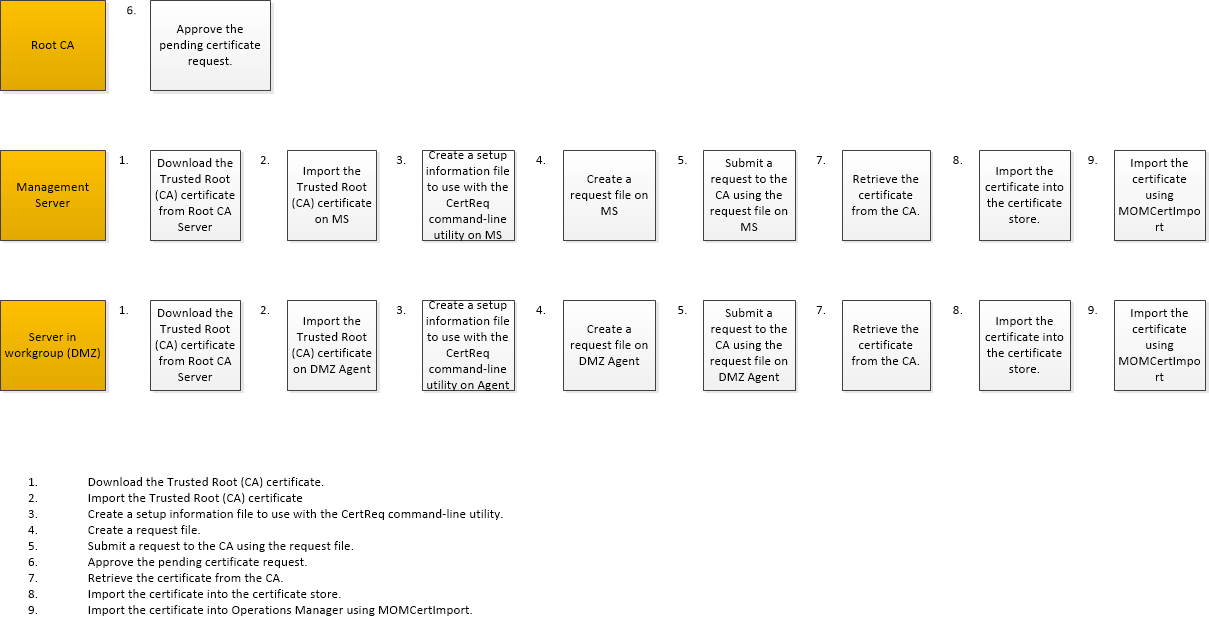
I created a simple Diagram to have a high-level overview on which steps are being executed on which machines.
Environment:
-
- OM12 RTM
-
- Stand-Alone Windows Server 2008 CA (w2k8r2dc1.demo.stranger)
-
- Two OM12 Management Servers (OM12MS01.demo.stranger and OM12MS02.demo.stranger)
-
- Workgroup server in "DMZ" (OM12DMZ01.demo.dmz)
Some important notes:
-
- Server must have a FQDN, so if it is in a workgroup add a domain suffix manually.
-
- The server being monitored must be able to resolve the FQDN of the OM2012 Management Server server.
- Check if non-domain member server can connect to port 5723 from Management Server. (use telnet client)
Guide info: https://technet.microsoft.com/en-us/library/dd362655.aspx
Pre-reqs:
It is assumed that you have AD CS installed, an HTTPS binding is being used, and its associated certificate has been installed. Information about creating an HTTPS binding is available in the topic How to Configure an HTTPS Binding for a Windows Server 2008 CA.
High-Level steps:
- Download the Trusted Root (CA) certificate.
- Import the Trusted Root (CA) certificate
- Create a setup information file to use with the CertReq command-line utility.
- Create a request file.
- Submit a request to the CA using the request file.
- Approve the pending certificate request.
- Retrieve the certificate from the CA.
- Import the certificate into the certificate store.
- Import the certificate into Operations Manager using MOMCertImport.
Step 1. Download the Trusted Root (CA) certificate
-
- Log on to the computer where you installed a certificate; for example, the gateway server or management server.
- Start Internet Explorer, and connect to the computer hosting Certificate Services; for example, https://<servername>/certsrv.
- On the Welcome page, click Download a CA Certificate, certificate chain, or CRL.
- On the Download a CA Certificate, Certificate Chain, or CRL page, click Encoding method, click Base 64, and then click Download CA certificate chain.
- In the File Download dialog box, click Save and save the certificate; for example, Trustedca.p7b.
- When the download has finished, close Internet Explorer.
[OM12MS02.demo.stranger]
Download a CA Certificate, certificate chain, or CRL
Step 2. Import the Trusted Root (CA) Certificate
-
- On the Windows desktop, click Start, and then click Run.
- In the Run dialog box, type mmc, and then click OK.
- In the Console1 window, click File, and then click Add/Remove Snap-in.
- In the Add/Remove Snap-in dialog box, click Add.
- In the Add Standalone Snap-in dialog box, click Certificates, and then click Add.
- In the Certificates snap-in dialog box, select Computer account, and then click Next.
- In the Select Computer dialog box, ensure that Local computer: (the computer this console is running on) is selected, and then click Finish.
- In the Add Standalone Snap-in dialog box, click Close.
- In the Add/Remove Snap-in dialog box, click OK.
- In the Console1 window, expand Certificates (Local Computer), expand Trusted Root Certification Authorities, and then click Certificates.
- Right-click Certificates, select All Tasks, and then click Import.
- In the Certificate Import Wizard, click Next.
- On the File to Import page, click Browse and select the location where you downloaded the CA certificate file, for example, TrustedCA.p7b, select the file, and then click Open.
- On the File to Import page, select Place all certificates in the following store and ensure that Trusted Root Certification Authorities appears in the Certificate store box, and then click Next.
- On the Completing the Certificate Import Wizard page, click Finish.
[OM12MS02.demo.stranger]
Open Certificates Local Computer account MMC:
Import Certificate TrustedCA.p7b
Step 3. Create a setup information file to use with the CertReq command-line utility.
-
- On the computer hosting the Operations Manager component for which you are requesting a certificate, click Start, and then click Run.
- In the Run dialog box, type Notepad, and then click OK.
- Create a text file containing the following content:
[NewRequest]
Subject="CN=<FQDN of computer you are creating the certificate, for example, the gateway server or management server.>"
Exportable=TRUE
KeyLength=2048
KeySpec=1
KeyUsage=0xf0
MachineKeySet=TRUE
[EnhancedKeyUsageExtension]
OID=1.3.6.1.5.5.7.3.1
OID=1.3.6.1.5.5.7.3.2 - Save the file with an .inf file name extension, for example, RequestConfig.inf.
- Close Notepad.
[OM12MS02.demo.stranger]
Step 4. Create a request file to use with a stand-alone CA
-
- On the computer hosting the Operations Manager component for which you are requesting a certificate, click Start, and then click Run.
- In the Run dialog box, type cmd, and then click OK.
- In the command window, type CertReq –New –f RequestConfig.inf CertRequest.req, and then press ENTER.
- Open the resulting file (for example, CertRequest.req) with Notepad. Copy the contents of this file onto the clipboard.
[OM12MS02.demo.stranger]
Step 5. Submit a request to a stand-alone CA
-
- On the computer hosting the Operations Manager component for which you are requesting a certificate, start Internet Explorer, and then connect to the computer hosting Certificate Services (for example, https://<servername>/certsrv).
- On the Microsoft Active Directory Certificate Services Welcome screen, click Request a certificate.
- On the Request a Certificate page, click advanced certificate request.
- On the Advanced Certificate Request page, click Submit a certificate request by using a base-64-encoded CMC or PKCS #10 file, or submit a renewal request by using a base-64-encoded PKCS #7 file.
- On the Submit a Certificate Request or Renewal Request page, in the Saved Request text box, paste the contents of the CertRequest.req file that you copied in step 4 in the previous procedure, and then click Submit.
- Close Internet Explorer.
[OM12MS02.demo.stranger]
Request a certificate
Advanced
Select Submit a certificate request by using a base-64-encoded CMC or PKCS #10 file, or submit a renewal request by using a base-64-encoded PKCS #7 file.
Step 6. approve the pending certificate request
-
- Log on as a certification authority administrator to the computer hosting Active Directory Certificate Services.
- On the Windows desktop, click Start, point to Programs, point to Administrative Tools, and then click Certification Authority.
- In Certification Authority, expand the node for your certification authority name, and then click Pending Requests.
- In the results pane, right-click the pending request from the previous procedure, point to All Tasks, and then click Issue.
- Click Issued Certificates, and confirm the certificate you just issued is listed.
- Close Certification Authority.
[W2K8R2DC1.demo.stranger]
Click Pending Request in Certificate Authority
Click on Issue
Step 7. retrieve the certificate
-
- Log on to the computer where you want to install a certificate; for example, the gateway server or management server.
- Start Internet Explorer, and connect to the computer hosting Certificate Services (for example, https://<servername>/certsrv).
- On the Microsoft Active Directory Certificate Services Welcome page, click View the status of a pending certificate request.
- On the View the Status of a Pending Certificate Request page, click the certificate you requested.
- On the Certificate Issued page, select Base 64 encoded, and then click Download certificate.
- In the File Download – Security Warning dialog box, click Save, and save the certificate; for example, as NewCertificate.cer.
- On the Certificate Installed page, after you see the message that Your new certificate has been successfully installed, close the browser.
- Close Internet Explorer.
[OM12MS02.demo.stranger]
View status of pending certificate request
Save certificate
Download certificate
Step 8. import the certificate into the certificate store
-
- On the computer hosting the Operations Manager component for which you are configuring the certificate, click Start, and then click Run.
- In the Run dialog box, type cmd, and then click OK.
- In the command window, type CertReq –Accept NewCertificate.cer, and then press ENTER
[OM12MS02.demo.stranger]
Step 9. import the certificate into Operations Manager using MOMCertImport
-
- Log on to the computer where you installed the certificate with an account that is a member of the Administrators group.
- On the Windows desktop, click Start, and then click Run.
- In the Run dialog box, type cmd, and then click OK.
- At the command prompt, type <drive_letter>: (where <drive_letter> is the drive where the Operations Manager 2007 installation media is located), and then press ENTER.
- Type cd\SupportTools\i386, and then press ENTER.
Note
On 64-bit computers, type cd\SupportTools\amd64
-
- Type the following:
MOMCertImport /SubjectName <Certificate Subject Name> - Press ENTER.
- Type the following:
[OM12MS02.demo.stranger]
MOMCertImport /SubjectName OM12MS02.demo.stranger
Check if everything is ok
Open the certificate that you installed on management/gateway server. Click on Details Tab and check the Serial Number.
Now navigate to HKLM\Software\Microsoft\Microsoft Operations Manager\3.0\Machine Settings and check the value of ChannelCertificateSerialNumber. Serial number of certificate should be listed backwards here in registry.
Open registry
Tada!
Pre-reqs on DMZ server:
Make sure you have installed the OM12 Agent first before starting.
Let's check the eventlog
Repeat steps for OM12DWZ01 server in workgroup
High-Level steps:
-
- Download the Trusted Root (CA) certificate.
- Import the Trusted Root (CA) certificate
- Create a setup information file to use with the CertReq command-line utility.
- Create a request file.
- Submit a request to the CA using the request file.
- Approve the pending certificate request.
- Retrieve the certificate from the CA.
- Import the certificate into the certificate store.
- Import the certificate into Operations Manager using MOMCertImport.
[OM12DWZ01.demo.dmz]
Step 1. Download the Trusted Root (CA) certificate.
Step 2. Import the Trusted Root (CA) certificate
Step 3. Create a setup information file to use with the CertReq command-line utility.
Step 4. Create a request file to use with a stand-alone CA
CertReq –New –f RequestConfig.inf CertRequest.req
Step 5. Submit a request to a stand-alone CA
Step 6. approve the pending certificate request
[W2K8R2DC1.demo.stranger]
Step 7. retrieve the certificate
[OM12DMZ01.demo.dmz]
Step 8. import the certificate into the certificate store
Step 9. import the certificate into Operations Manager using MOMCertImport
MOMCertImport /SubjectName OM12DMZ01.demo.dmz
Final step is approving agent
Check Security Settings in Operations Console.
Wait for Agent to turn up in Pending Approval folder
End result:
Have fun at MMS for those who are in Vegas, and for those who are not, well…