CM - Enabling multiple user certificates on one Smart Card
Enabling multiple user certificates on one Smart Card
Scenario: Create an automated way of adding two certificates to the same card each representing a different account.
Solution: provides the capability to put two or more certificates, each associated with a different account, on one card.
- The additional certificates are not limited to accounts solely owned by the smart card owner (i.e. a group account).
- Each additional certificate, when presented for selection, can have obviously distinct names.
- There is no need to limit the number of certificates to two.
Before continuing it is recommended to read about the custom policy modules and OID at:
https://technet.microsoft.com/en-us/library/gg418616(v=ws.10).aspx
https://technet.microsoft.com/en-us/library/cc708677(v=ws.10).aspx
https://msdn.microsoft.com/en-us/library/windows/desktop/aa379070(v=vs.85).aspx
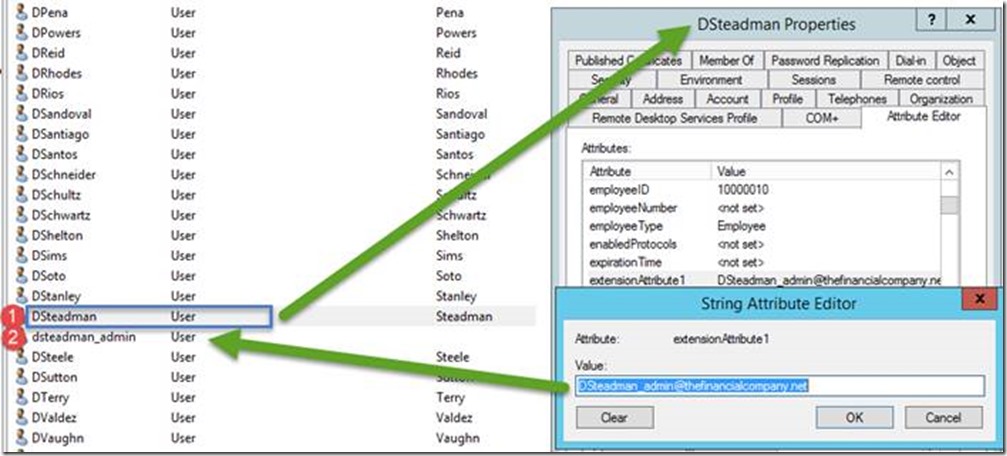
Here is the scenario we have a user called dsteadman and also a admin account called dsteadman_admin. We want to enroll in a smart card for both the user and his admin account to the same smart card. To do this we will link them using the extensionAttribute1, We also populated extensionAttribute2 with the username of the admin account
Thank you and credit for this collaboration to:
- Steve Light
- Jay Hoffmeier
Steps involved:
- Certificate Template changes:
- Create one or more additional Smart Card Certificate Templates
- These additional templates will be based on copies of the existing Certificate template
- There will be one new certificate template required for each additional certificate to be issued
- Enable deployment of these new templates by the same CA as the original
- Create two new Custom Policy Modules on the CA for each of the new templates
- The first will modify the certificate to associate it with a different AD account
- The second will modify the certificate to have a unique display name
- Create one or more additional Smart Card Certificate Templates
- CLM Changes
- Create a new profile template which issues certificates from both (or more) smart card certificate templates
- Add a data collection element at request time to allow the requestor to enter the AD account name for any additional certificates.
Procedure: (to be repeated for each additional certificate needed on a card)
- Create the duplicate Smart card Certificate Templates (performed on the issuing CA)
- From the Administrative Tools menu, open Certification Authority.
- In the Certification Authority window, expand the CA and right-click on Certificate Templates and select Manage.
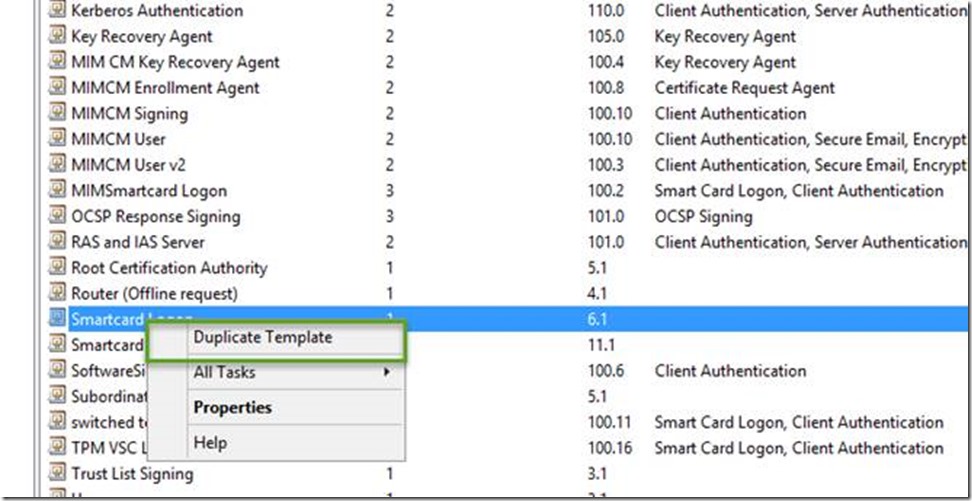
- In the certtmpl window, right-click on the certificate template currently used for Smartcard logon (ex: Smartcard Logon) and select Duplicate Template.
-
- In the Properties of New Template window, in the General tab, provide a new Template Display Name (ex: Smartcard Logon Certificate 2).
- Click OK to close the properties window.
- Close the certtmpl window.
Enable issuance of this new certificate template
- At the Certification Authority window, right click on Certificate Templates, and select New -> Certificate Template to Issue.
- In the Enable Certificate Templates window, select the newly created certificate template (ex: Smartcard Logon Certificate 2), and click OK.
- Close the Certification Authority Window
Add the custom policy modules
Subject Alternate Name module
- From the Administrative Tools menu, open Certification Authority.
- In the Certification Authority window, right click on Smartcard Issuing CA 1 and select Properties.
- Click on the Policy Module tab.
-
- Click Properties to edit the Certificate Lifecycle Manager Policy module.
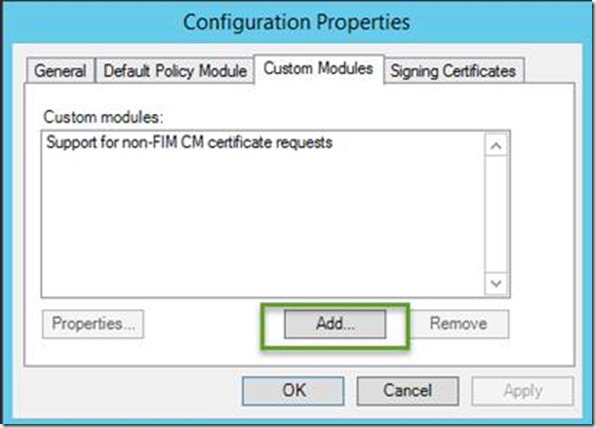
- On the Custom Modules tab, click Add
-
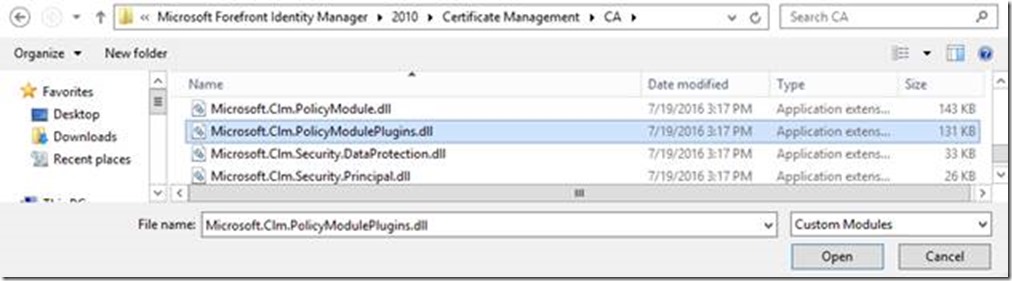
- Browse to the CA folder where Certificate Lifecycle Manager is installed (default location of c:\program files\microsoft certificate lifecycle manager\ca) and select Microsoft.Clm.PolicyModulePlugins.dll
-
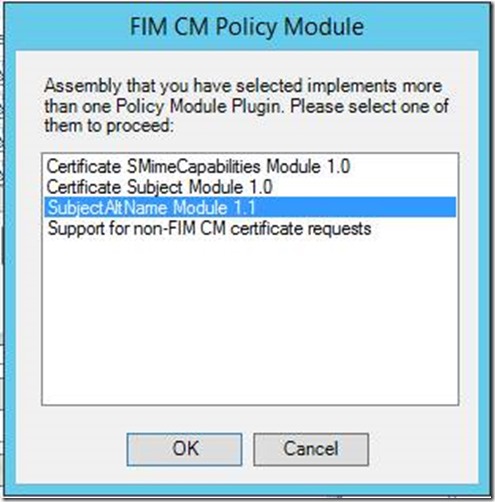
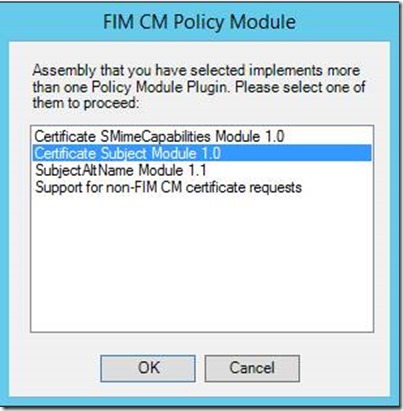
- In the Clm Policy Module window, select SubjectAltName Module 1.1
-
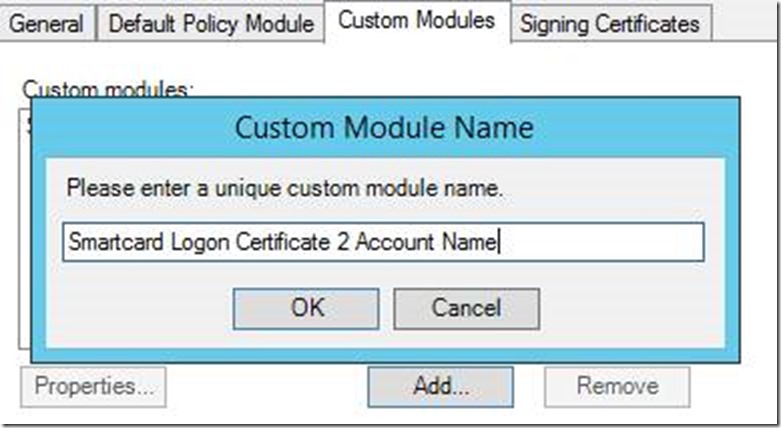
- Assign a name to the custom module (ex: Smartcard Logon Certificate 2 Account Name) and click OK.
-
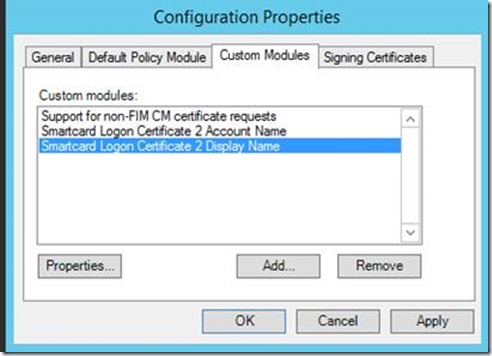
- Back on the Custom Modules tab, select the new custom module and click Properties.
-
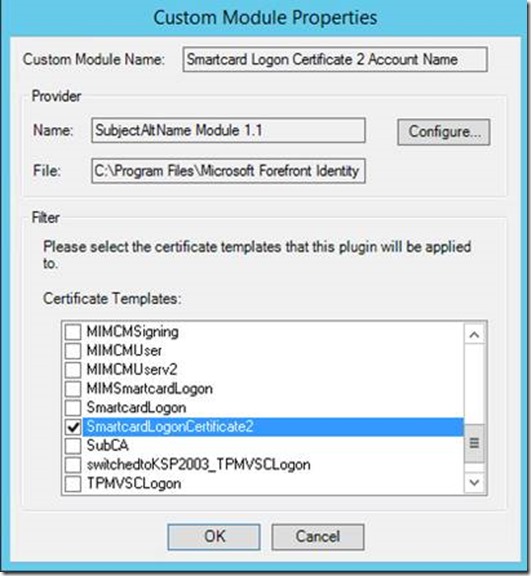
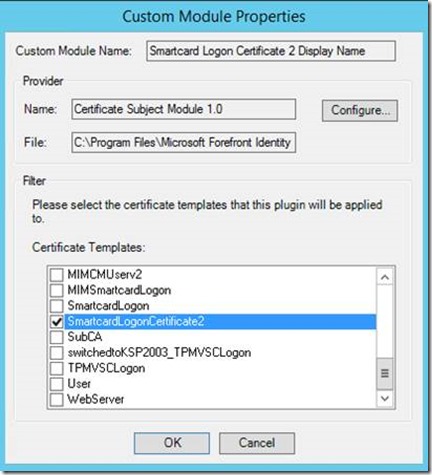
- On the Custom Module Properties window, select the certificate template previously created (duplicated) that will be used for the second certificate (ex: SmartcardLogonCertificate2).
-
- On the Custom Module Properties window, select Configure…
-
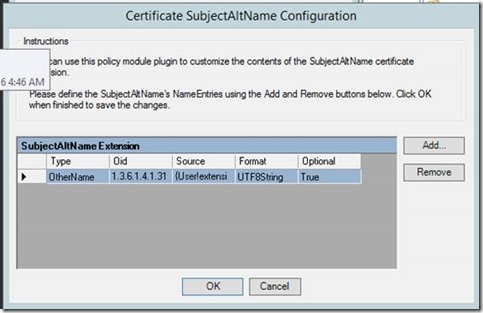
- On the Certificate SubjectAltName Configuration window, click Add...
- On the SubjectAltName Name Entry window, under Type, select OtherName and enter the following OID: 1.3.6.1.4.1.311.20.2.3
- On the SubjectAltName Name Entry window, under Value, select UTF8String and enter {User!extensionAttribute1} . This will build the full SubjectAltName from information entered into active directory user attribute extensionAttribute1.
- Note: you can use attribute used on enrollment with data collection by defining it as {Clm!datacollectionitem}
- Check the option Do not include this name entry if the value is empty or not available.
- Click OK to close the SubjectAltName Name Entry window.
- Click OK to close the Certificate SubjectAltName Configuration window.
- Click OK to close the Custom Module Properties window.
- Certificate Subject Name module
- On the Custom Modules tab, click Add
- Browse to the CA folder where Certificate Lifecycle Manager is installed (default location of (c:\program files\microsoft certificate lifecycle manager\ca) and select Microsoft.Clm.PolicyModulePlugins.dll
- In the Clm Policy Module window, select Certificate Subject Module 1.0
-
- Assign a name to the custom module (ex: Smartcard Logon Certificate 2 Display Name) and click OK.
-
- Back on the Custom Modules tab, select the new custom module and click Properties.
- On the Custom Module Properties window, select the certificate template previously created (duplicated) that will be used for the second certificate (ex: SmartcardLogonCertificate2). Note: This is optional and only SAN is required
-
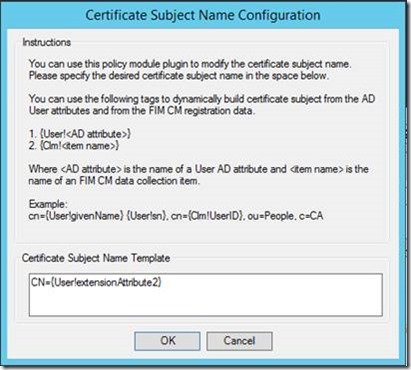
- On the Custom Module Properties window, select Configure...
- For the Certificate Subject Name Template enter CN={User!extensionAttribute2}
-
- Click OK to close the Certificate Subject Name Configuration window.
- Click OK to close the Custom Module Properties window.
- Click OK to close the Configuration Properties window.
- Click OK to close the CA Properties Window. The CA will need to be restarted for the new changes to take effect.
- CM Configuration
- Log onto the Certificate Manager portal with an account that can edit profile templates.
- At the CM Manager Operations home screen, click on Manage Profile Templates.
-
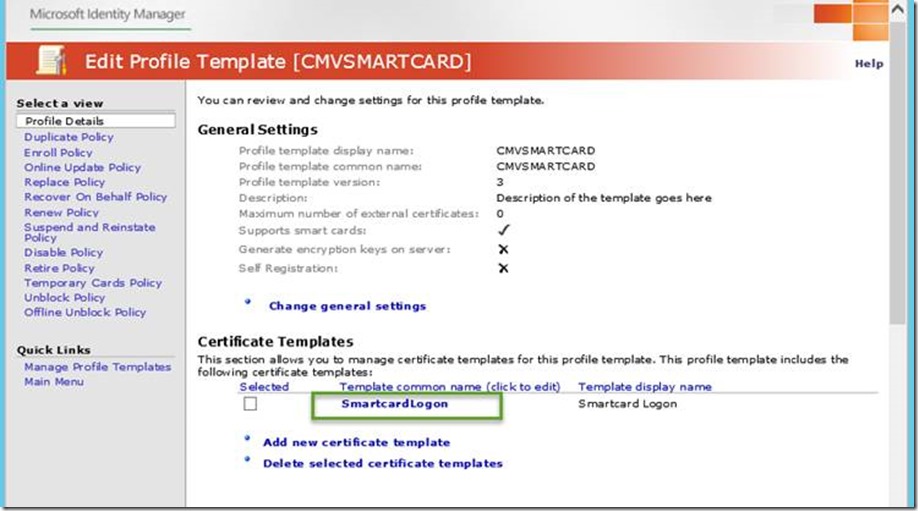
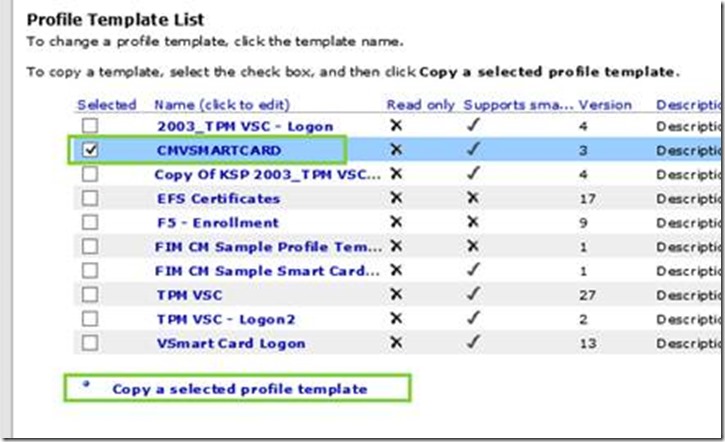
- Select your current smartcard profile template (ex: SCMVSMARTCARD) and click on Copy a selected profile template
-
- Provide a new name for the profile template (ex: SCMVSMARTCARD2).
- Click on the new profile template to modify its settings.
- Perform these next steps for each additional certificate to be applied to the card
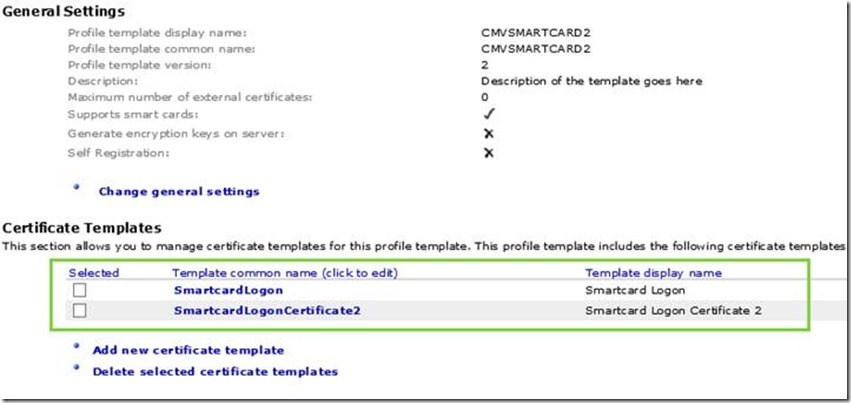
- In the Profile Details -> Certificate Templates section, add the second certificate template which was duplicated earlier (ex: SmartCardLogonCertificate2). You should now have both certificate templates enabled for this profile template.
- Click OK.
Testing: Log on with test user
- First lets login as our test user(dsteadman)
- Insert Smart Card
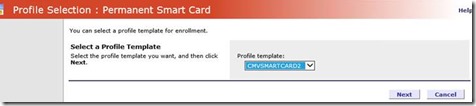
- Login to CM and select Request New Permanent Smart Card
-
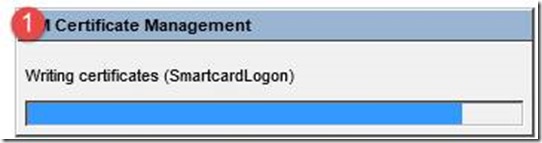
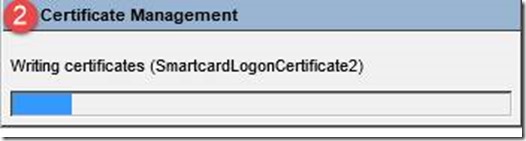
- During Enrollment you will see the writing of both certificates for the user and the admin certificate
-
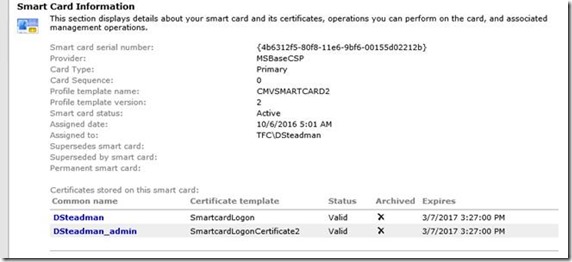
- Now let look at the certificate issues
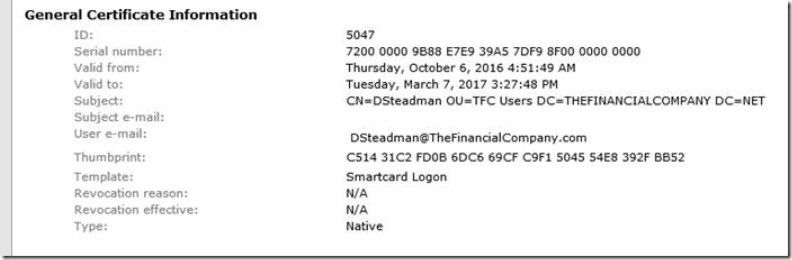
- The Normal User account (dsteadman)
- Now let look at the certificate issues
-
-
- The Admin Account (dsteadman_admin)
-
To summarize what we have done we had 2 users 1 of which is the admin account used for login to do administrative functions. The scenario is the business wanted the login certs for the user and the admin account. In this scenario it writes both certificates and the CM profile is tied to the normal user so that if the use should go away the profile template with both user and admin certs go away.