Defense-in-Depth vs. BitUnlocker: How to defeat Cold DRAM attacks using BitLocker, Power Options, and Physical Security
Princeton University published a paper this week entitled: Lest We Remember: Cold Boot Attacks on Encryption Keys which shows how an attacker can extract the contents of DRAM from a computer that is powered off and retrieve the encryption keys from memory offline and decrypt disks that were encrypted by many popular disk encryption software such as Microsoft BitLocker, FileVault, dm-crypt, and TrueCrypt on Linux, Vista and Mac OS 10 — using no special devices or materials.
They also published a video which includes a special form of this attack on BitLocker which they dubbed "BitUnlocker" which demonstrates the attack using the following method:
1. The machine is powered on and locked
2. They attach a USB disk
3. They cut power by removing the battery
4. They quickly replace the battery and restart the laptop
5. The computer boots to the external drive which copies everything in memory capturing most of the data still in DRAM.
6. The program then looks for the encryption keys offline.
The attack vectors are for computers using BitUnlocker that are machines that are sleeping, locked or in the case of BitLocker if there is no required PIN or USB Key. Here is Microsoft's official response:
The claims detailed in the Princeton paper are not vulnerabilities, per se, but simply detail the fact that contents that remain in a computer's memory can be accessed by a determined third party if the system is running. BitLocker is an effective solution to help safe guard personal and private data on mobile PCs and provides a number of protection options that meet different end-user needs. Like all full volume encryption products BitLocker has a key-in memory when the system is running in order to encrypt/decrypt data, on the fly, for the drive/s in use. If a system is in 'Sleep mode' it is, in effect, still running. We recognize users want advice with regards to BitLocker and have published best practice guidance in the Data Encryption Toolkit (available here). In it we discuss the balance of security and usability and detail that the most secure method to use BitLocker is hibernate mode and with multi-factor authentication.
How do you defeat such an attack practically? - the answer is simply that you follow Microsoft's recommended best practice security and "Defense in Depth" Here are my recommendations in order to Defeat BitUnlocker with BitLocker, Power Options, and Physical Security Best Practices:
You must have TPM 1.2, “TPM+PIN” (or “TPM+USB”) configured, and machine must be in Hibernate or Powered Off state when not in use or when attacked by BitUnlocker.
Note: If machine is still running and locked or only been shut off for a few seconds and attacked it is still vulnerable to this attack. (This is where physical security is key).
The main attack vector is that non physically secured machines (i.e. laptops, PCs in unlocked buildings) that are not in use (in the hotel room or at the desk when you are at lunch), are still running (i.e. sleeping or active/locked).
The following will show you how to configure Bitlocker 1.2 with TPM + PIN configuration and to configure your Laptop to Hibernate or Shutdown (not Sleep) so that you will not be easily defeated by this attack.
1. Use Bitlocker with a TPM 1.2 with “TPM + PIN” configuration – This is Microsoft’s recommended most secure BitLocker option anyway, it basically requires a pin on boot and anytime it wakes up from Hibernation or started. You can back up your recovery key to a network share – In my case, My Documents is mapped to a network server, so I can get to the recover the Key from another machine if I forget my pin. Caution: If you save your recovery key to a USB drive or print it and that USB drive or printed document is stolen with your laptop or lost, then you are at risk or even unable to recover your pin which I why I prefer a network drive that’s secured and backed up.
2. Configure BitLocker: Pre-Requisites & Step-by-Step Guide - For BitLocker to work, you must be running Vista Ultimate or Vista Enterprise edition and have at least two partitions on your hard disk. Review https://download.microsoft.com/download/c/3/8/c3815ed7-aee7-4435-802b-8e855d549154/BitLocker_StepByStep.doc for minimum system requirements and disk partitioning information and basic BitLocker setup configuration, then proceeded to Step 3 to configure TPM+PIN.
3. Configure TPM+PIN (or TPM+USB)
To turn on BitLocker Drive Encryption with a TPM plus a PIN or with a TPM plus a startup key on a USB flash drive
1. Click Start, type gpedit.msc in the Start Search box, and then press ENTER.
2. If the User Account Control dialog box appears, verify that the proposed action is what you requested, and then click Continue. For more information, see Additional Resources later in this document.
3. In the Group Policy Object Editor console tree, click Local Computer Policy, click Administrative Templates, click Windows Components, and then double-click BitLocker Drive Encryption.
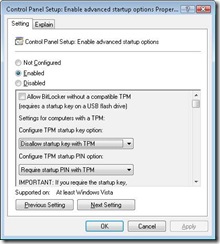
4. Double-click the setting Control Panel Setup: Enable Advanced Startup Options. The Control Panel Setup: Enable Advanced Startup Options dialog box appears.
5. Select the Enabled option. For TPM plus a PIN or startup key configurations, you do not need to change any further settings, but you can choose to require or disallow users to create a startup key or PIN. Click OK.
6. Click Start, type gpupdate.exe /force in the Search box, and then press ENTER.Wait for the process to finish.
7. Click Start, click Control Panel, click Security, and then click BitLocker Drive Encryption.
8. If the User Account Control message appears, verify that the proposed action is what you requested, and then click Continue. For more information, see Additional Resources later in this document.
9. On the BitLocker Drive Encryption page, click Turn On BitLocker on the system volume.
10. On the Set BitLocker startup preferences page, select the startup option you want. You can choose only one of these options:
· Require PIN at every startup. You will see the Set the startup PIN page. Enter your PIN, confirm it, and then click Set PIN.
· Require Startup USB key at every startup. You will see the Save your Startup Key page. Insert your USB flash drive, choose the drive location, and then click Save.
11. On the Save the recovery password page, you will see the following options:
· Save the password on a USB drive. Saves the password to a USB flash drive.
· Save the password in a folder. Saves the password to a network drive or other location.
· Print the password. Prints the password.
Important:
The recovery password will be required in the event the encrypted drive must be moved to another computer, or changes are made to the system startup information. This password is so important that it is recommended that you make additional copies of the password stored in safe places to assure you access to your data. You will need your recovery password to unlock the encrypted data on the volume if BitLocker Drive Encryption enters a locked state (see Scenario 4: Recovering Data Protected by BitLocker Drive Encryption). This recovery password is unique to this particular BitLocker encryption. You cannot use it to recover encrypted data from any other BitLocker encryption session.
Choose any of these options to preserve the recovery password. Store recovery passwords apart from the computer for maximum security. To choose more than one recovery password storage method, select one, follow the wizard to determine the location for saving or printing, and then click Next. You can then repeat this step to choose additional recovery password storage methods.
12. On the Encrypt the selected disk volume page, confirm that the Run BitLocker System Check check box is selected, and then click Continue.
Confirm that you want to restart the computer by clicking Restart Now. The computer restarts and BitLocker ensures that the computer is BitLocker-compatible and ready for encryption. If it is not, you will see an error message alerting you to the problem before encryption starts.
13. If it is ready for encryption, the Encryption in Progress status bar is displayed. You can monitor the ongoing completion status of the disk volume encryption by dragging your mouse cursor over the BitLocker Drive Encryption icon in the tool bar at the bottom of your screen or clicking on the Encryption balloon.
By completing this procedure, you have encrypted the operating system volume and created a recovery password unique to that volume. The next time you turn your computer on, the USB flash drive must be plugged into a USB port on the computer or you must enter your PIN. If you do not, you will not be able to access data on your encrypted volume. Store the startup key away from the computer to increase security. Without the startup key, or your PIN, you will need to go to recovery mode and supply the recovery password to access your data.
4. Choose a PIN with at least 7 numbers of which at least 4 digits are unique - For additional information please review: MSDN Blog - Finding a Secure Pin
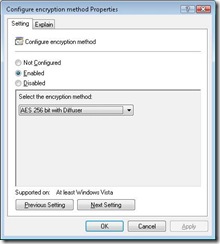
5. If your machine is sufficiently fast, while you are in GPEDIT.MSC, I would recommend changing the “Configure Encryption Method” policy to “AES 256 bit with Diffuser” to reduce the chance of a Brute Force attack being successful. More information on differences between 128-bit and 256-bit drive encryption are found at: https://windowshelp.microsoft.com/Windows/en-US/Help/c4500bf7-8392-4c38-a56e-d018a2438aa21033.mspx. The default is 128 bit with Diffuser, but I am using 256 with no performance degradation.
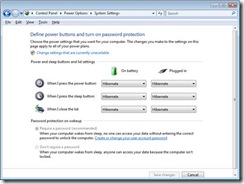
6. From Control Panel->Power Options, Change the “Choose what the power buttons do” options from Sleep to Shutdown or Hibernate. In my example below, I changed from Sleep to Hibernate. The effect of this is that you will have a minute delay on shutting down and powering up your Laptop and you will be required to Enter a Pin
7. Once you have configured your power options, any time you start your machine, you will be required to enter your pin number, but the advantage here against the attack’s shown in the video are that the memory is written to disk which is protected by BitLocker in Hibernate mode.
8. Please remember that the most dangerous automated attack vector here from the paper was using BitUnlocker to attack a machine that was “Sleeping” because the machine is still running memory is still active. That gives a thief ample time to get access to the memory and cool it or launch the automated BitUnlocker attack at anytime.
When shutting off your Laptop or go into “Hibernate” all memory is written to disk which is now protected by BitLocker, however remember that there is still a few seconds to a couple of minutes where you need to watch your laptop after it shuts down while the DRAM diffuses its memory.
Once it’s shutdown or in hibernate mode and memory is diffused, BitUnlocker cannot access the key in memory if TPM+PIN is configured. They will have to resort to Brute Force attack on the PIN which is very difficult because of built-in anti-hammering technology.