Crypto locker on your Machine
Probably one of the smartest malware, in my opinion, yes I’m starting with praise for this malware. Very smart modus operandi. If you are struck with it, you have only two options either you pay or forget about your files.
If you are smart then you will keep your machines protected by super patching, leaving no vulnerable software and operating system .Apart from that, have Backups for all your important stuff.
MMPC(Microsoft Malware Protection Center) has recently published a post on its blog , you can read that here. The most important points discussed, in this is how ransom ware (Win32/Crowti and its family) spreads, which is majorly via spam emails containing attachments, luring users to open them. The other way is through exploit kits, which provide exploits, to exploit the java or flash vulnerabilities on a user’s system i.e. if these software are unpatched and are hence vulnerable.
This post, is an example, where an exploit kit manages to exploit a vulnerability on the system. In this scenario, it was a client machine i.e. machine with a client operating system, on a network that got infected. We were trying to find the way infection happened, so we collected data from the infected machines and started looking at it.
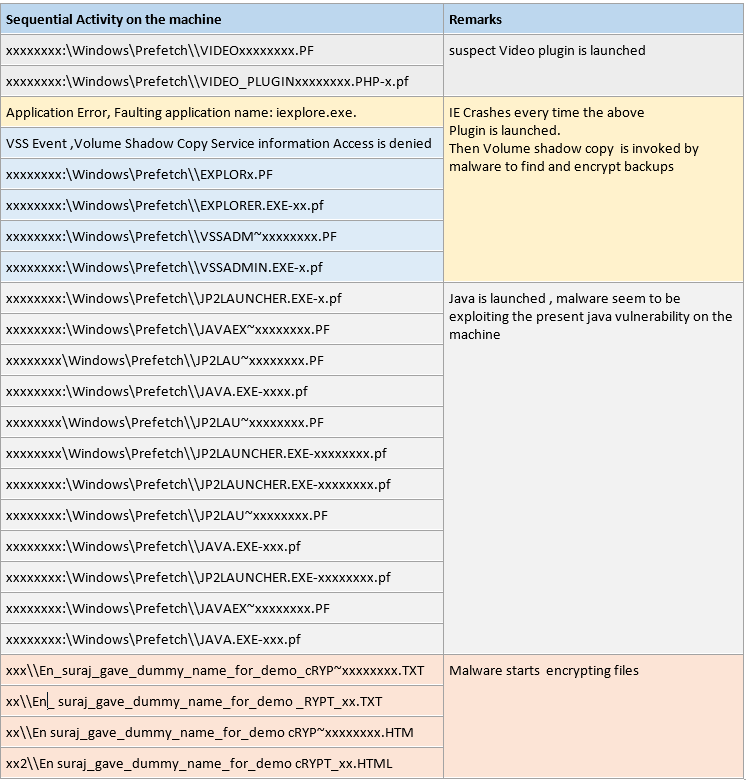
Observations from data
I’m putting down sequential activity below, sequenced in terms of time.
Vulnerable software list as pulled down by data collection tool, partially shown below, on the infected machines did not have Java updated and hence left machines vulnerable. By comparing the installed versions and latest versions of java software, on these infected machines, we could understand clearly the big hole in them, as installed versions were way behind the latest versions. That’s what exploits from the exploit kits keep looking and if found, its bull’s eye for them and they nail it.
Software |
Installed Version |
Latest Version |
Java(TM) x Update x |
X |
x |
JavaFX x.x.x |
X |
x |
Java Auto Updater |
X |
x |
Let’s now connect the dots together in this scenario. So we could see that suspect plugin was getting launched (as we can see from pre-fetch files in above table of activity), about prefetch folder and files please refer https://windows.microsoft.com/en-in/windows-vista/what-is-the-prefetch-folder.
Every time, it was getting launched, it was crashing IE for some reason. Then it was trying to launch Volume shadow copy, to find backups and also encrypt them. Then it started launching Java files, obviously exploit, found out that java software were unpatched and exploited them. So what happened is, that it put the java jar files on the machine and unzipped it in the memory not on hard drive, hence went undetected from the antivirus on the system. Then started its operation and next thing we see is, it starts encrypting the files on the system. Checkmate, game over.
So Ideal thing to do here, as prevention is to make sure, your machines are patched.
I have also seen third party websites suggesting restriction of executable in appdata folder on the machine e.g.
On following path
Path: %AppData%\*.exe
i.e. Create rules to make sure executables cannot run on this location i.e. subfolder of %AppData%.
But we don’t either suggest or recommend it, as there could be good applications that may need to run from this location, however Applocker can be used to white list the legal applications to run on the machine.