Generating netstat output and scenario based tracing using netsh when a specific event occurs in the eventlog-using Powershell
I was working on a case, where I needed to get netstat outpiut to understand certain connections behavior and I needed to do that for a particular event in the event log. It was really difficult to get this output exactly at the time this event was occuring. So I started working on it in my lab. I used my previous blog post about nmcap and eventmon and idea of powershell, which is a amazing tool and technology.
for event id I did not have to do much, i used the same script mentioned in my previous blog post where i had reference: https://blogs.technet.com/b/netmon/archive/2007/02/22/eventmon-stopping-a-capture-based-on-an-eventlog-event.aspx
I simplified that in my blog post : https://blogs.technet.com/b/sooraj-sec/archive/2011/12/23/using-eventmon-and-nmcap-to-take-network-monitor-trace-when-a-particular-event-is-generated.aspx Now i m trying to modify it further to get netstat output when an event occurs.
Step1 :Copy the contents of the script given in above post shown below in a notepad and save it as EvtMon.vbs and put this in a folder lets call it netstat and in my lab i put it in c:\netstat location
'======================================================================
' Print out the help when something is not typed in correctly or when
' nothing at all is typed in.
Public Sub PrintHelp
Wscript.Echo "Usage:"
Wscript.Echo " EvtMon EventNumber [LogFileDisplayName]"
Wscript.Echo " LogFile is optional. If used, the eventlog name"
Wscript.Echo " file ie, application, system, security, etc..."
End Sub
' Get the arguments. Check for event nubmer and log file as arugments
Set objArgs = WScript.Arguments
' See how many arguments we have and colect them.
if objArgs.Count < 1 OR objArgs.Count > 2 Then
PrintHelp
ElseIf objArgs.Count > 1 Then
EventNumber = objArgs(0)
LogFile = objArgs(1)
Else
EventNumber = objArgs(0)
LogFile = ""
End If
If EventNumber <> "" Then
strComputer = "."
' Attatch to the WMI Service
Set objWMIService = GetObject("winmgmts:{(Security)}\\" & _
strComputer & "\root\cimv2")
' if the LogFile is populated add this to our query. Create a
' Event Log monitoring object and send it a query.
If LogFile = "" Then
Set colMonitoredEvents = objWMIService.ExecNotificationQuery _
("Select * from __InstanceCreationEvent Where " _
& "TargetInstance ISA 'Win32_NTLogEvent' " _
& "and TargetInstance.EventCode = '" _
& EventNumber & "'")
Else
Set colMonitoredEvents = objWMIService.ExecNotificationQuery _
("Select * from __InstanceCreationEvent Where " _
& "TargetInstance ISA 'Win32_NTLogEvent' " _
& "and TargetInstance.EventCode = '" _
& EventNumber _
& "' and TargetInstance.LogFile = '" _
& LogFile & "'")
End If
' Create an object which returns when the next event occurs.
Set objLatestEvent = colMonitoredEvents.NextEvent
' Print some info based on the event log we encountered.
Wscript.Echo objLatestEvent.TargetInstance.User
Wscript.Echo objLatestEvent.TargetInstance.TimeWritten
Wscript.Echo objLatestEvent.TargetInstance.Message
WScript.Echo objLatestEvent.TargetInstance.Logfile
Wscript.Echo
End If
Step2 : Copy the contents of the batch file below in a notepad and save it as netstat.bat in same folder
@echo off
cscript //NoLogo EvtMon.vbs %2 %3
powershell.exe -command "& netstat -ano | Out-file c:\netstat\netstat.txt
ping -n 1 4.3.2.1
goto :EOF
Note: You can see that I m taking output of the file at location c:\netstat\netstat.txt
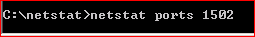
Usage : After saving the two files at c:\netstat folder, Open up a elevated command prompt and then go to the folder, where we have saved these two files and then run command(this is an example command here, 1502 is the event id) -> netstat ports 1502
reference snapshots below
Note : once you run this command it just waits for the event to occur
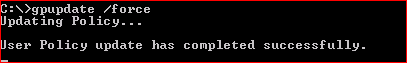
This event "1502 "gets generated when you update the group policy , I used this event in my lab, for a quick repro as whenever you run gpupdate/force this event will be generated, so I ran gpupdate /force as shown below
after this I got 1502 event and got my netstat output as well as you can see in my snapshot below
for people who like to experiment, the batch file can be modified to get a filtered out put as shown below, in following batch file i filtered the output for filtered connections, similarly we can filter for other connection stated , even more specificaly the attacks e.g. half open connections, which show up as "Syn_received"
***********************************************
@echo off
cscript //NoLogo EvtMon.vbs %2 %3
powershell.exe -command "& netstat -aonp TCP | select-string "ESTABLISHED" | Out-file c:\netstat\netstat.txt
ping -n 1 4.3.2.1
goto :EOF
***********************************************
Collecting Scenario based tracing using netsh when an event occurs
Following section is about a scenario if you want to collect netsh scenario based trace to look at various networking components when a particular event occurs.
So instructions about the eventmon.vbs and contents remain the same , You modify the contents of batch file as below and let us say save it as netsh1.bat
*******************************************************************
@echo off
cscript //NoLogo EvtMon.vbs %2 %3
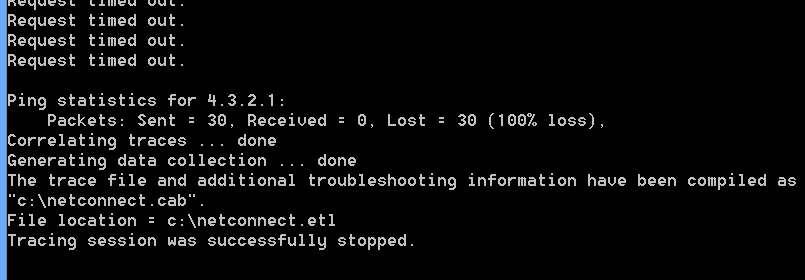
netsh trace start scenario=netconnection capture=yes tracefile=c:\netconnect.etl
ping -n 30 4.3.2.1
netsh trace stop
goto :EOF
*******************************************************************
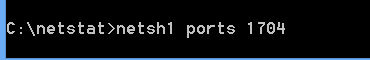
and run it like
here netsh1 is your file name, ports is just a place holder , 1704 is your event id.
in the batch file i have introduced delay of few minutes by pinging 4.3.2.1 ,30 times so that we can get good amount of trace collected at the time of issue. we can vary this number as per amount of delay we want.
so once the event will occur netsh tracing would start and after 30 pings tracing will stop and file will be located at c:\netconnect.etl.
so after event occurs , you will see this at the end explaining the data has been captured with its location and that tracing was stopped.