Setting internal network address ranges as per the routing table on the ISA server
Although we know that we can configure the address ranges on the ISA server using different methods e.g. using adapter,add ranges or add private ranges from the three private range options.
But I would like to emphasize on the usage of first option to define the address ranges of the internal network.Because it uses the routing table on the ISA server to create the address range. In other words it adds those address ranges which ISA really knows on his internal network.
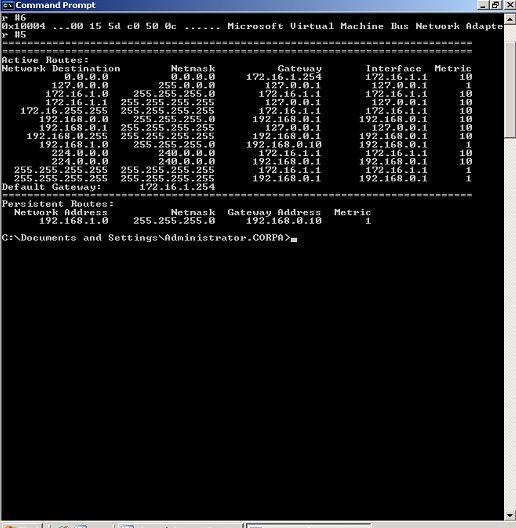
Let us say we have following routing table on the ISA server
Here we can see there is a persistent route for 192.168.1.0 network and we can also see that in order to reach this network ISA need to send traffic to 192.168.0.10 router(next hop). In other words ISA has know how of this network and way to reach it. And this is what we should have for the networks which are behind the ISA server and we want them to configure as ISA server's internal network i.e. routes to all the networks on ISA server which are behind ISA server.
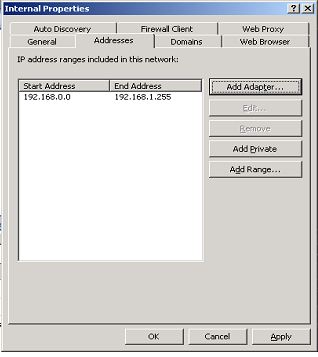
So lets go ahead and add address ranges using add adapter option lets open the internal network properties
and go to addresses tab
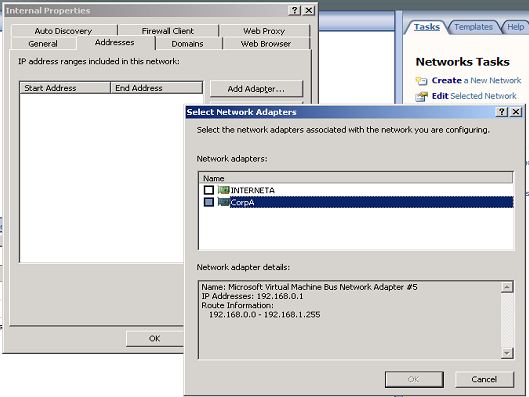
then click on Add adapter button then you would get following screen
In this screen we can see that we have NICs listed, both internal and external. if we highlight a NIC we would be able to see the routing information for that NIC. Then choose the internal NIC in this case its CorpA, when we highlight it we can see we have the address range as per the routing table on the ISA server.
As a result we would see above address range as the internal network for ISA server. Now let me talk about the reason why I or some one would prefer this approach.
Let us now assume that we do not have persistent route in the above mentioned routing table. Then instead of using Add adapter button we use button Add range and add range 192.168.0.0-192.168.1.255 in the address range. After using this approach we will start getting alerts saying you have a address range for which you do not have route through the internal network card and and packets or traffic from that traffic would be dropped as spoofed. That is what would happen packets from that network would be dropped as spoofed.
In order to avoid such misconfiguration and problems as its effect we can use the approach discussed here initially, which would insure that we are defining those networks as internal for which we have routes on the ISA server.