Manage Mobile Browser Access | CA Scenarios for Success (4 of 4)
Today we are back with the final installment of our four part series on conditional access scenarios for success! We often hear from our customers that they want to give end users flexibility to access corporate resources on the go through their mobile browser, but still need the ability to manage that access and prevent data loss. When users access data through apps that support Intune App Protection, such as the Intune Managed Browser/Outlook/OneDrive, we can enforce policies to prevent data loss; however, up until a few months ago we had no way to force the use of a MAM protected app when accessing web resources. This left customers running the risk of data leakage when users accessed resources through unmanaged browsers such as Safari/Chrome.
Thanks to new features of Conditional Access, we can block access to corporate resources on unmanaged browsers (such as Safari/Chrome) and force the use of the Intune Managed Browser! This enables web view of O365 and on-premises resources published through App Proxy to only be available through the Intune Managed Browser where we can prevent data loss with Intune App Protection policies.
The additional benefit to end users? True Single Sign-On to Office 365 and other Azure AD applications! When your users access other web applications from the Intune Managed Browser (such as third party federated apps or those you have published with App Proxy), they will be seamlessly signed in to these applications- no username/password prompts. So this is a great improvement in end-user experience and accessing applications that they may need to use on mobile devices!
Scenario Requirements
This scenario requires a single Conditional Access policy along with an Intune App Protection policy targeting the Managed Browser, plus any other applications you want to protect. In our configuration today we focus on ExO/SPO, but you can extend the Intune App Protection policy to ensure the DLP settings are in place across additional applications.
- Conditional Access policy
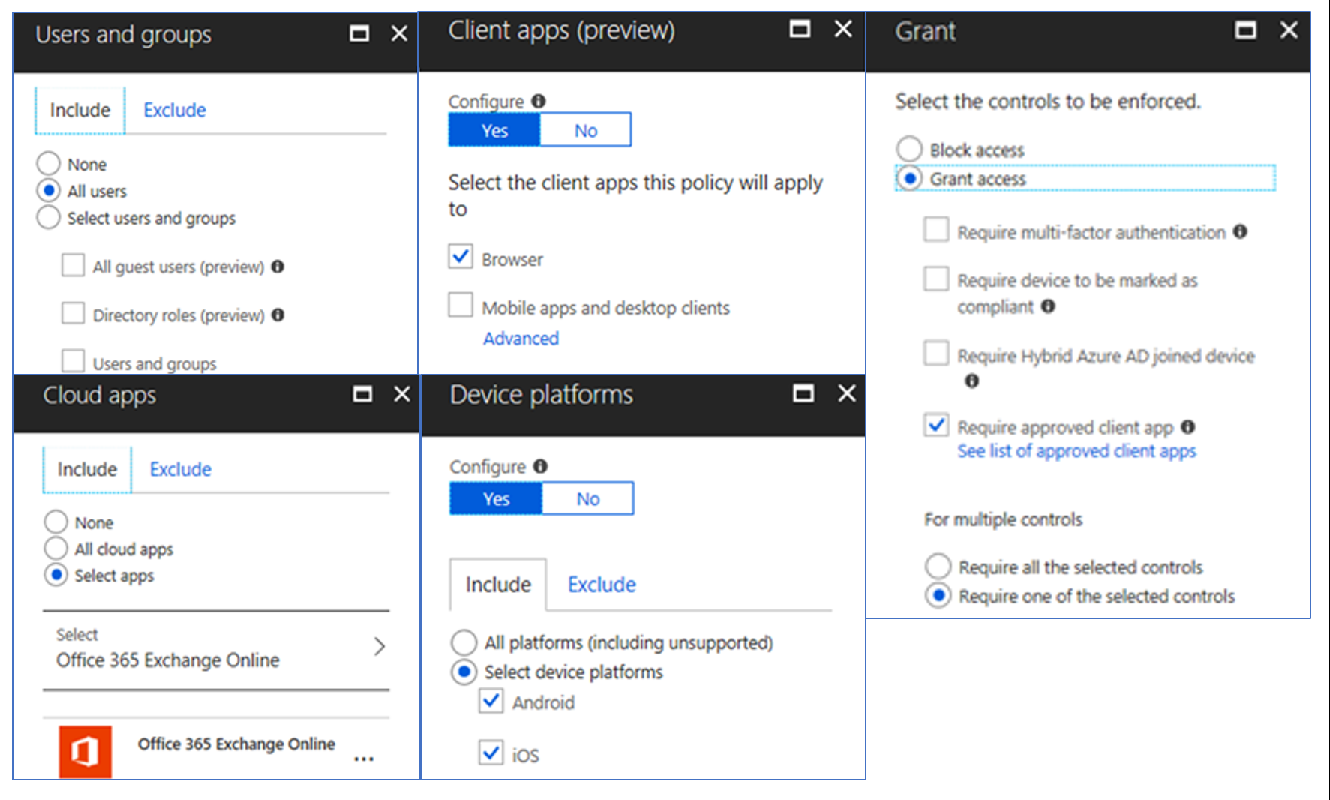
- Policy: scoped to EXO/SPO, targets Browser for iOS and Android, and requires devices use the Approved Client App
- Intune App Protection Policy
- Policy: targets the Intune Managed Browser (plus at least one other application*), configured to meet your desired security settings to protect your corporate data (i.e. disallow copy/paste to unmanaged locations, etc)
With these two policies, we lock down web traffic to corporate resources on mobile devices to the Intune Managed Browser, and then use Intune App Protection to ensure that the applications are managed with the application controls. This enables a managed experience when accessing corporate web resources, while also providing an improved end-user experience with SSO via the Managed Browser!
Configuration Steps
- Create the Conditional Access policy that targets EXO/SPO to force users who are accessing these resources via the Web are doing so via the Intune Managed Browser
- Create an Intune App Protection policy that targets the Intune Managed Browser and any other apps you plan on protecting
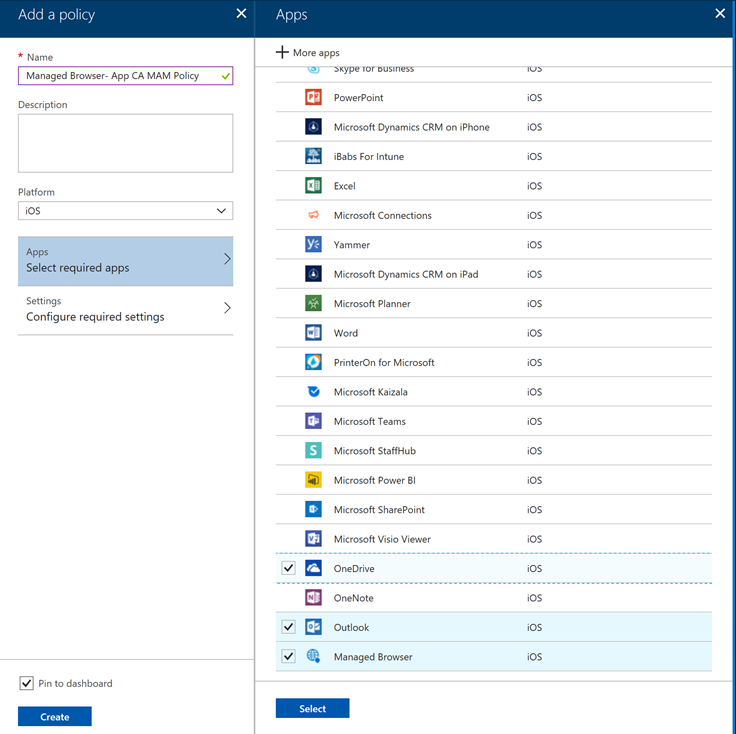
*NOTE: The Intune Managed Browser cannot be the only application you target with this policy. It does not have the ability to communicate with the App Protection service on its own, so a user will need to set up another managed application before the Managed Browser will receive policy
Once you have completed these two steps, you are ready to move on and start testing this scenario.
End-User Experience
Let's take a look at what the end-user experience looks like after you implement this scenario.
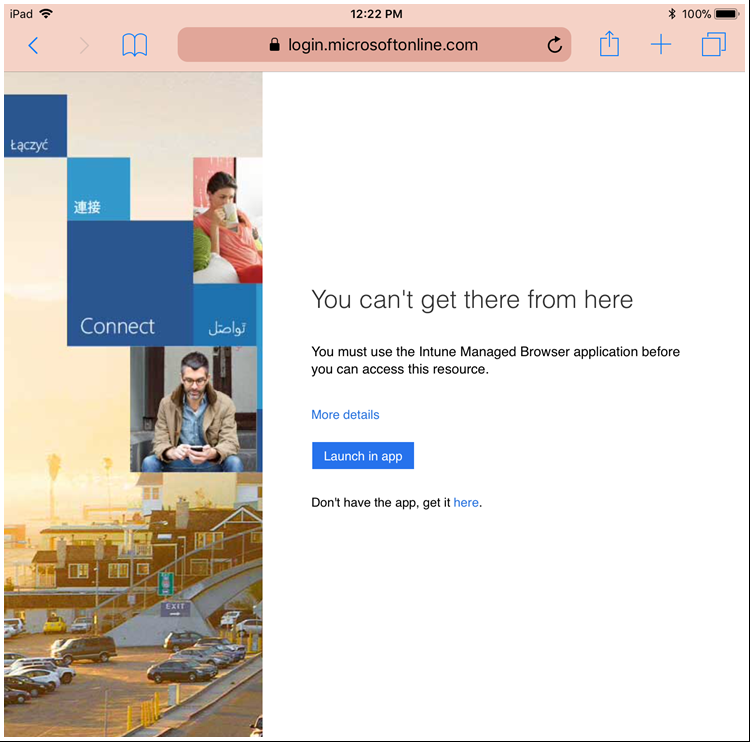
When a user opens the native browser on their device and tries to access Exchange Online or SharePoint Online/OneDrive content, they will see a message redirecting them to the Intune Managed Browser. To access the desired corporate resource, they simply click on "Launch in app" button and are seamlessly redirected if they already have the app installed. If they do not yet have it installed, there is a link they can click that will take them to their device's app store to download the application.
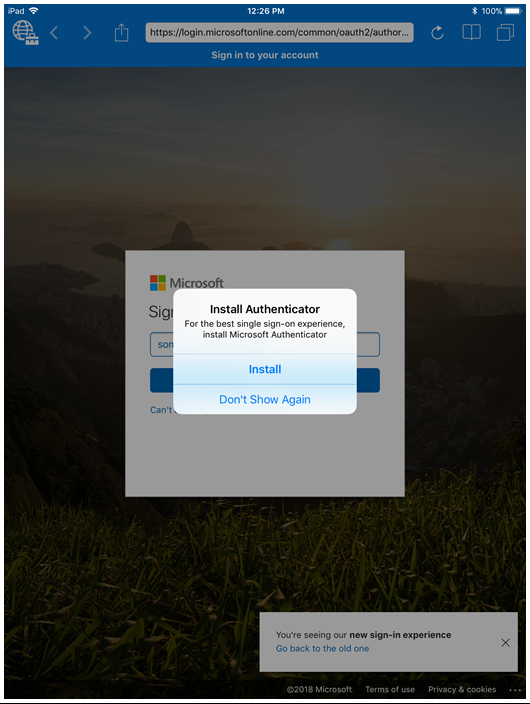
The first time users launch the Managed Browser, they will be prompted to install the Microsoft Authenticator application. This is our "broker" application that relays the identity of the application to Azure AD and allows the Conditional Access check to be satisfied. You can read more about "broker" apps and the entire validation process here.
The Authenticator app also provides SSO inside the Managed Browser for end-users. So once this app is installed and configured, they will be able to seamlessly sign in to Office 365 and other Azure AD web resources through the Managed Browser.
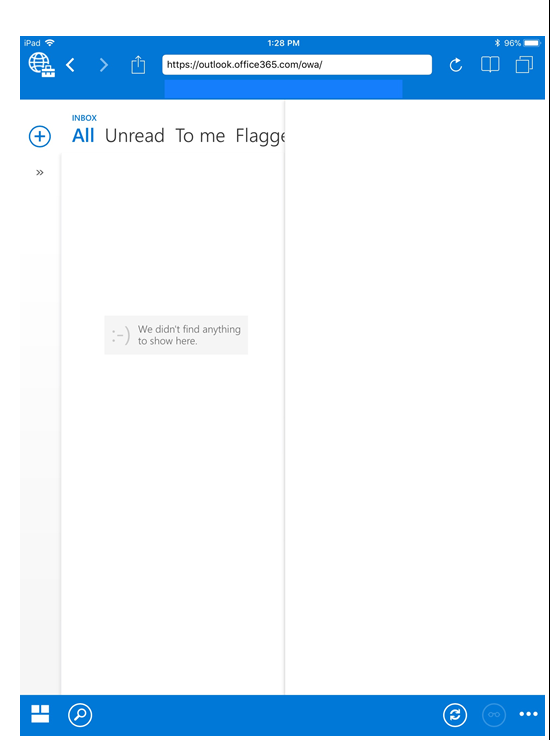
Once the Authenticator setup is complete, the end-user arrives at the link they were originally attempting to access in their device's native browser. So you can see below that they have landed in OWA and are successfully seeing their mailbox in the Managed Browser!
In Review
Scenario Goal: Ensure users access web resources (like OWA, SPO, OneDrive, etc) from an app with Intune App Protection applied- the Intune Managed Browser
Scenario Scope: iOS/Android
Recommended when…
- You allow browser access to corporate data on mobile devices
- You want to extend Intune App Protection capabilities to the browser
This wraps up our four-part series on Conditional Access and Scenarios for Success. We hope you have found it helpful and now find your environment a bit more secure! Have more questions about securing mobile device access to Office 365? Have you tried out these conditional access scenarios? Let us know in the comments below!