Microsoft Teams: Restrict Usage with Azure AD Conditional Access
Introduction:
In this blog post I will discuss how to use Conditional Access in Azure Active Directory (Azure AD) to restrict how Microsoft Teams is accessed by employees. This blog post will cover how to configure Conditional Access, and what the experience is like for users.
What is Conditional Access? Conditional Access is a feature of Azure AD that enables organizations to define specific conditions for how users authenticate and gain access to applications and services. For more information, see the following resource Conditional access in Azure Active Directory. Note, Conditional Access requires Azure AD Premium P1 or above. For more information, see Azure Active Directory pricing (Note, a 30 day trial is also available).
Scenario:
The are many ways Conditional Access can be used. In this blog post, a fictitious company Contoso, would like to give their retail employees access to Microsoft Teams however they have requirements that must be met:
- Retail employees are paid hourly and work at a company retail store. When the employee leaves work and is "off the clock", they are not allowed to access Microsoft Teams.
- When the employee leaves work, the app should not allow them to access data or services.
- When the employee returns to work, the app should allow them to access to all data and services within the app.
- These requirements will apply to all platforms where an employee can access Microsoft Teams (smartphone app, Windows, Mac, web browser, etc)
Based on these requirements and an understanding of the capabilities of Conditional Access, they came up with the following design and configuration:
Design notes:
All retail employees will be assigned to a security group titled Retail Staff. The Conditional Access policy will only be applied to employees that are a member of this security group.
The policy will only be applied to the Microsoft Teams append will include all platforms (Android, iOS, Windows Phone, Windows, Mac OS, etc.
The policy will apply to any location (IP address), but, locations with trusted IPs will be excluded. Contoso will add their public IP subnet to the list of trusted IPs.
The policy will apply to browser, mobile apps, and desktop clients.
Sign in risk will not be configured.
Access controls will be set to block. Require Multi-factor authentication, device compliance, etc will not be configured.
Session control will not be configured.
Employees will connect to a guest Wi-Fi network while in the store.
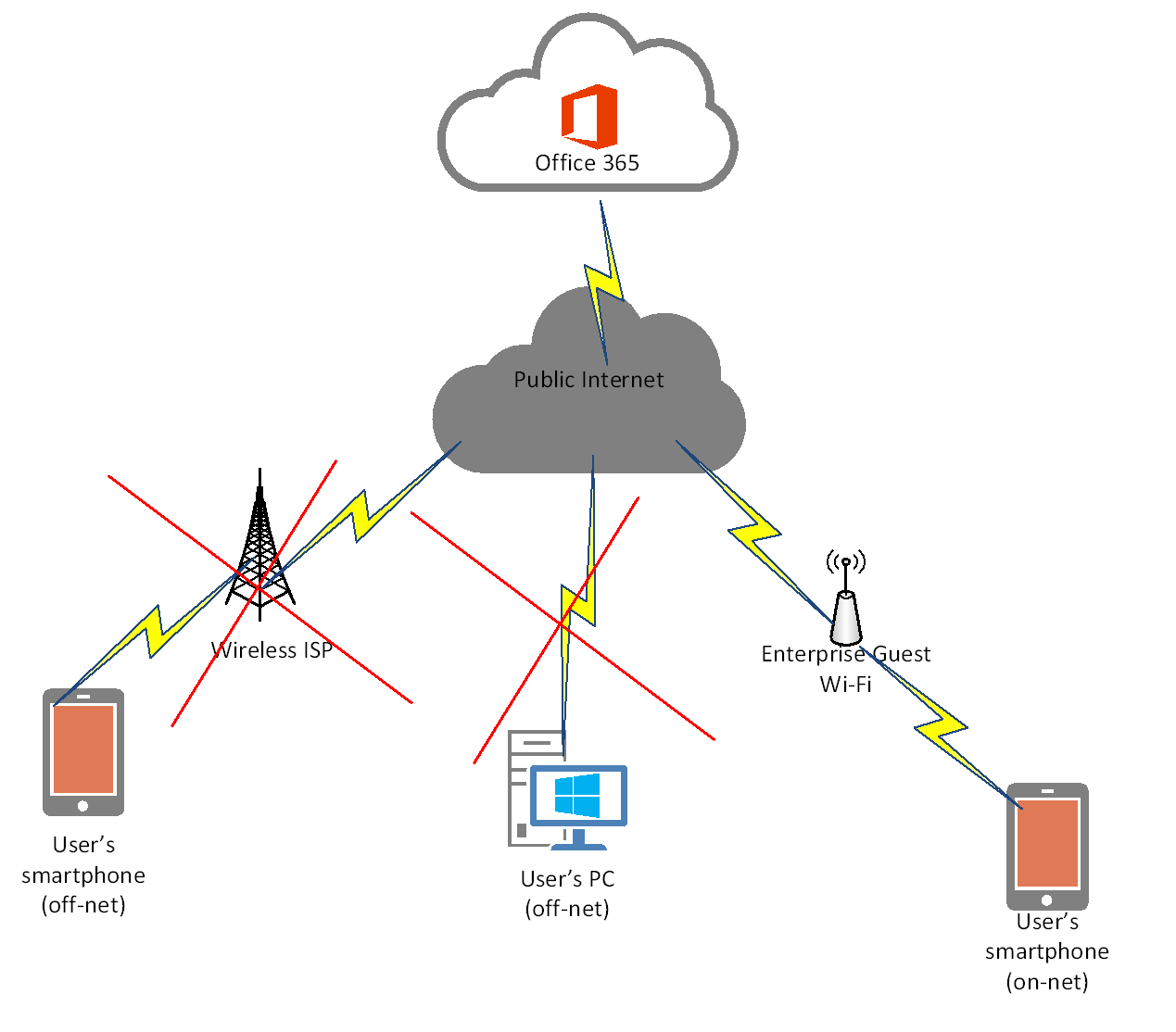
Let's get started on how to deploy this design.
First, assign Azure Active Directory Premium P1 licenses to users:
As mentioned previously Azure AD Premium P1 is required. For this scenario, I'm going to assign the license to my retail employee Megan:
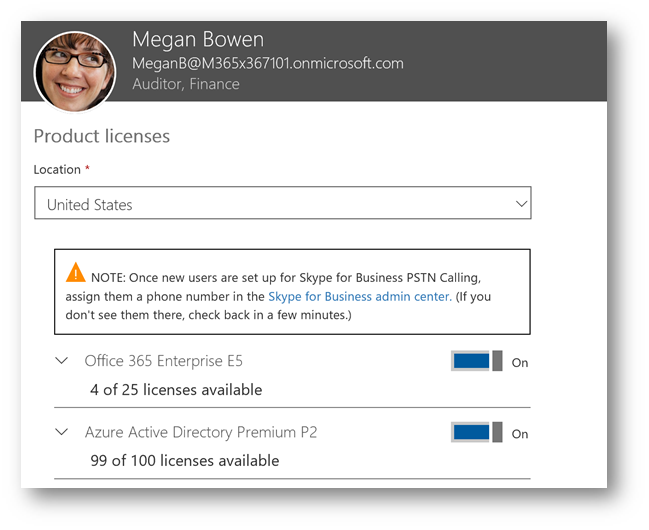
Note: You'll see that I'm using AzureAD Premium P2, this is because I'm using a few additional features such as Privileged Identity Management and Identity Protection that I will blog about in the future.
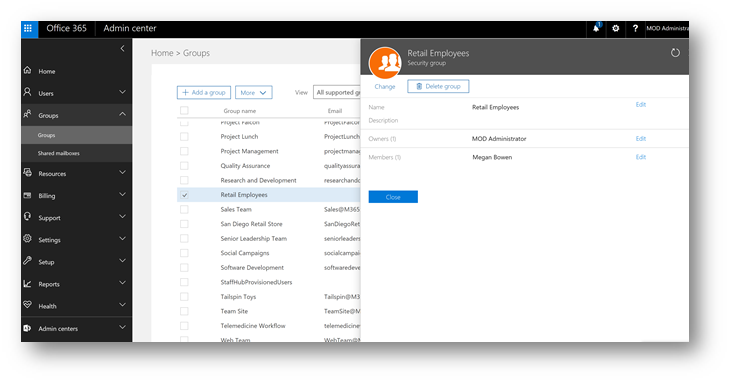
Add employees to the Retail Employees security group:
Next, I will add Megan to the Retail Employees security group I created. This will make it easy to manage the Conditional Access policy and assign users later:
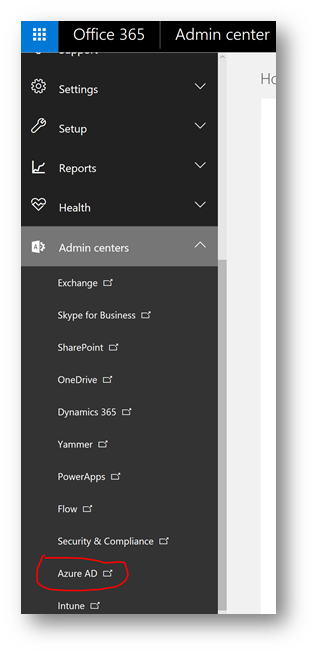
Launch the Azure Active Directory admin center:
Conditional Access is configured in the Azure Active Directory admin center. To launch this portal, on the left side of the Office 365 Admin Portal expand Admin centers and click Azure AD:
Note: A shortcut is to browse to aad.portal.azure.com
In the Azure Active Directory admin center, on the left side click Azure Active Directory:
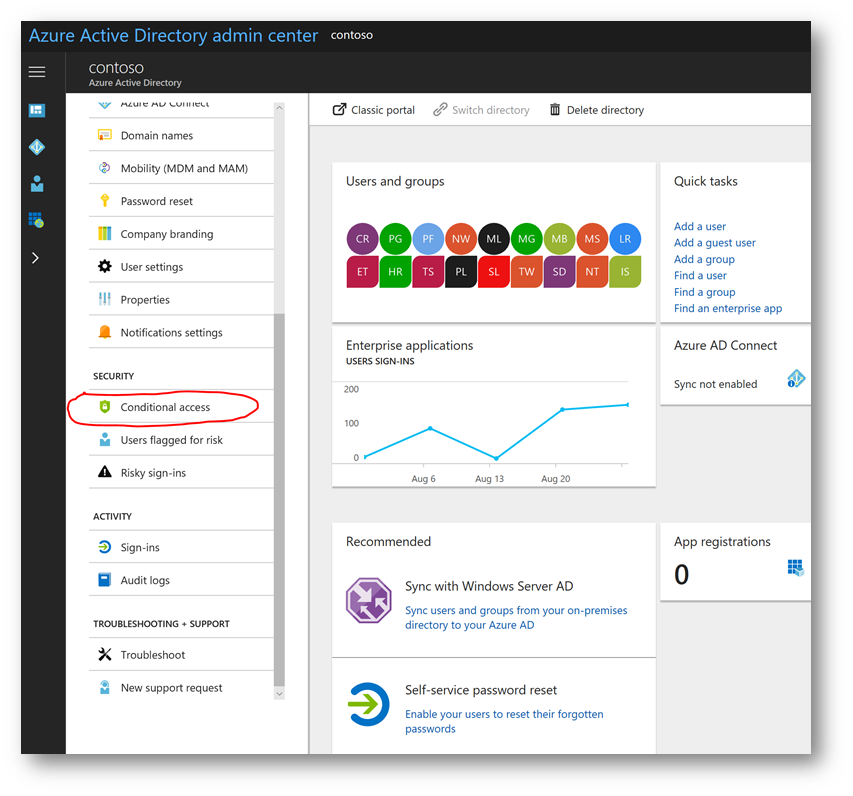
Next, scroll down and find the Security category and click Conditional Access:
Create Conditional Access Policy:
Next, click Create Policy:
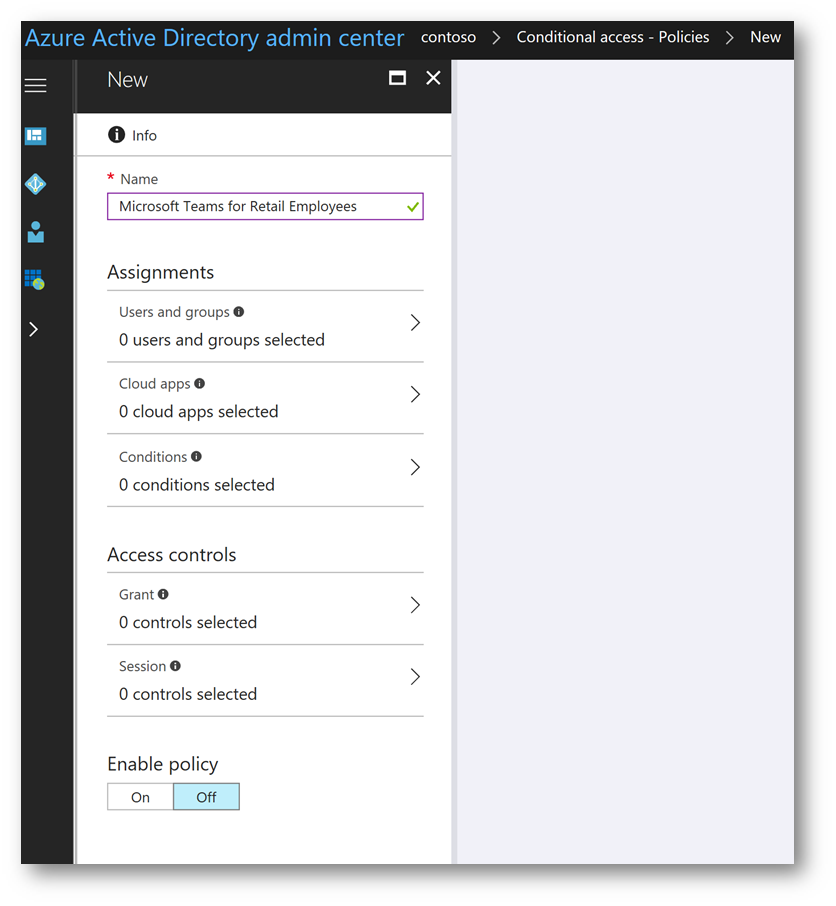
On the New blade, we will give the policy a name of Microsoft Teams for Retail Employees . Then click Users and Groups:
In the Users and groups blade, under the Include tab select the radio button for Select users and groups then click Select. On the Select blade, browse to the security group Retail Employees and place a check next to it. Then click the Select button at the bottom:
Note: If any employees should be exempt from the policy (i.e. the store manager) then the Exclude tab can be used.
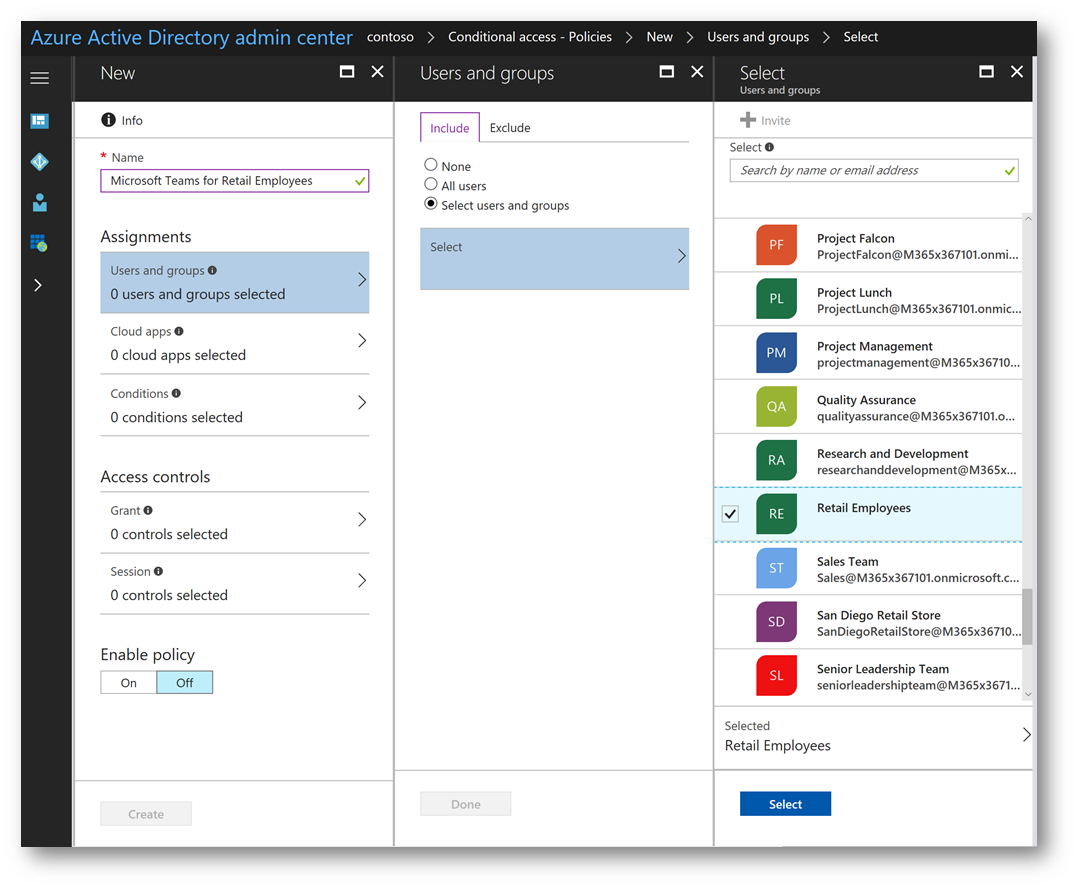
On the Users and groups blade click Done:
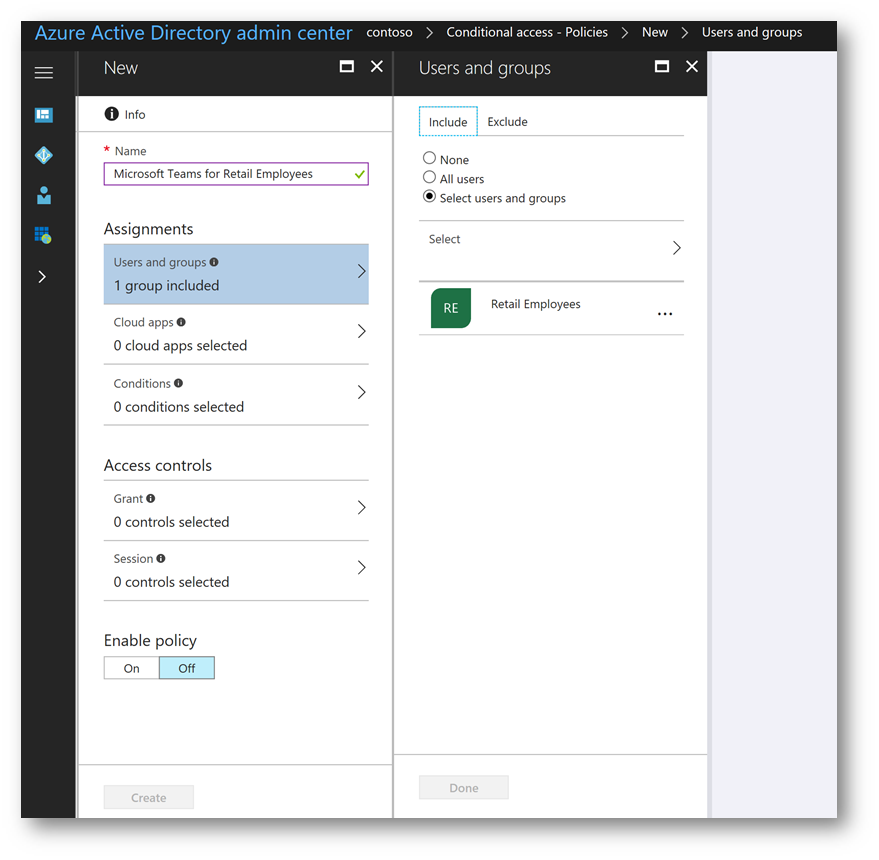
On the New blade click Cloud apps;
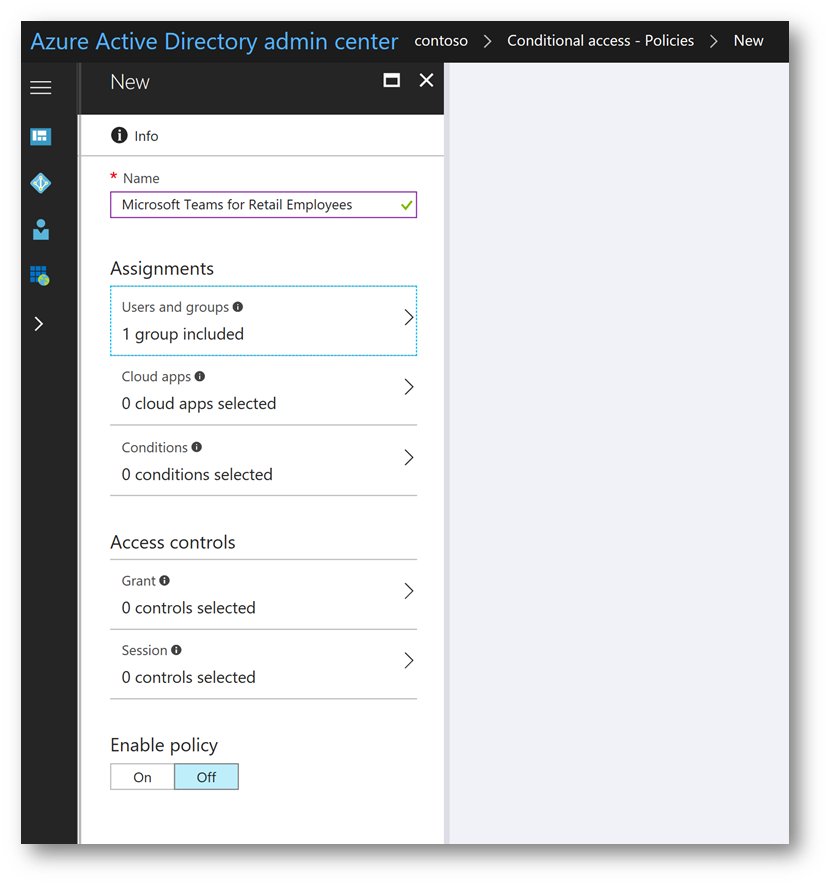
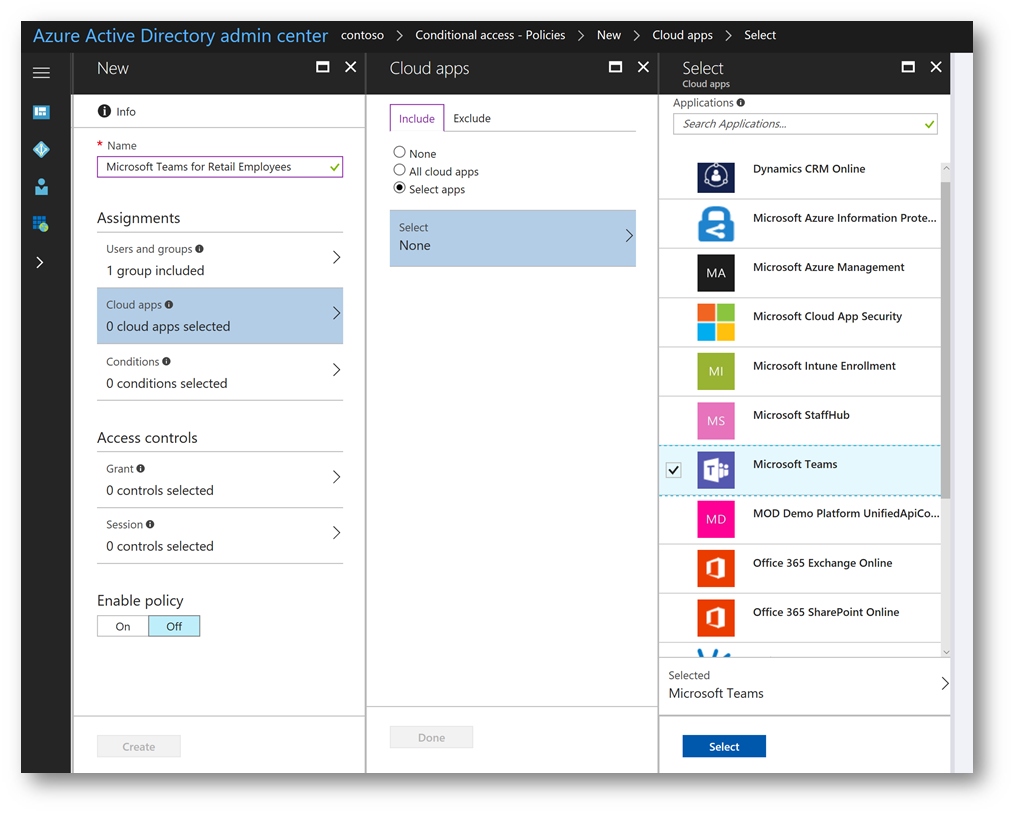
On the Cloud apps blade, under the Include tab click the radio button for Select apps then click Select. On the Select blade, find Microsoft Teams, place a check mark next to it then click Select. On the Cloud Apps blade click Done:
Back on the New blade, click Conditions. On the Conditions blade click Device platforms. On the Device platforms bade click Yes and select All platforms (including unsupported). Then click Done:
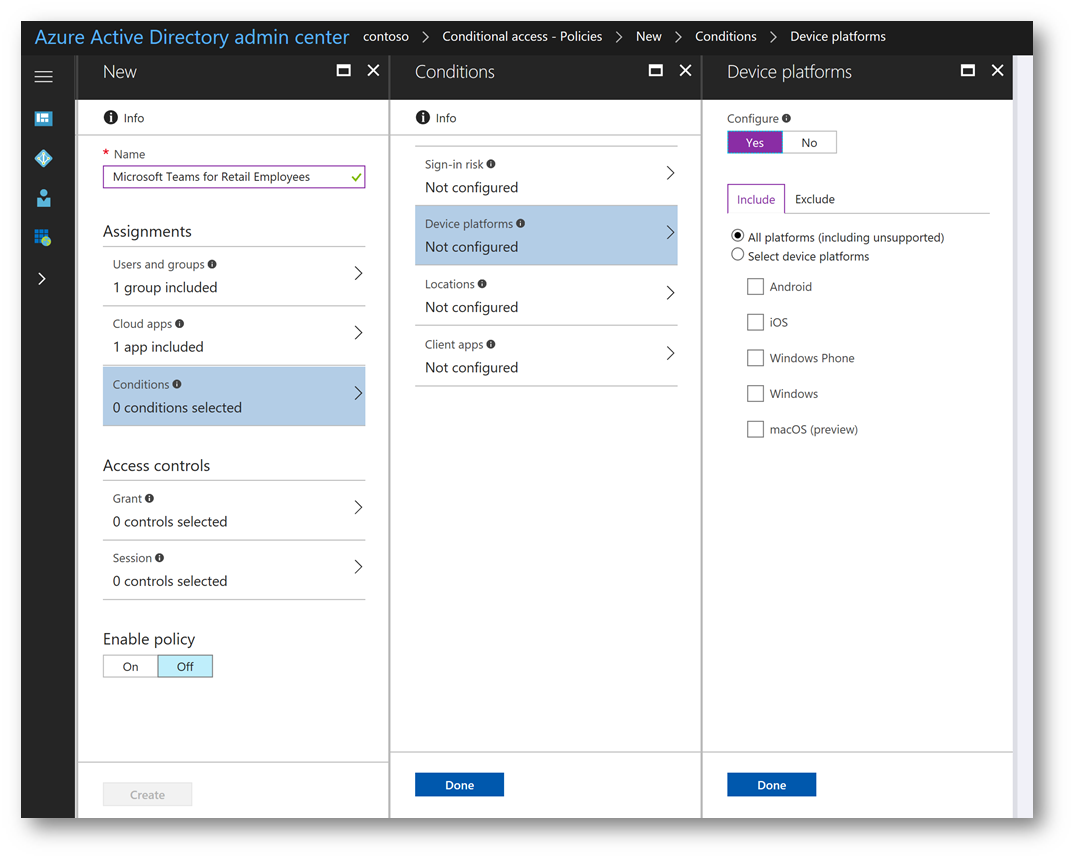
One the Conditions blade, click Locations. Click Yes and on the Include tab click Any Location then click the Exclude tab:
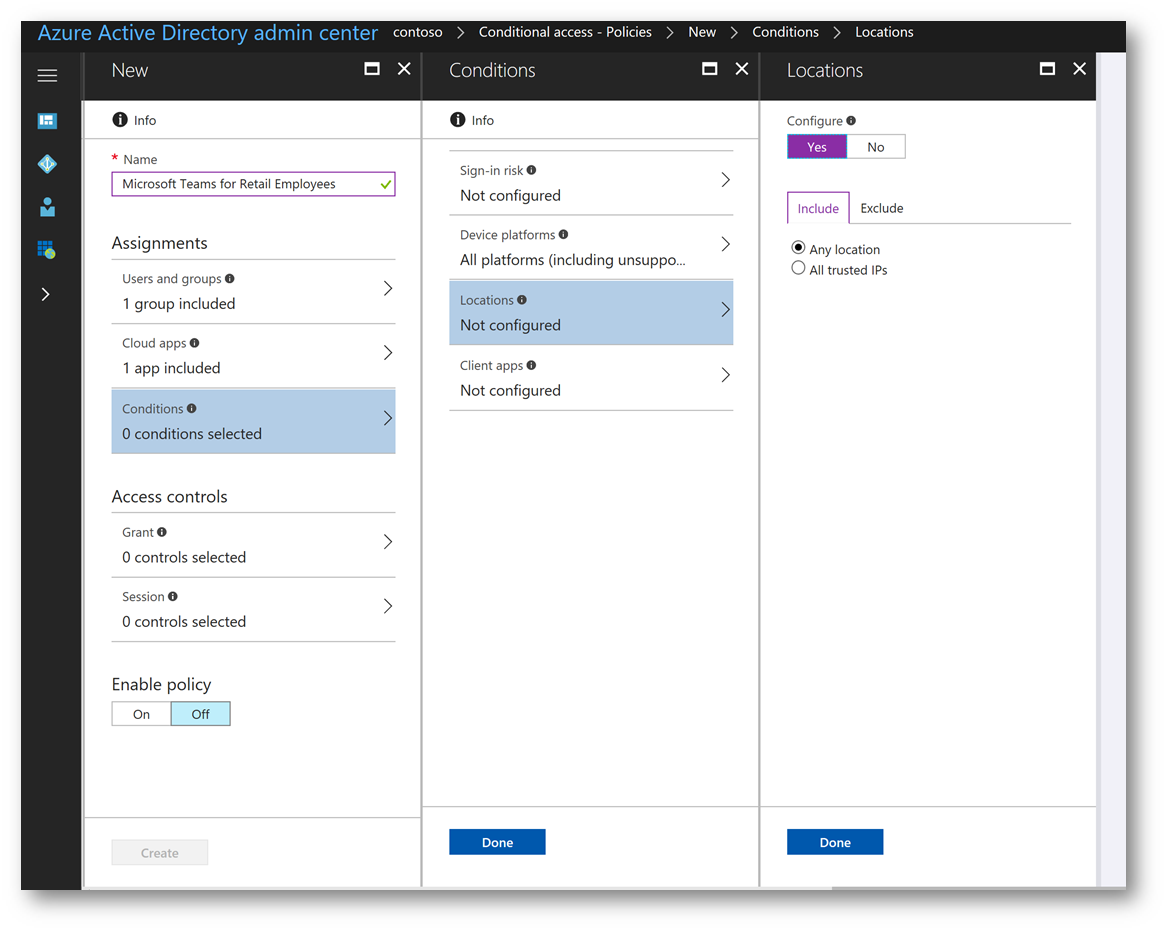
On the Exclude tab click the check box All trusted IPs then click the hyperlink Configure all trusted locations:
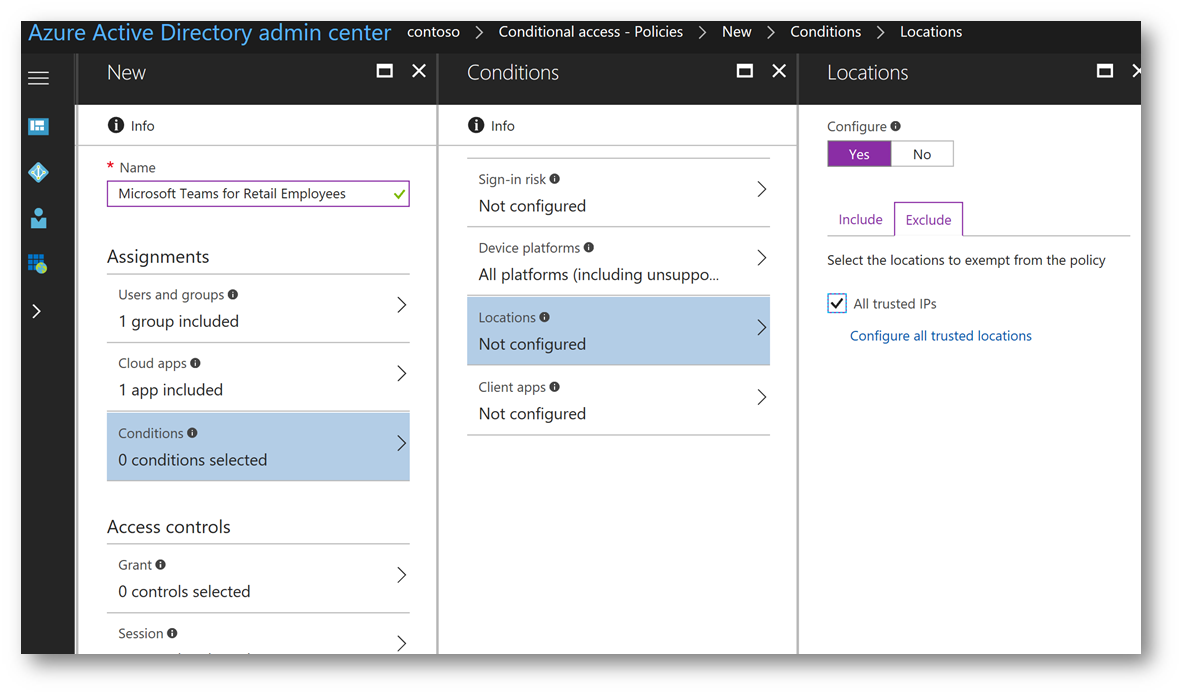
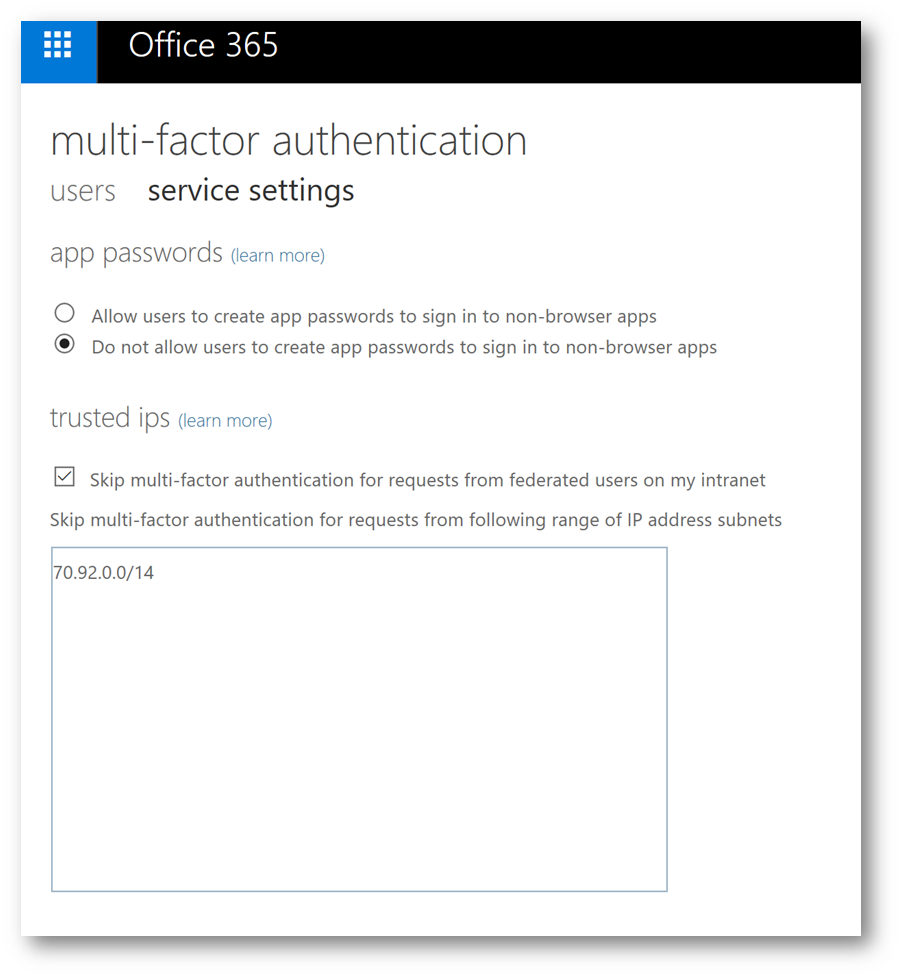
A new browser tab will launch, and you will be taken to the mult-factor authentication page. In the trusted ips box, type the IP address subnets of the public IP address of the retail store. In my example below, when the employee is in the retail store and connected to the guest Wi-Fi network it will use a public IP in the subnet of 70.92.0.0/14 to access Microsoft Teams in Office 365. By adding this subnet, this tells Conditional Access to exclude any authentication attempts coming from this subnet from the Conditional Access policy. Click Save at the bottom of the page and close the browser tab when finished:
Back in the Azure Active Directory admin center, click Done on the Locations blade:
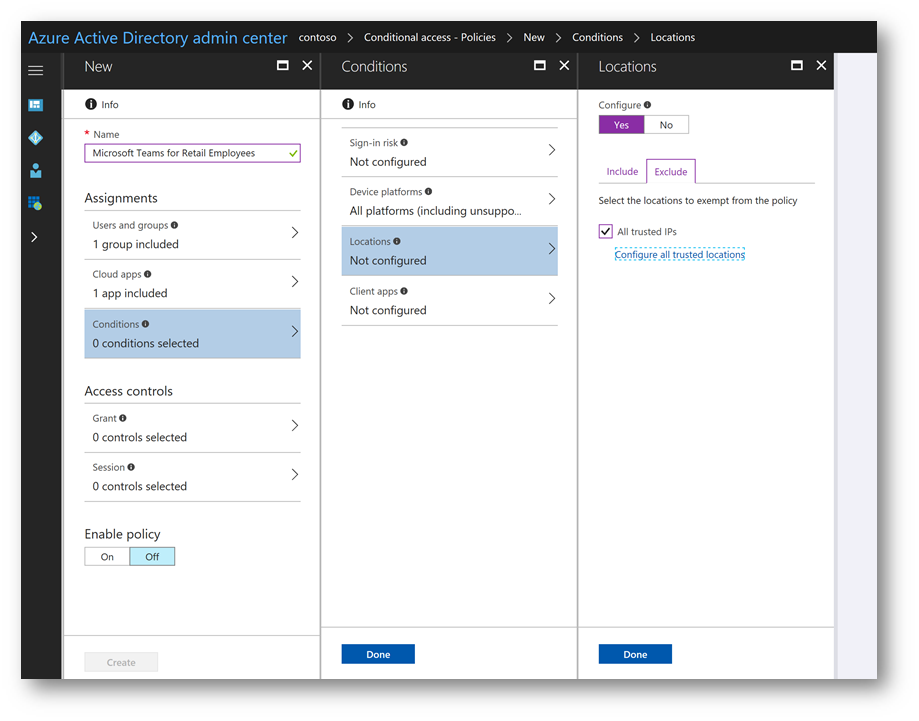
On the Conditions blade click Client Apps. On the Client Apps blade click Yes. Click the radio button Select Client Apps and select Browser and Mobile apps and desktop clients. Then click Done. Then on the Conditions blade click Done.
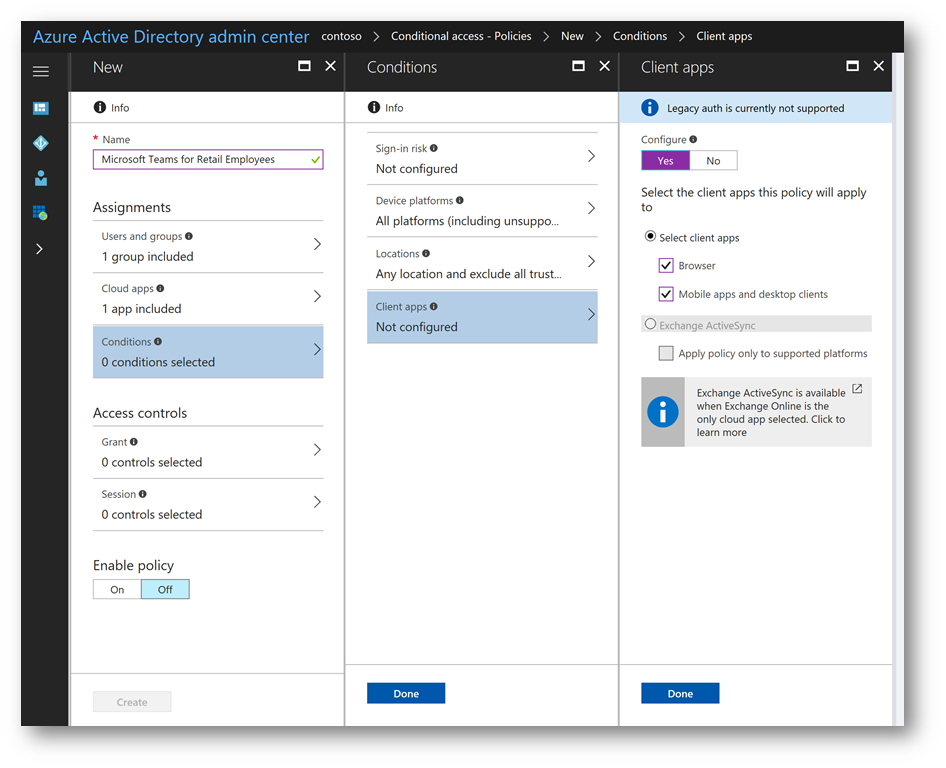
Back on the New blade, under Access controls click Grant. On the Grant blade click the radio button for Block access then at the bottom click Select:
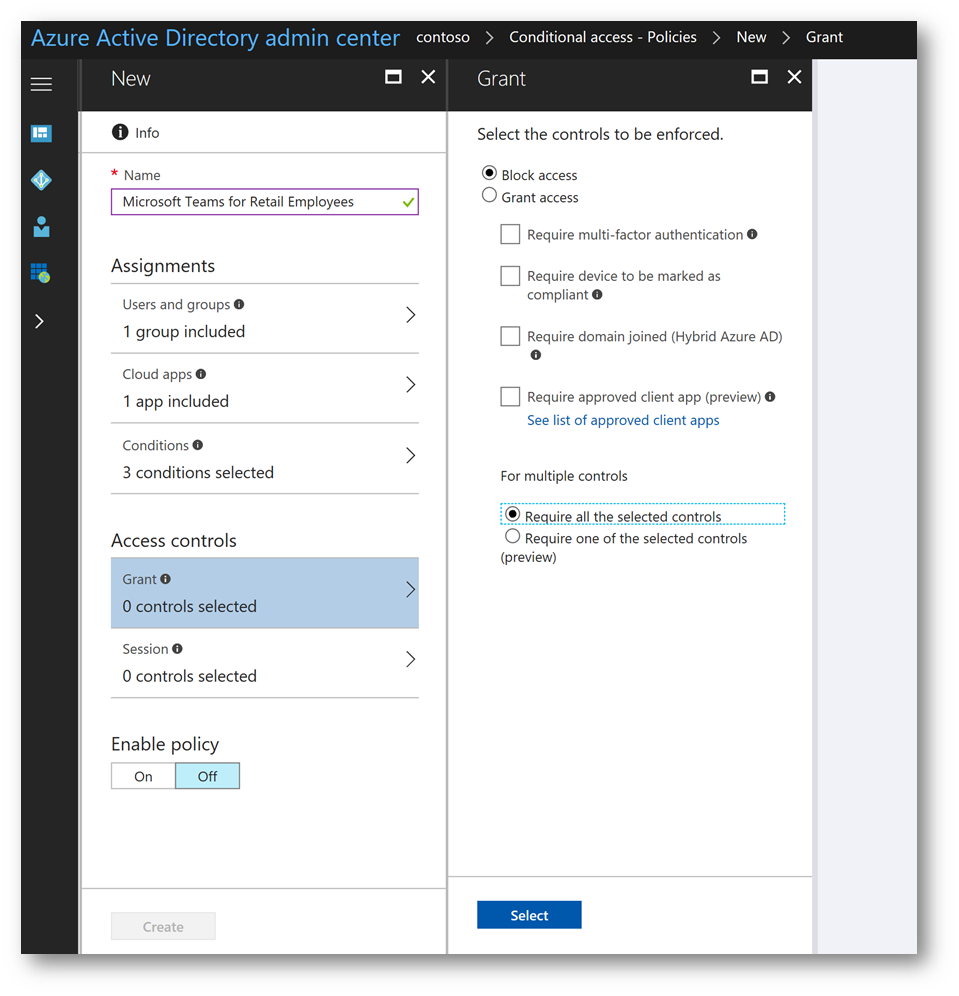
On the New blade click On to enable the policy then click Create to create the policy. Notice in the upper right corner a new toast notification will appear, indicating the policy is in the process of being enabled.
Close the Azure Active Directory admin center tab:
Test Conditional Access while on-network:
Now that the policy has been configured and enabled, let's test to see if the policy takes effect for a retail employee. I am going to connect an iPhone to the Wi-Fi network at the retail store, and launch the Microsoft Teams app.
I will be successfully authenticated and the app will load:
At this point, I can now use Microsoft Teams when on-network while connected to corporate guest Wi-Fi at the retail store. I will sign-out of the app when finished:
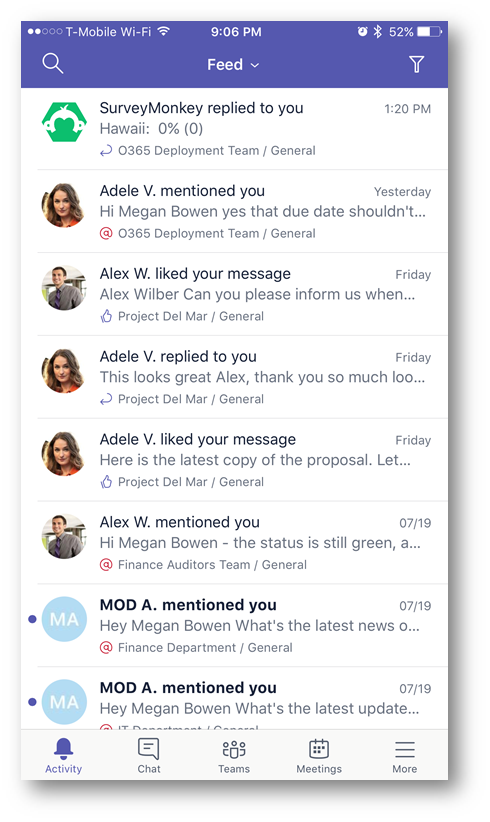
When accessing using a desktop web browser when on-network:
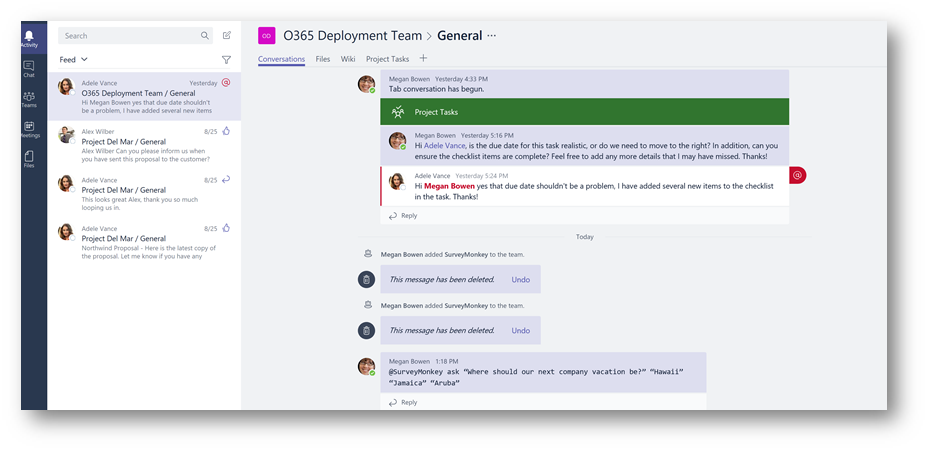
Test Conditional Access while off-network:
Next, I will turn off Wi-Fi on the iPhone so that I am connected to the cellular network to simulate leaving the retail store and disconnecting from the corporate guest Wi-Fi network.
IMPORTANT: The app will automatically re-authenticate every 60 minutes. So, if an employee leaves the store at 5pm, they may still have access to the app until 6pm when it re-authenticates and the Conditional Access policy kicks in.At that point, when they open the app again, they will receive an error due to the policy. I'll show that in just a moment.
While disconnected from the Wi-Fi network, I'm going to attempt to sign-in to the Microsoft Teams app:
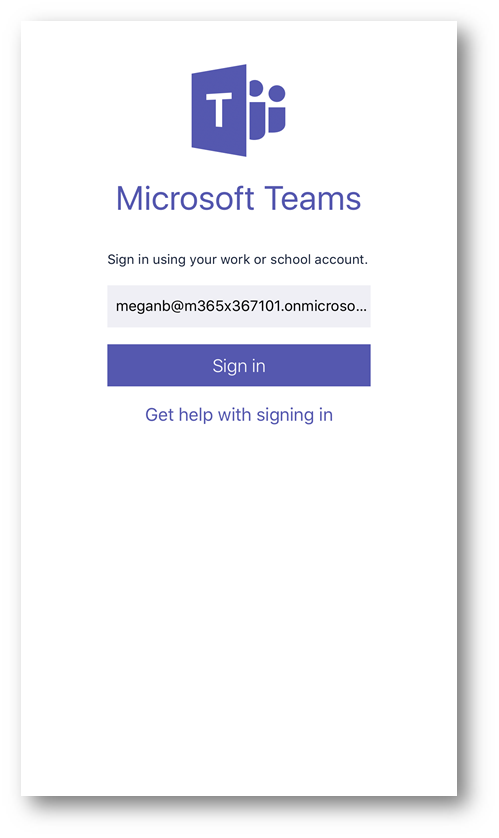
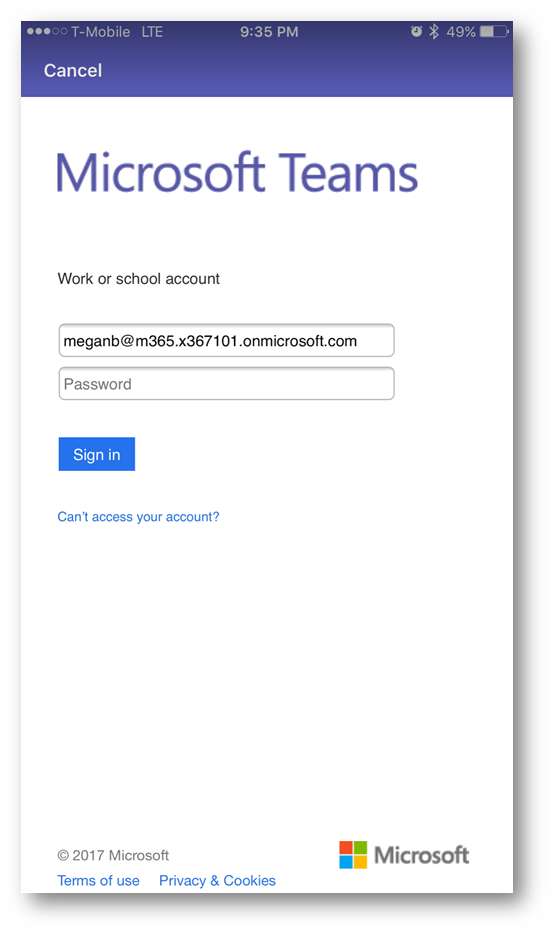
Next, after tapping Sign in will be challenged to enter my password. So, I'll type in my password and tap Sign in
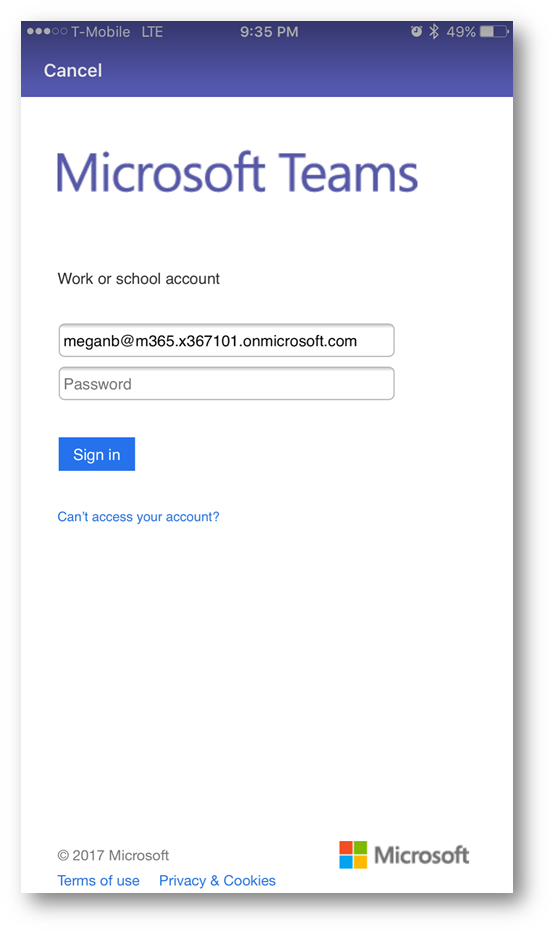
The Conditional Access policy will kick in, and I am presented with the following message. Notice I cannot proceed with sign in:
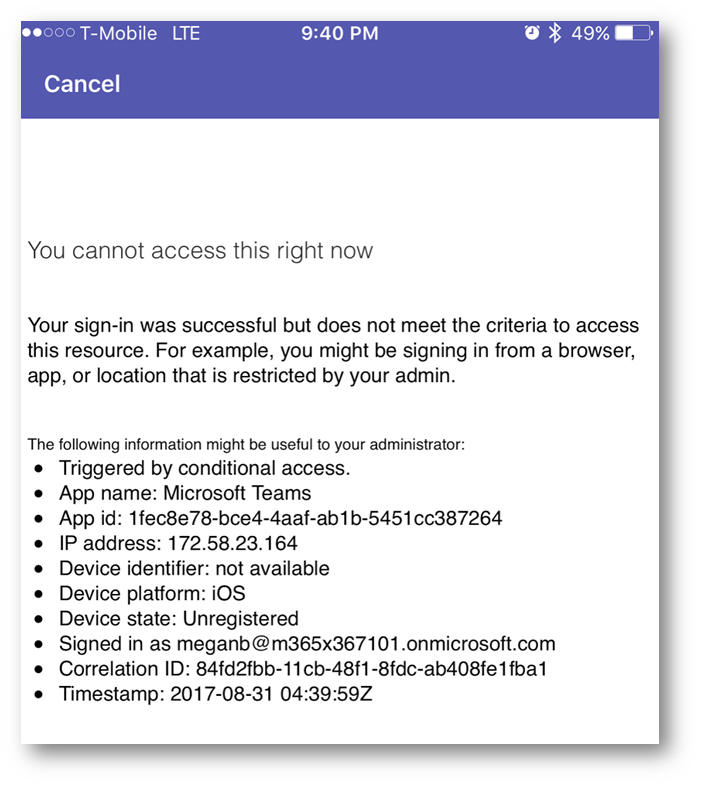
When testing from the desktop web browser when off network:
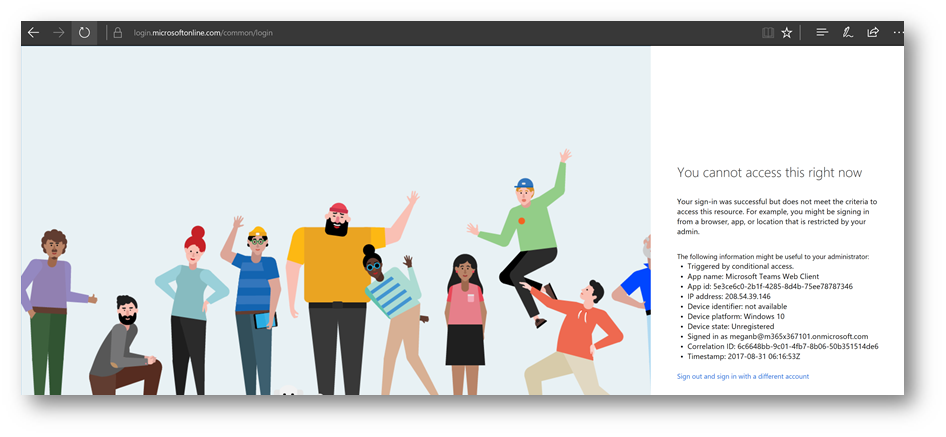
User experience when app times out after 60 minutes:
When the app re-authenticates I will be challenged with an authentication prompt to re-enter my credentials:
Conclusion: Conditional Access is an effective way to enable access to resources after specific conditions have been met. In this scenario, we saw how this can be used to enable a retail employee to use Microsoft Teams while at work, but then not be allowed to use it after work. If you have questions, comments, or feedback on this blog post please don't hesitate to post in the comments below. My top priority is to ensure the post is accurate and meets the needs of my readers. Enjoy! –Matt Soseman
P.S. Stay tuned for an additional blog post on using Intune Mobile Application Management (MAM) with Microsoft Teams.