Desktop Security Made Easy and Free
There are basically three basic aspects to securing your Windows 7 desktop, all are possible for free to home users and small businesses and with market leading technologies. In this post I’ll discuss how to work with these basic component and how some of those same technologies can be scaled for big business too. The technologies we’ll take a look at are: Anti-Malware (Antivirus, spyware, adware and phishing) courtesy of Microsoft Security Essentials and Forefront, Windows Firewall and Windows Update.
Anti-malware
Lets start with Microsoft Security Essentials which as of 7th October is free for small businesses (small is less than 10 PCs). Lets just hold on that for a moment. Just over a year ago Microsoft had no free anti-malware option for home users, now we have a product that gained huge respect in that space and has been expanded to small businesses. What people like most about the software is that it follows an almost “Install and forget” model, only really letting you know it exists when you need to take some action. The quality of the protection is really high too in fact it uses the same signatures as our Forefront protection engine that big businesses use.
So what is the experience like? Lets take a look at the user experience first. After MSE is installed the latest definitions (the details about how to match viruses) are downloaded and a scan of the computer is undertaken to establish that everything is ok.
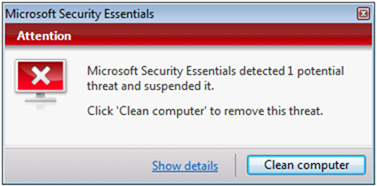
When a virus is found, in this case it’s just a test virus, the user gets a message pop up letting them know that’s something's been found.
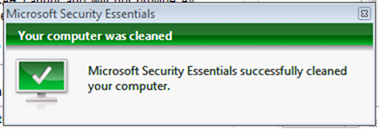
Clicking Show details gives them all the info they need to make an informed decision and it’s a simple case of clicking Clean computer to remove the infection
All the red and green colouring on the messages and dialogues mean that there’s no confusion as to there being a problem that needs some type of action.
As MSE isn't intended for larger install bases it doesn’t have the capabilities, such as centralised alerting and policy, that commercial products do. Instead the focus is on making the users journey easier to understand. That said we have some great alternatives to that do scale really well. When it is released Windows Intune will be one of those products and it focuses very neatly on providing that control whilst still maintaining the ease of use that consumers are used to.
Right now though businesses over 10 users will want to go for something like Forefront Client Security that allows a more granular level of customisation and alerting. Forefront Endpoint Protection 2010 is the next version of our enterprise level client offering however that’s currently in Beta but available for download.
Taking a quick look through Forefront is a tough thing to do because essentially there are lots of components that you need to pick up for your enterprise. There is however a great learning resource for it on TechNet.
Andrew has summed it all up expertly with a video:
Desktop security one size does not fit all
Firewall
Windows Firewall in Windows 7 can alter the level of restriction around what can be accessed network wise depending up on the network you’re currently connected to. For example at home you can have the ability to share and stream music to other computers in the home enabled, at work you can have that same access disabled and in public places you can ensure that all the sharing features of Windows 7 are disabled.
Most consumers come across this when they connect to WiFi in a new location and they receive a pop up asking them to classify the type of the location they just connected to. It’s very good to get you users into the habit of classifying correctly to help them protect themselves.
Windows Firewall can be configured for enterprise use using group policy and with that you can control specific applications to be allowed through the firewall, specific applications and ports to be blocked to prevent them accessing the network and what happens in each of the profiles.
Patching
Patching is one of those things that you just have to take care of if you don’t it's like allowing a whole to form in the wall of your house without taking care of it, one day someone is going to try to get in through the hole or at least they might try to take a peak. Most IT Professionals who manage Windows are used to the regular and predictable patch Tuesday model that Microsoft have employed for years. One of the great bits of feedback that we get about this is that it’s got the high level of predictability that allows you to plan around the rhythm of releasing patches at the same point in time, wouldn’t it make life easier if everyone followed the same rhythm?
There are again lots of ways for you to manage patching in your environment. If you have a small business of 10 or so machines you’ll probably find it easiest to just have Windows automatically pull updates from Windows Update (which by the way is a massive Microsoft cloud that regularly handles millions of update requests totally seamlessly). If you’re larger or you have very limited bandwidth available you’ll want to think about deploying Windows Software Update Services.
WSUS looks at Microsoft's Windows Update servers and watches for new updates to be released, when they are they’re downloaded to the WSUS server. WSUS essentially replaces the public Windows Update servers as far as the clients are concerned. Because WSUS comes within the control of your network you can control which updates are made available to your clients, so if you should have a particular update that you know breaks your line of business (LOB) apps you can hold off on installing it until you’ve had time to fix the LOB app. WSUS also allows you to test updates to avoid any problem with your LOB apps by grouping your clients, that way you can test new patches on a group of typical machines before rolling a patch to your entire estate and potentially hitting any repercussions from incompatibilities.
You need to do quite a bit of planning to implement WSUS optimally but the guide makes lots of sense. WSUS can be seen as a core part of a Windows infrastructure and it not only controls updates for Windows but it’s leveraged by other services. For example Forefront Client Security uses the WSUS service to manage updates.
To step up the management a level then System Center Essentials 2010 or the full System Center are needed to provider more granular and device specific management.
Of course all of this is just a part of deploying your Windows 7 Optimized Desktop and Springboard has some stunning resources for you there.