Security baseline for Windows 10 v1607 (“Anniversary Update”) and Windows Server 2016
Microsoft is pleased to announce the release of the security configuration baseline settings for Windows 10 version 1607, also known as “Anniversary Update” and internally as “Redstone 1”. The downloadable attachment to this blog post includes importable GPOs, tools for applying the GPOs, custom ADMX files for “pass the hash” mitigation and legacy MSS settings, and all the settings in spreadsheet form. It also includes spreadsheets generated from Policy Analyzer that show differences from past baselines and brief descriptions of the reasons for the differences, and a similar spreadsheet listing the differences between the Member Server and Domain Controller baselines.
Download the content from the Microsoft Security Compliance Toolkit (click Download and select Windows 10 Version 1607 and Windows Server 2016 Security Baseline.zip).
The .CAB files corresponding to these baselines for the Security Compliance Manager (SCM) are being worked on and should be available for download through SCM by the end of October. In the meantime, the downloadable materials on this blog post should provide most everything you need to move forward. We are also preparing an updated version of Policy Analyzer and hope to publish it soon. [Update, 17-Nov-2016: the SCM CAB files corresponding to these baselines are now published. Install and start SCM v4.0 on an internet-connected system: it will notify you that the new baselines are available if it is configured to check for updates automatically, or you can select "Check for updates" from the File menu.]
The main changes in the Windows 10 v1607 baseline since that for Windows 10 v1511 include:
- Windows Defender is recommended for enterprise use and important Defender settings are now part of the Windows baseline.
- Enforcing the blocking of use of SSL 3.0 and out-of-date ActiveX controls in Internet Explorer.
- Disabling the Mobile Hotspot feature, which non-admins could otherwise enable.
- Improvements in auditing settings.
- Change in User Rights Assignment so that administrators can choose to enable Remote Desktop.
- Continued removing unnecessary enforcement of defaults, consistent with our previously-documented philosophy.
In addition to those, the Windows Server 2016 Member Server baseline removes settings for the Microsoft Edge browser that were in the Windows Server 2016 Technical Preview 5 baseline, as Microsoft Edge is no longer present in Windows Server.
To assist with evaluation, we have built spreadsheets listing differences between the latest baselines and previous baselines, along with explanations for the differences. Download here . The spreadsheets with "Raw" in the file name includes detailed information about the differences; the ones with "Explanation" in the file name removes detailed columns such as raw registry value and data type, and adds a "Reason for difference" column. The differences captured are between:
- Windows 10 v1511 (TH2) to Windows 10 v1607 (RS1)
- Windows Server 2012 R2 to Windows Server 2016 - Member Server
- Windows Server 2012 R2 to Windows Server 2016 - Domain Controller
- Windows Server 2016 TP5 to Windows Server 2016 RTM - Member Server
- Windows Server 2016 Member Server to Domain Controller
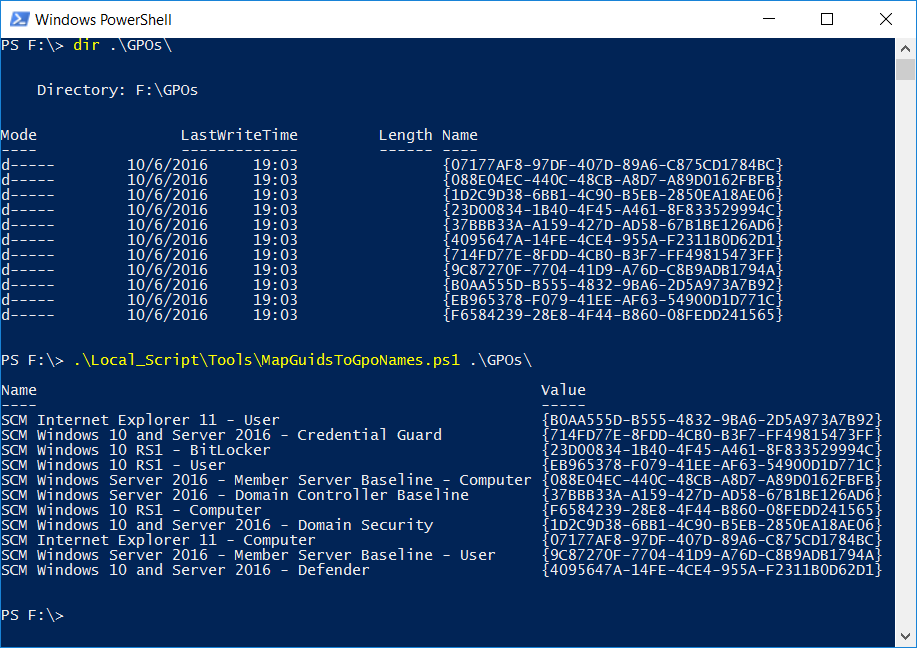
For those who have used the Local_Script tools in the download packages for previous baselines, we’ve changed its implementation. We used to copy GPO artifacts such as registry.pol files into the Local_Script directory and rename them. This time, the scripts reference the GPO files in their original locations. Because all GPO backup directory names are GUIDs, it can be difficult to identify which GUID is associated with which GPO. To help, we have added a simple PowerShell script that maps the GUIDs in a GPO backup directory hierarchy to the corresponding GPO names. This screenshot demonstrates: