Using Protected Groups to Secure Privileged User Accounts
Benefits
Members of the Protected Users group who are signed-on to Windows 8.1 devices and Windows Server 2012 R2 hosts can no longer use:
- Default credential delegation (CredSSP) - plaintext credentials are not cached even when the Allow delegating default credentials policy is enabled
- Windows Digest - plaintext credentials are not cached even when they are enabled
- NTLM - NTOWF is not cached
- Kerberos long term keys - Kerberos ticket-granting ticket (TGT) is acquired at logon and cannot be re-acquired automatically
- Sign-on offline - the cached logon verifier is not created
If the domain functional level is Windows Server 2012 R2 , members of the group can no longer:
- Authenticate by using NTLM authentication
- Use Data Encryption Standard (DES) or RC4 cipher suites in Kerberos pre-authentication
- Be delegated by using unconstrained or constrained delegation
- Renew user tickets (TGTs) beyond the initial 4-hour lifetime
Requirements
The PDCe role should be hosted on a domain controller that runs Windows Server 2012 R2 to create the Protected Users security group.
Hosts must run Windows 8.1, Windows Server 2012 R2 or later to provide client-side restrictions for Protected Users. Members of this group have no additional protection if they are logged on to a device that runs a version of Windows earlier than Windows 8.1.
Domain controller-side restrictions for Protected Users require the domain functional level to be Windows Server 2012 R2 or later.
Action
Simply add users to the group, using UI tools such as Active Directory Administrative Center (ADAC) or Active Directory Users and Computers, or a command-line tool such as Dsmod group, or the Windows PowerShellAdd-ADGroupMember cmdlet
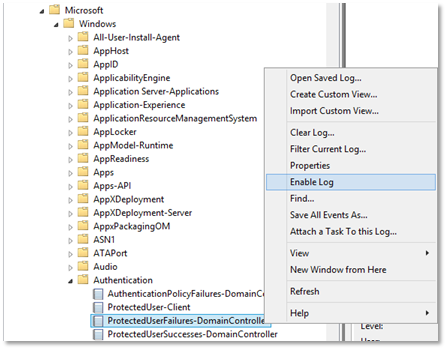
To track events, enable the following logs on domain controllers:
- Microsoft-Windows-Authentication/ProtectedUserFailures-DomainController
- Microsoft-Windows-Authentication/ProtectedUserSuccesses-DomainController
Impact
Members of the Protected Users group must be able to authenticate by using Kerberos with Advanced Encryption Standards (AES). The built-in administrator as well as any account, which has a password that was changed at a domain controller that runs an earlier version of Windows Server, is locked out. Therefore, follow these best practices:
Do not test in domains unless all domain controllers run Windows Server 2008 or later.
Change password for each user before adding the account to the Protected Users group or ensure that the password was changed recently on a domain controller that runs Windows Server 2008 or later.
Membership of the Protected Users also affect the Kerberos TGT lifetime and renewal times:
| Kerberos Policy | Default | Protected Users |
| Maximum lifetime for user ticket | 10 hours (600 minutes) | 240 minutes |
| Maximum lifetime for user ticket renewal | 7 days (10,080 minutes) | 240 minutes |
Validation – Success
Connecting to server using RDP. Using the DNS name of the server results in Kerberos being used for authentication
Log Name: Microsoft-Windows-Authentication/ProtectedUserSuccesses-DomainController
Source: Microsoft-Windows-Kerberos-Key-Distribution-Center
Date: 2/5/2018 10:38:39 PM
Event ID: 303
Task Category: None
Level: Information
Keywords:
User: SYSTEM
Computer: RootDC01.Litware.com
Description:
A Kerberos ticket-granting-ticket (TGT) was issued for a member of the Protected User group.
Account Information:
Account Name: BBanner
Supplied Realm Name:
User ID: LITWARE\BBanner
Authentication Policy Information:
Silo Name:
Policy Name: AuthPol - Tier_0_Accounts_Devices
TGT Lifetime: 240
Device Information:
Device Name:
Service Information:
Service Name: krbtgt/LITWARE
Service ID: LITWARE\krbtgt
Network Information:
Client Address: ::ffff:10.10.20.24
Client Port: 49204
Additional Information:
Ticket Options: 0x78
Result Code: 0x0
Ticket Encryption Type: 0x7
Pre-Authentication Type: 2
Certificate Information:
Certificate Issuer Name:
Certificate Serial Number:
Certificate Thumbprint:
Certificate information is only provided if a certificate was used for pre-authentication.
Pre-authentication types, ticket options, encryption types and result codes are defined in RFC 4120.
Log Name: Microsoft-Windows-Authentication/ProtectedUserSuccesses-DomainController
Source: Microsoft-Windows-Kerberos-Key-Distribution-Center
Date: 2/5/2018 10:38:39 PM
Event ID: 304
Task Category: None
Level: Information
Keywords:
User: SYSTEM
Computer: RootDC01.Litware.com
Description:
A Kerberos service ticket was issued for a member of the Protected User group.
Account Information:
Account Name: BBanner@LITWARE.COM
Account Domain: LITWARE.COM
Logon GUID: {9fdc2786-483a-81c3-17ce-43276cb9e55e}
Authentication Policy Information:
Silo Name:
Policy Name:
Device Information:
Device Name:
Service Information:
Service Name: ROOTMS04$
Service ID: LITWARE\ROOTMS04$
Network Information:
Client Address: ::ffff:10.10.20.24
Client Port: 49205
Additional Information:
Ticket Options: 0x7B
Ticket Encryption Type: 0x1F
Failure Code: 0x0
Transited Services: -
This event is generated every time access is requested to a resource such as a computer or a Windows service. The service name indicates the resource to which access was requested.
This event can be correlated with Windows logon events by comparing the Logon GUID fields in each event. The logon event occurs on the machine that was accessed, which is often a different machine than the domain controller which issued the service ticket.
Ticket options, encryption types, and failure codes are defined in RFC 4120.
Log Name: Security
Source: Microsoft-Windows-Security-Auditing
Date: 2/5/2018 10:40:40 PM
Event ID: 4768
Task Category: Kerberos Authentication Service
Level: Information
Keywords: Audit Success
User: N/A
Computer: RootDC01.Litware.com
Description:
A Kerberos authentication ticket (TGT) was requested.
Account Information:
Account Name: BBanner
Supplied Realm Name: LITWARE.COM
User ID: LITWARE\BBanner
Service Information:
Service Name: krbtgt
Service ID: LITWARE\krbtgt
Network Information:
Client Address: ::ffff:10.10.20.24
Client Port: 49239
Additional Information:
Ticket Options: 0x40810010
Result Code: 0x0
Ticket Encryption Type: 0x12
Pre-Authentication Type: 2
Certificate Information:
Certificate Issuer Name:
Certificate Serial Number:
Certificate Thumbprint:
Certificate information is only provided if a certificate was used for pre-authentication.
Pre-authentication types, ticket options, encryption types and result codes are defined in RFC 4120.
Validation – Failure
When connecting over RDP, using the ip address of the server results in NTLM being used for authentication, which results in a failed authentication.
Log Name: Microsoft-Windows-Authentication/ProtectedUserFailures-DomainController
Source: Microsoft-Windows-NTLM
Date: 2/5/2018 10:50:23 PM
Event ID: 100
Task Category: None
Level: Error
Keywords:
User: SYSTEM
Computer: RootDC01.Litware.com
Description:
NTLM authentication failed because the account was a member of the Protected User group.
Account Name: BBanner
Device Name: ROOTMS01
Error Code: 0xC000006E
Log Name: Security
Source: Microsoft-Windows-Security-Auditing
Date: 2/5/2018 10:50:23 PM
Event ID: 4822
Task Category: Credential Validation
Level: Information
Keywords: Audit Failure
User: N/A
Computer: RootDC01.Litware.com
Description:
NTLM authentication failed because the account was a member of the Protected User group.
Account Name: BBanner
Device Name: ROOTMS01
Error Code: 0xC000006E
Log Name: Security
Source: Microsoft-Windows-Security-Auditing
Date: 2/5/2018 10:50:23 PM
Event ID: 4776
Task Category: Credential Validation
Level: Information
Keywords: Audit Failure
User: N/A
Computer: RootDC01.Litware.com
Description: The computer attempted to validate the credentials for an account.
Authentication Package: MICROSOFT_AUTHENTICATION_PACKAGE_V1_0
Logon Account: BBanner
Source Workstation: ROOTMS01
Error Code: 0xC000006E