Using Authentication Policies to Restrict Privileged User Account Logons
Authentication policy silos and the accompanying policies provide a way to contain high-privilege credentials to systems that are only pertinent to selected users, computers, or services. Silos can be defined and managed in Active Directory Domain Services (AD DS) by using the Active Directory Administrative Center and the Active Directory Windows PowerShell cmdlets.
The following example shows how to use authentication policies and authentication policy silos to allow privileged user accounts to log on ONLY to domain controllers and to privileged access workstations (also called jump servers, administrative servers/workstations, etc. The rationale is to restrict Tier 0 accounts to Tier 0 servers and not allow interactive logon to less secure machines. For more information on the tier model, see https://aka.ms/tiermodel
NoteMost examples on the internet use policies to:
|
Requirements
- Windows Server 2012 R2 domain functional level
- Clients must run Windows 8, Server 2012 and later to support Kerberos armoring (which is part of Dynamic Access Control)
High-level steps:
- Enable support for claims, compound authentication, and Kerberos armoring on domain controllers using group policy.
- Enable support for claims, compound authentication, and Kerberos armoring on clients using group policy.
- Create an authentication policy that configures the following:
- User accounts
- TGT lifetime for the user accounts
- Access control conditions that restrict devices
- Assign the authentication policy to each of the user accounts
Detailed steps:
| 1. | Configure domain controllers to support claims and compound authentication for Dynamic Access Control and Kerberos armoringDo this by enabling the following group policy setting and linking the group policy object to the domain controllers organizational unit:Computer Configuration\Policies\Administrative Templates\System\KDC - KDC support for claims, compound authentication, and Kerberos armoring: Always provide claims | 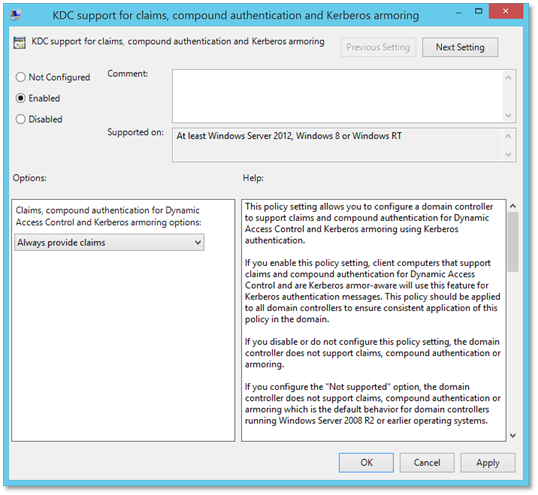 |
| 2. | Configure the client computers to request claims, provide information required to create compounded authentication and armor Kerberos messages.Do this by enabling the following group policy setting and linking the group policy object to the OUs that contain the machines to which the user(s) will be allowed to log on to:Computer Configuration\Policies\Administrative Templates\System\Kerberos - Kerberos client support for claims, compound authentication and Kerberos armoring | 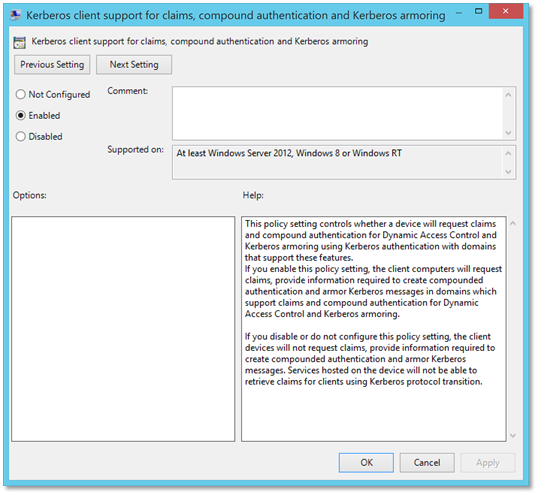 |
| 3. | Open the Active Directory Administrative Center (dsac.exe).Click on Authentication in the left pane.The selected Authentication node is visible for domains which are at Windows Server 2012 R2 DFL | 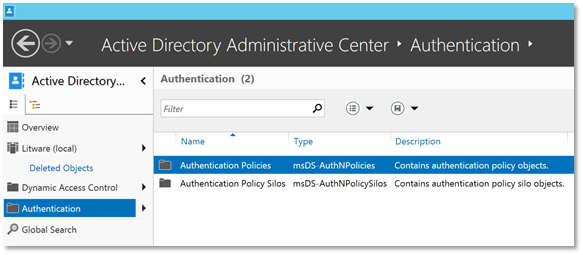 |
| 4. | In the main pane select Authentication Policies. Then, in the Tasks pane, click on New under Authentication Policies. Select Authentication Policy from the context menu. | 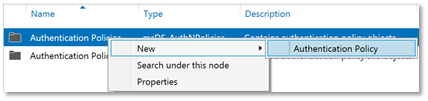 |
| 5. | Configure the policy with the following information:Display name: AuthPol - Tier_0_Accounts_DevicesDescription: This policy restricts directory service administrator accounts to authenticate against domain controllers and Privileged Administrative Workstations aloneOnly audit policy restrictions: Select for testing, before rolling out to productionProtect from accidental deletion: checked | 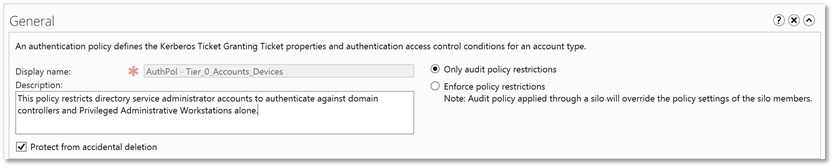 |
| 6. | Under the Accounts section, use the Add button to add the users. Group objects cannot be selected using the object picker. | 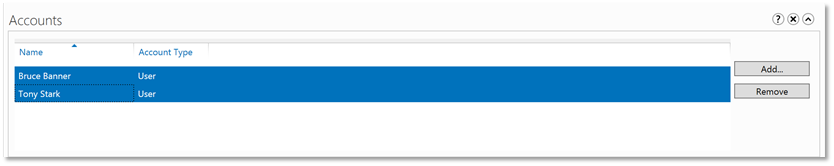 |
| 7. | Under the User section, check the box Specify a Ticket Granting Ticket lifetime for user accounts and enter a value in minutes for Ticket-Granting-Ticket Lifetime (minutes) | 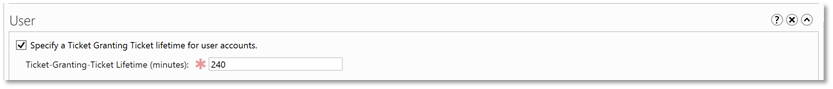 |
| 8. | Also, under the User section, specify access control conditions that restrict devices that can request a Ticket Granting Ticket for the user accounts assigned to this policy. | 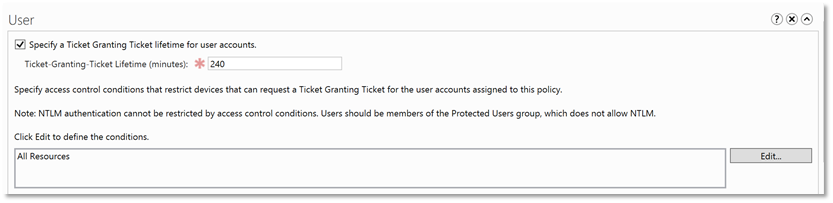 |
| 9. | Under the User section, click the Edit button. In the Edit Access Control Conditions window, click the Add a condition link on the bottom left corner. | 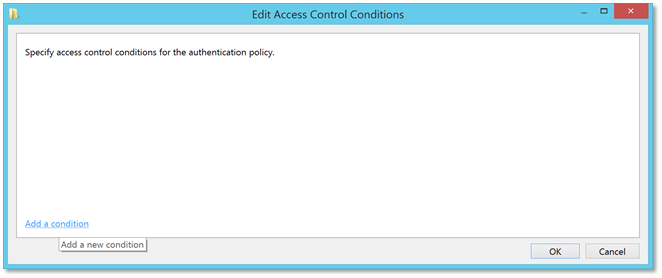 |
| 10. | In the Member of each drop-down box, select Member of any | 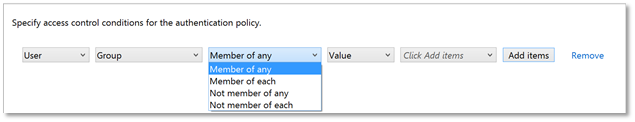 |
| 11. | Click the Add items button. Use the object picker to select the Domain Controllers security group. | 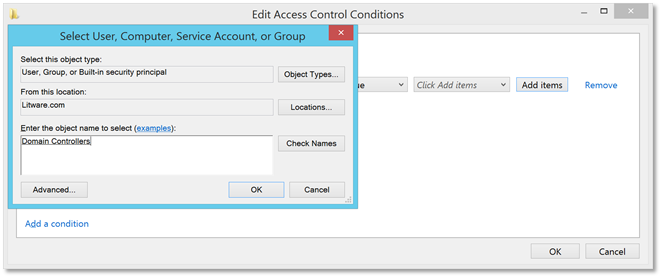 |
| 12. | Once again, click Add items and this time in the object picker, select the Computers object type as well. | 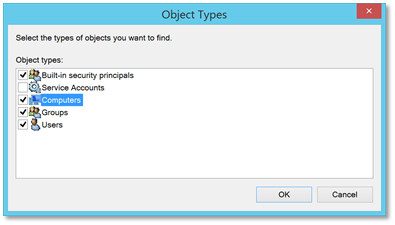 |
| 13. | Search and select the server(s) you want the user(s) to be able to log on to. | 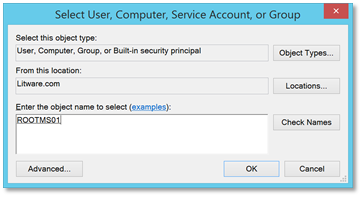 |
| 14. | This is what the result should look like in the Edit Access Control Conditions window: | 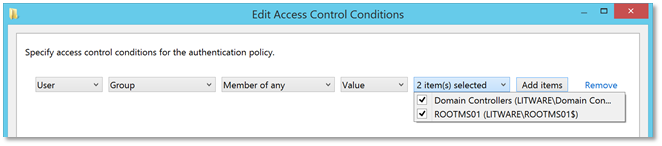 |
| 15. | This is what the result should look like in the User section of the authentication policy properties: | 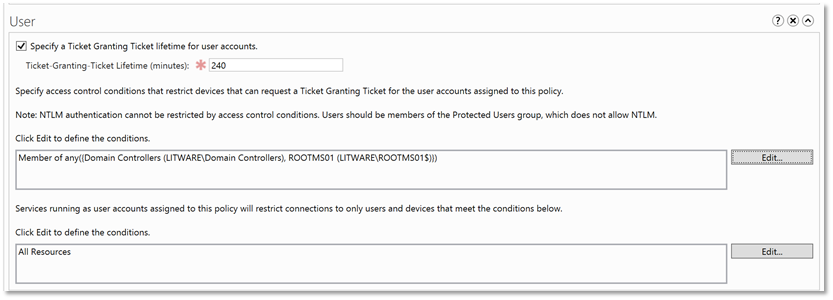 |
| 16. | Click OK on the authentication policy properties window.Within the Active Directory Administrative Center browse to the user account added in step 7, right-click the object and click Properties.Click Policy on the left and on the main pane, in the Authentication Policy section, select Assign Authentication Policy Silo and using the drop down, select the policy. | 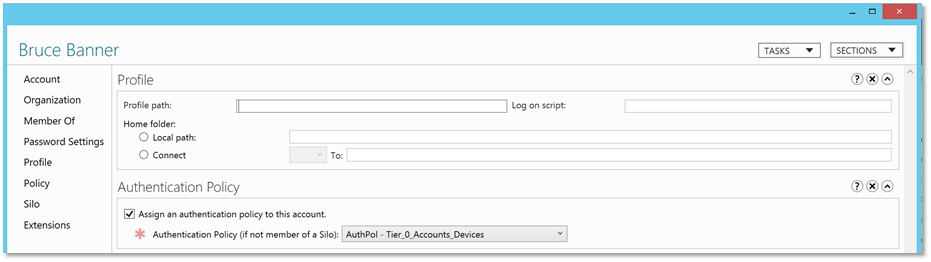 |
| 17. | Repeat the last step for each user account added in step 7. |
Validation – Failure
Audit Mode
When a user assigned an authentication policy attempts to log on to a machine to which he/she is not allowed access, the attempt succeeds but the following event is logged on the domain controller:
| Log Name: Microsoft-Windows-Authentication/AuthenticationPolicyFailures-DomainControllerSource: Microsoft-Windows-Kerberos-Key-Distribution-CenterDate: 2/5/2018 10:19:58 PMEvent ID: 305Task Category: NoneLevel: InformationKeywords: User: SYSTEMComputer: RootDC01.Litware.comDescription:A Kerberos ticket-granting-ticket (TGT) was issued, but it will be denied when Authentication Policy is enforced because the device does not meet the access control restrictions.Account Information:
Account Name: BBannerSupplied Realm Name:User ID: LITWARE\BBanner Authentication Policy Information:Silo Name:Policy Name: AuthPol - Tier_0_Accounts_DevicesTGT Lifetime: 240 Device Information:Device Name: Service Information:Service Name: krbtgt/LITWAREService ID: S-1-5-21-156393716-1274321063-4078162134-0 Network Information:Client Address: ::ffff:10.10.20.24Client Port: 49204 Additional Information:Ticket Options: 0x7BResult Code: 0x12Ticket Encryption Type: 0x7Pre-Authentication Type: 0 Certificate Information:Certificate Issuer Name:Certificate Serial Number:Certificate Thumbprint: Certificate information is only provided if a certificate was used for pre-authentication.Pre-authentication types, ticket options, encryption types and result codes are defined in RFC 4120. |
Enforced Mode
When a user assigned an authentication policy attempts to log on to a machine to which he/she is not allowed access, the attempt fails with the following error:
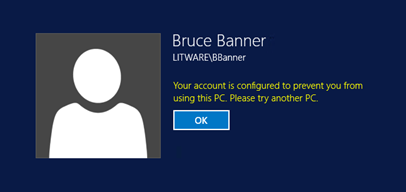
This is accompanied by the following events on the domain controller:
| Log Name: Microsoft-Windows-Authentication/AuthenticationPolicyFailures-DomainControllerSource: Microsoft-Windows-Kerberos-Key-Distribution-CenterDate: 2/5/2018 11:39:12 PMEvent ID: 105Task Category: NoneLevel: ErrorKeywords: User: SYSTEMComputer: RootDC01.Litware.comDescription:A Kerberos Ticket-granting-ticket (TGT) was denied because the device does not meet the access control restrictions.Account Information:
Account Name: BBannerSupplied Realm Name:User ID: LITWARE\BBanner Authentication Policy Information:Silo Name:Policy Name: AuthPol - Tier_0_Accounts_DevicesTGT Lifetime: 240 Device Information:Device Name: Service Information:Service Name: krbtgt/LITWAREService ID: S-1-5-21-156393716-1274321063-4078162134-0 Network Information:Client Address: ::ffff:10.10.20.24Client Port: 49218 Additional Information:Ticket Options: 0x78Result Code: 0xCTicket Encryption Type: 0x7Pre-Authentication Type: 0 Certificate Information:Certificate Issuer Name:Certificate Serial Number:Certificate Thumbprint: Certificate information is only provided if a certificate was used for pre-authentication.Pre-authentication types, ticket options, encryption types and result codes are defined in RFC 4120. |
| Log Name: SecuritySource: Microsoft-Windows-Security-AuditingDate: 2/5/2018 11:39:12 PMEvent ID: 4820Task Category: Kerberos Authentication ServiceLevel: InformationKeywords: Audit FailureUser: N/AComputer: RootDC01.Litware.comDescription:A Kerberos Ticket-granting-ticket (TGT) was denied because the device does not meet the access control restrictions.Account Information:
Account Name: BBannerSupplied Realm Name:User ID: LITWARE\BBanner Authentication Policy Information:Silo Name:Policy Name: AuthPol - Tier_0_Accounts_DevicesTGT Lifetime: 240 Device Information:Device Name: Service Information:Service Name: krbtgt/LITWAREService ID: S-1-5-21-156393716-1274321063-4078162134-0 Network Information:Client Address: ::ffff:10.10.20.24Client Port: 49218 Additional Information:Ticket Options: 0x78Result Code: 0xCTicket Encryption Type: 0x7Pre-Authentication Type: 0 Certificate Information:Certificate Issuer Name:Certificate Serial Number:Certificate Thumbprint: Certificate information is only provided if a certificate was used for pre-authentication.Pre-authentication types, ticket options, encryption types and result codes are defined in RFC 4120. |