Layers (Defense in Depth Part 1)
 If you have spent any time working with Network security, you are familiar with the concept of Defense in Depth. In a nutshell, there is NO SILVER BULLET when it comes to network or computer security. Network security is a process, and one where the threats and countermeasures are constantly evolving. Whenever I see posts saying that all an enterprise needs to do to become secure is to switch to Linux, or install a Firewall or IDS/IPS (or any other one-stop-answer) is uninformed at best, and irresponsible at worst.
If you have spent any time working with Network security, you are familiar with the concept of Defense in Depth. In a nutshell, there is NO SILVER BULLET when it comes to network or computer security. Network security is a process, and one where the threats and countermeasures are constantly evolving. Whenever I see posts saying that all an enterprise needs to do to become secure is to switch to Linux, or install a Firewall or IDS/IPS (or any other one-stop-answer) is uninformed at best, and irresponsible at worst.
There are any number of factors to consider when working to secure a network. There are physical security considerations, technological 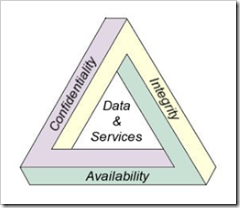 considerations, people considerations… Any basic security course or CISSP book will teach you about CIA, the magic triangle of Confidentiality, Integrity, and Availability (picture courtesy of Wikipedia). Having your company business plan available but not confidential, is a loss. Having your server locked down 6 ways from Sunday, but unavailable for use by authorized users, is a loss.
considerations, people considerations… Any basic security course or CISSP book will teach you about CIA, the magic triangle of Confidentiality, Integrity, and Availability (picture courtesy of Wikipedia). Having your company business plan available but not confidential, is a loss. Having your server locked down 6 ways from Sunday, but unavailable for use by authorized users, is a loss.
Writing an uber post that addresses all of these considerations would be rather cumbersome (for me to write, and for you to read), so I'll start off with my reply to an email that came through an internal Discussion List regarding one of the technologies Microsoft makes available to help with one particular threat vector. I will follow up this post with a series of posts covering the range of technologies, solutions, and processes used by Microsoft to address security. Security is a topic near and dear to my heart, so if you have any specific requests, put them in the comments and I will address them in future posts.
In any case, the question that came through the DL related to Windows Rights Management Services. RMS is a technology available for Windows Server 2003 that allows an organization to define who can open, modify, print, forward and/or take other actions with the information in a particular document. The threat that RMS primarily addresses is that if information disclosure. Sometimes confidential documents are leaked (either accidentally or intentionally), and can cause grave damage to a company. There is a great write-up on the purpose of (and limitations to) Information Rights Management (IRM) as implemented in Office 2007 here: https://office.microsoft.com/en-us/help/HA101029181033.aspx#1, and an in-depth article from Windows IT Pro magazine here: https://www.windowsitpro.com/Windows/Articles/ArticleID/48912/pg/1/1.html
The question (which was a fair one) stated that a customer had found that an RMS protected email with "forward" and "copy" permissions restricted could still be captured by using a third party screen capture utility, and pasted into other applications as an image. An earlier thread on the same subject carried the sensational headline of "RMS is crackable"
The question (and subject line), however, indicate a fundamental misunderstanding of the purpose and capabilities of RMS. The fact that an authorized end-user can take screenshots of an RMS protected document is expected behavior. Don't take that last sentence out of context…
RMS is a policy enforcement tool. The two main capabilities that an RMS enabled application provides are access control and user rights restrictions. Access control is the claim that users who do not have access to the protected content will not obtain access to it. This is a strong guarantee because a user who has no permissions to access the content will have to implement a successful cryptographic attack against AES.
In other words, someone who is not authorized to open the RMS document will not be able to do so (and therefore will not be able to use a 3rd party screen capture utility to screenshot the image and paste it into other applications).
Someone who IS authorized to open the document will always be able to use analog means to transcribe the contents. For example, RMS will not stop them from using a camera to take pictures of the screen, it will not stop an authorized user from calling someone on the telephone and reading them the contents, and it will not stop a 3rd party screen capture utility from taking screenshots of a document that the user is authorized to view.
RMS (and RMS-enabled applications such as Office 2007) will enforce the restrictions implemented by RMS (ie, the end-user will not be able to forward, or copy, or print…) as defined by the content owner. If you have an authorized user going through the effort needed to circumvent the policy restrictions placed on the document (that they are legitimately allowed to view), then you have a Human Resources problem, not a technical one... The efforts that the user will have gone to in order to circumvent the technical restrictions will usually show their disrespect for company policy and their intent to blatantly disregard it, and this will need to be addressed by management and HR policies. The end-user in question will not be able to say that they "accidentally" forwarded the company business plan to a competitor ;)
To quote part of the resolution to the email thread: RMS gives strong guarantees that people who do not have access to the content will not get it even if they have somehow obtained the documents. RMS enabled applications also provide user rights restrictions that keep the authorized users from disclosing information unintentionally.