Understanding and Remediating "PASSWD_NOTREQD"
In my previous post on querying the userAccountControl attribute, I noted one of the flags I want to ensure you understood was the PASSWD_NOTREQD or "Password Not Required" flag. As the name suggests, this flag allows you to have a fully functioning account with a blank password (even with a valid domain password policy in place).
In my time performing AD security assessments, I would estimate I've seen nearly 300,000 accounts with this flag set. Out of those accounts, I have only ever seen 5 unprivileged active accounts that had blank passwords set. So yes I want you to remediate the affected accounts, but even if a quick audit shows a large number of them present in your domains, it's probably not as bad as you think.
How does it happen?
This issue most commonly arises due to identity management systems that create accounts with the flag set, set a password but fail the last step of removing the flag. Our in-built tools such AD Users and Computers perform all the appropriate steps to remove the flag.
To actually have an enabled account with a blank password, the following things need to occur:
- You need to have PASSWD_NOTREQD enabled on your userAccountControl attribute and
- Have a password not set at creation time OR have privileged user exercise the "Reset-Password" security right and simply press enter on the password change prompt to grant the account a blank password.
So I have "X" amount of accounts in my report, can you tell me how many have blank passwords?
Not directly, there is no interface to query if an account has a blank password BUT if we try to remove the flag on an enabled account and the password is blank, we will get an error because the DC definitely knows it won't meet the password length/complexity requirements of your domain (its blank duh!)
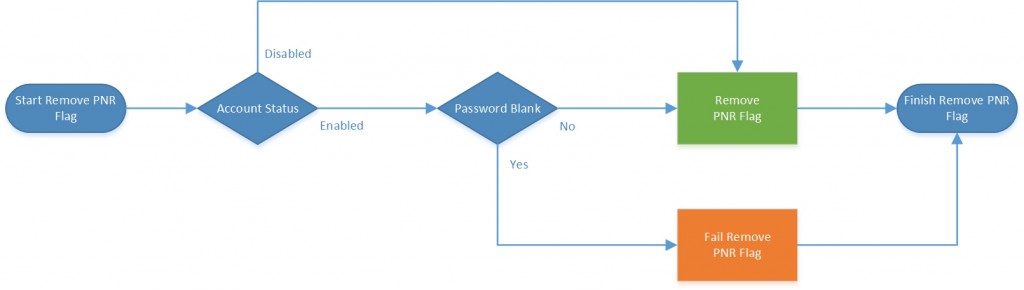
The following flow chart shows you the behavior that will occur when we try to remove the PNR flag from an account. The outcome depends on the current status of the account and if the current password is blank or not.
Cleanup Aisle 3
The following script can be used to help identify (again) and then attempt to remove the PASSWD_NOTREQD flag on all affected accounts. It will visually report the findings using Out-Grid then confirm if you want to proceed. Along with visual feedback, it will also export the affected accounts and reset status to a .CSV for further investigation.
# Report on Affected Accounts
$StatusLog = @()
Get-ADUser -Filter 'useraccountcontrol -band 32' -Properties "passwordnotrequired","useraccountcontrol","msDS-LastSuccessfulInteractiveLogonTime","lastLogonTimestamp" | Select-Object -Property DistinguishedName,Enabled,PasswordNotRequired,"msDS-LastSuccessfulInteractiveLogonTime","lastLogonTimestamp" | Out-GridView -Wait
# Attempt to remediate and log output
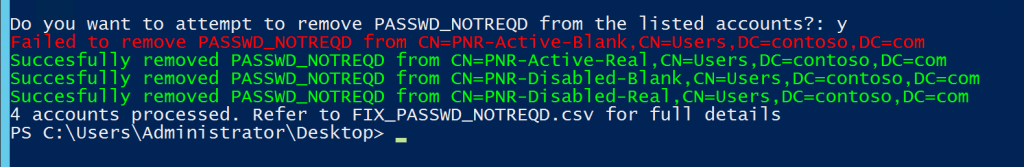
$Response = Read-Host "`nDo you want to attempt to remove PASSWD_NOTREQD from the listed accounts?"
If($Response.ToLower() -eq "y"){
ForEach ($Account in (Get-ADUser -Filter 'useraccountcontrol -band 32')){
$Status = "" | Select Status,Account
$Status.Account = $Account
Get-ADUser $Account | Set-ADUser -PasswordNotRequired $False -ErrorAction SilentlyContinue
If($?){
Write-Host "Succesfully removed PASSWD_NOTREQD from $Account" -ForeGroundColor Green
$Status.Status = "Success"
}
Else{
Write-Host "Failed to remove PASSWD_NOTREQD from $Account" -ForeGroundColor Red
$Status.Status = "Failure"
}
$StatusLog += $Status
}
}
Write-Host $StatusLog.Count "accounts processed. Refer to FIX_PASSWD_NOTREQD.csv for full details"
$StatusLog | Export-CSV -NoTypeInformation FIX_PASSWD_NOTREQD.csv
Final Words
So hopefully every identified account successfully has the PASSWD_NOTREQD flag removed and you feel a little easier knowing all of your user accounts have a password of some kind. If an account has failed (and you have permissions to modify it), there is a good chance it is both enabled and has a blank password. Press CTRL+ALT+DEL on domain member and try to login with a blank password.
Wait a few weeks after your initial clean-up and then check again. If any more accounts pop-up, you obviously have another system or operational process to remediate as well as some accounts to clean up.
Note: If any of the disabled accounts had a blank password, and your try to enable them in the future, you will receive an error saying the don't meet the password policy requirements. Simply set a password that meets requirements and then you will be able to enable it as expected.
If you find any blank passwords in your domains, let me know in the comments below.
Russ