Monitoring machines using Certificates with Operations Manager 2007 R2 - Part 1
In this series of two blogs, we will discuss about monitoring machines in non-trusted domain. In part one we will discuss about scenarios to use certificates and configuring certificate template for SCOM. In part two, we will talk about installation, approval of gateway servers and configuring monitoring for Workgroup machines.
Kerberos or Certificates
System Center Operations Manager 2007 R2 uses mutual authentication to communicate with agents. This can be done using Kerberos v5 or certificates. In case of same domain as that of SCOM server or if the two domains have two way trust we can use Kerberos. But if you want to monitor machines in workgroup or in non-trusted/one way trusted domain we need certificates. Certificates help in Mutual authentication.
Scenarios to used Certificates
If my SCOM server is in domain A and I want to monitor machines which are in Workgroup, I need Certificates. I will install Certificate on my SCOM server and on each workgroup machine that I want to monitor.
If my SCOM server is in domain A and I want to monitor machines in untrusted domain B, I will use certificates along with gateway server. But this time I don’t need to install certificate on all machines in domain B. I can simply install Gateway Server in domain B and have certificates installed on SCOM server of domain A and Gateway Server of domain B. Within Domain B, Kerberos is security mechanism between agents and Gateway server. And between gateway and SCOM server, certificates help for mutual authentication.
Another benefit of gateway servers is that I need to open only 1 port 5723 (TCP) between gateway and SCOM server.
We need name resolution between SCOM server and gateway server. This can be done using DNS, host files etc.
Let’s get it Started
I have installed Active Directory Certificate Services (AD CS) and Certificate Authority Web Enrollment roles on 2008 R2. Certificate Authority is of Enterprise type. More on 2008 R2 CA can be found here. Also to configure HTTPS binding for CA, check this.
Configuring certificate template for SCOM
1) On 2008 R2 Server, Click Start, then Administrative Tools and open Certification Authority snap-in. Click on Certificate templates, then on Manage.
2) Right Click on IPSec (offline request) template and select Duplicate Template option.
Select Windows Server 2003 Enterprise option for the version.
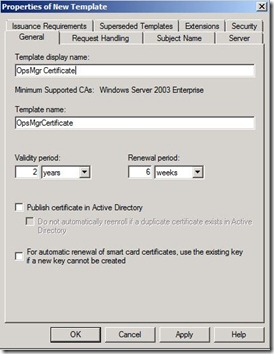
3) In Properties of new Template on General tab, give any name to template like OpsMgr Certificate using Template Display Name.
4) On request handling tab check Allow private key to be exported.
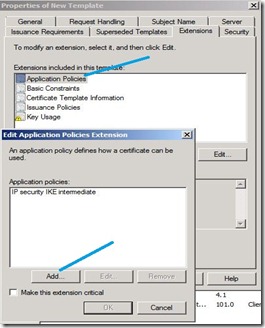
5) Click the Extensions tab, and in Extensions included in this template, click Application Policies, and then click Edit. In the Edit Application Policies Extension dialog box, click IP security IKE intermediate, and then click Remove.
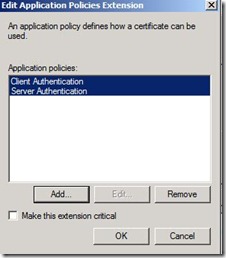
6) Click Add and then select Client Authentication and Server Authentication and click OK.
7) Click on Security tab and give Authenticated users Read and Enroll permissions.
8) Close the Certificate templates console.
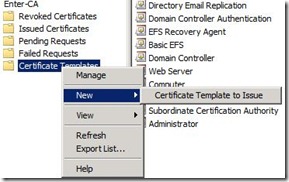
Add the configured templates to certificate templates folder
Right click Certificate templates in CA console. Click on New and then Certificate template to issue. Select the certificate template that we named in step 3.
This way we configure our certificate for SCOM. In part 2 we will discuss about installation of certificates, deployment of gateway server and monitoring WORKGROUP computers.
Stay Tuned!!