Security Intelligence Report: “Scareware” on the Raise
You know that we release our Security Intelligence Report twice an year: Today Version 6 is due.
Let me try to give you an overview of the “highlights” of the report from my point of view:
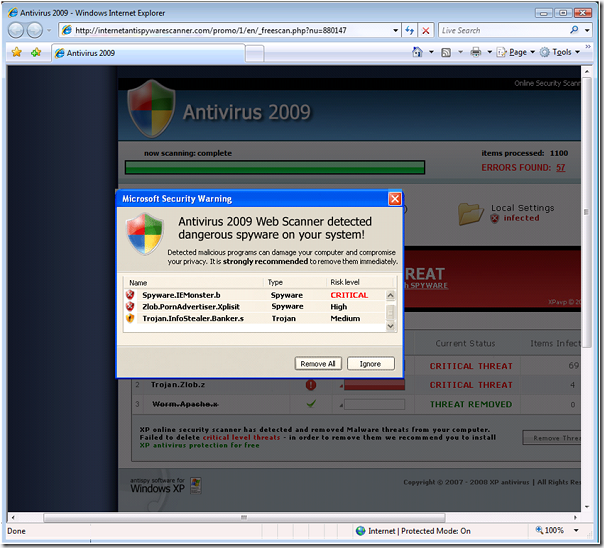
As I wrote in the title and as I blogged about this summer („Scareware“ on the Raise) one if the biggest growing threats we see is what I call “Scareware” or what we call in the report “Rogue Security Software”. I guess you know the feeling of visiting a website which then tells you that you are infected by malware and you should download a piece of software to protect you (or to clean your PC). Here you see a screenshot of how this can look like:
So, we have seen this growing over the last three periods and therefore we decided to feature a focus section on this growing threat.
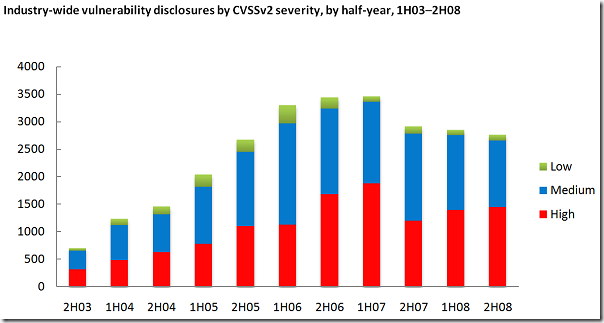
A standard topic in the report is about vulnerability disclosures. Here you find the chart you are used to if you read our Security Intelligence Report, my blog or heard me talking recently:
So, looking at the chart there is good and bad news:
- The good news is that vulnerability disclosures (industry-wide) is decreasing.
- However, there are still more than 2500 vulnerabilities per 6 months (to be clear again: this is the whole industry, not us)
- And, roughly 52% of all the vulnerabilities where high severity ones!
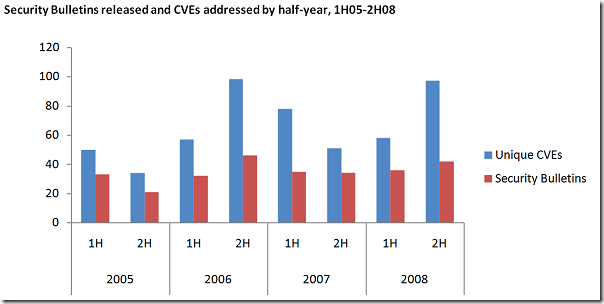
Looking at Microsoft’s vulnerabilities, this is the picture:
One thing I always mention, when I talk about this: If you are planning your Patch Management processes and you look at the figures above, make sure you cover your whole IT and not “just” Microsoft. In H2 2008 we had roughly 100 vulnerabilities out of 2500! So, think about patching the others as well (see 98% unpatched – and I am one of them :()
There are a few other charts in the report like the percentage of vulnerabilities responsibly disclosed or attacks on applications which I do not want to put in there (there has to be a reason you read the report J). But one thing I want to take up here as it was so important in H2, which is the PDF attacks as this underlines the statement I made above about Patch Management. Look at the exploits by months targeting Adobe Acrobat Reader:
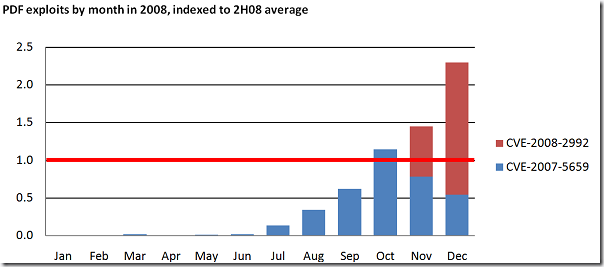
To be crystal clear with the graph above: This is not finger-pointing at Adobe. We were working closely together to address this and for both vulnerabilities there are updates available today. What I wanted to show you is that you have to extend your risk management to applications outside Microsoft.
Another standing set of graphs are world heatmaps. There are three of them in this Security Intelligence Report:
The “classic” malware infection rate based on the Malicious Software Removal Tool:
_thumb.jpg)
Even though we changed the way to determine where a computer is based (and therefore last report’s map cannot be compared with this one), EMEA does not look that bad. We have some challenges in the Middle East, Russias and – surprisingly to me – in Spain but the rest looks not great but ok.
But there is more. This time we look at the source of the malware based on infected websites and where they are hosted:
Here we have quite some green spots – which is good. It is interesting to see that Russia and Spain are red again here…
And last but not least the heatmap on where phishing sites are hosted:
If you take a different angle and look at it from a Windows perspective with regards to malware infection, it once more shows the progress we made with the different OSs:
This re-enforces the message I am delivering as often as possible: If I could give you one single advice from security person to security person (I am not measured on quota), this would be “stay on the latest version of your software – everywhere”. This includes Patch Management as well as Lifecycle management. Jus think about every piece of software you have (including embedded systems), think about when it was designed and then think about the threat landscape back then… Do you really have to think twice then?
If you want to hear Vinny Gullotto (General Manager, Microsoft Malware Protection Center) talk about the Security Intelligence Report, you can look at and interview he did with Tim Rains: Vinny and Tim show - SIR Volume 6 .
So, this and much more you can find in our Security Intelligence Report. Download it and have fun!
Roger
_thumb.jpg)
_thumb.jpg)
_thumb.jpg)