Securing My Infrastructure: Firewall
Well, this is a follow-up of my last posts about how I secure my environment. If you want to read the earlier posts of the series, see at the end of this post.
So, we did the Risk Assessment, now, let's look a little bit closer into my perimeter. Technically I have a "normal" ADSL connection with a static IP-address. However, I decided to use the provided modem only as a bridge and do the dial-up from my firewall, which is – surprise, surprise – an ISA Server2006. This enables me to avoid a NAT-NAT type of configuration and allows me as well to see what is going on on the outside adapter.
Looking at the classical design of a perimeter network, we travel through the world since quite some time and talk about the diminishing importance of the perimeter network or how Steve Riley puts it: "The death of the DMZ" – a concept I implemented in my network.
There are quite some services I am providing on my network to the Internet: I am running a Web Server, a Mail Server (which offers POP, SMTP, RPC over HTTPs, OWA, Exchange Active Sync) and I am exposing all my servers for RDP. Nevertheless I am not running a DMZ nor do I feel bad about it. The way I am working is to use the Reverse Proxy functionality of my firewall. If I would run the classical DMZ-design it is pretty likely that the second firewall would have a lot of ports open (I usually call this a "Router" J). In te setup I chose, I am able to use ISA as my bastion coming from the outside. It does a protocol filter as well as handles the entire authentication whenever a service is used, where I want to have authentication. Like that, nobody will hit my OWA server without being authenticated already. This is one of the big advantages of this setup. Additionally ISA looks into the data and tries to understand whether the packets are valid or not. So, if you send an SMTP command with a clearly invalid size, the packet will be dropped and will never reach my Exchange.
Last but not least, ISA serves as a cache. Initially I was wondering, whether I even should enable caching as we have so few users and enough bandwidth. Since ISA Server 2006 is able to cache Microsoft Update, it definitely makes sense. I configured the WSUS server in a way that the updates are downloaded directly from Microsoft Update. So, every computer in my network will access Microsoft Update and like that, the updates are cached as far as possible on the ISA Server.
Finally, let's have a look at monitoring. I am using System Center Operations Manager (SCOM) to monitor the environment and therefore ISA Server is reporting back to SCOM. Nevertheless the log shows interesting things from time to time:
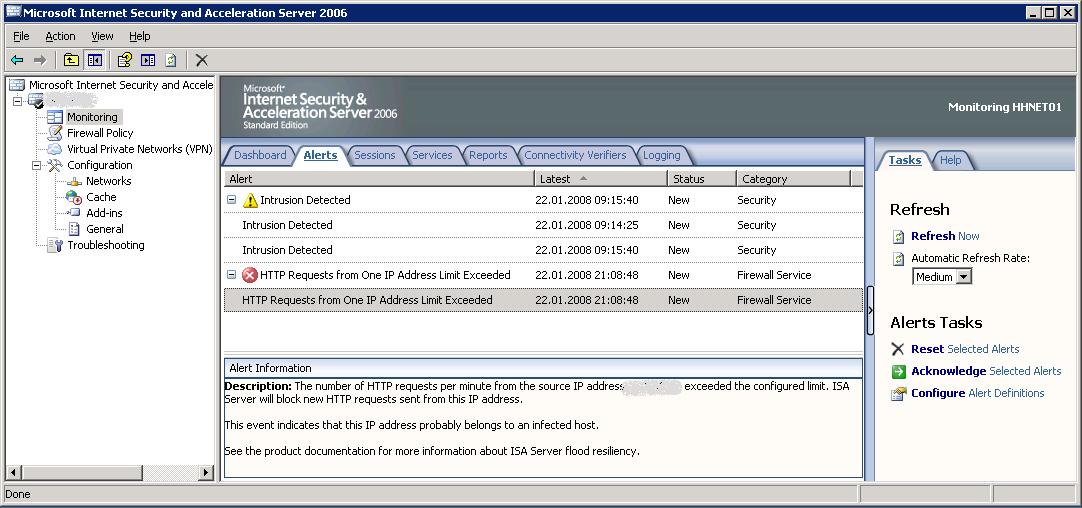
Recently one of the clients in the network got infected and started to send a lot of bogus traffic. ISA immediately closed the connection and alerted my SCOM (and Forefront cleaned the client):
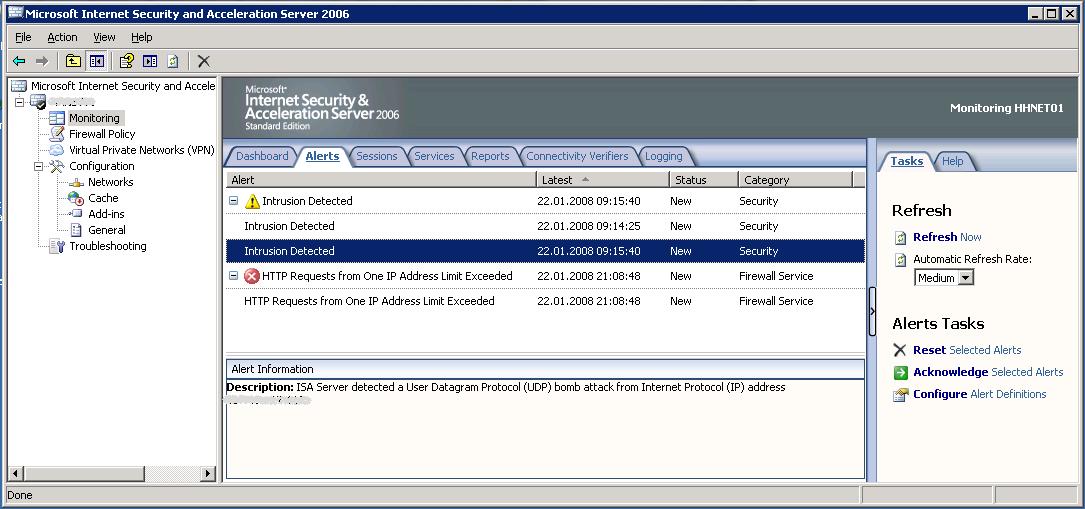
Things that happen really often are script kiddies looking at probing the firewall like that one (which actually came from the Netherlands):
So, this part up to now was pretty straight forward. However, there is one shortcoming (not of ISA but of other products like Office): As I stated above, I have one fixed IP address. From here I am running different domains (e.g. mail.contoso.com, vpn.contoso.com, www.contoso.com, …) where some of them need SSL. The ones of you knowing ISA and how it works realize that I need a listener, listening on port 443 and authenticating with a certificate taking the role for all the domains that request SSL– to which of the above mentioned names? Well, I issued a certificate with my CA to *.contoso.com. ISA can handle that pretty much without problems but some consuming devices like Outlook 2007 for RPC over HTTPS which fail to authenticate the server. There I had to disable the certificate check – something I would not like to do in production.
As always: If you have anything you would like me to answer, drop me a mail or a comment.
Roger
Other posts in this series:
- Securing My Infrastructure: Introduction
- Securing My Infrastructure: Introduction (part 2)
- Securing My Infrastructure: Risk Management
Additional Information